This post gives an overview of Edge Enterprise with Windows MAM, with the goal of protecting corporate data from being stored on personal unmanaged windows devices, and also the features that I feel are missing and hopefully to come from the solution.
By setting the following settings in Microsoft Intune you can achieve the following.
- Allow corporate Windows devices to continue to access data without restriction
- Block unmanaged personal Windows devices from accessing Corporate Office365 data from any apps apart from Microsoft Edge.
- Allow access to Office365 using personal unmanaged Windows devices through Microsoft Edge but restrict Downloads, Copy Paste and Print
Requirements
- Microsoft E3 Licensing – Intune
- Windows 10 or Windows 11 minimum 20h2
Setup
In Intune > Connectors and tokens > Mobile Threat Defense add the Windows Security Center Connector

In Devices > Enrollment > Enrollment Restrictions Windows MDM Personally Owned should be blocked otherwise your users can just join their device to Intune then they’ll be compliant and get around the point of this whole restriction

Conditional Access (2 policies will be created)
1st Conditional Access Policy (to block access using apps i.e office software on unmanaged Windows devices, and exclude corporate devices from policy)
Configure 1st conditional access with the following settings
Devices > Conditional Access
Give your policy a name and target it to a group (start small for testing)

For now we will just target Office365

In the conditions we will add
Device Platforms Windows


Client Apps
Mobile Apps and Desktop clients, Exchange Active Sync, Other Clients

Filter for devices Exclude Company devices

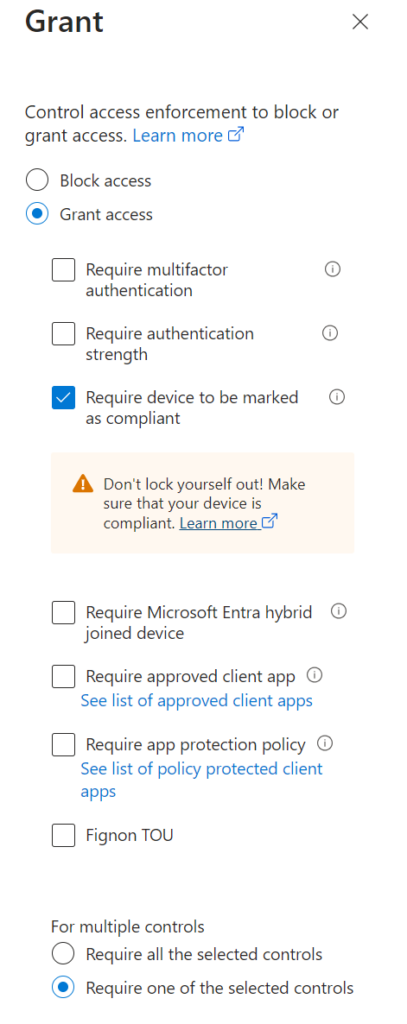
Grant

Grant Access to devices marked as compliant
Conditional Access Policy 2
2nd Conditional Access Policy (to allow access to Office365 using Edge on unmanaged Windows devices, and exclude corporate devices from policy)
Configure 2nd conditional access with the following settings
Give your 2nd policy a name and target it to the same group as 1st policy (start small for testing)

For now we will just target Office365

In the conditions we will add
Device Platforms Windows

Client Apps Browser

Filter for Company Devices Exclude Company owned

Require App Protection Policy Grant Access

Session see note below (not needed)

Note* Use Conditional Access App Control and Block Downloads (This may need Cloud App Security Licensing) in testing this setting seems to make no difference to MAM with Edge and you should not have to set it for all of this to work, Edge seems to still block downloads without it as the Application Management settings take care of all this.

Summary of Conditional Access
Policy 1 says a Windows device trying to connect to Office365 using apps i.e Office365 check if the device is compliant and if so allow access. The reason this policy works is you cannot become compliant on an ummanaged non MDM device, so you are effectively blocked from access
Policy 2 says grant access if using Edge and Edge has an app Protection policy so on entry Conditional Access will check for Edge and if the user has an app protection policy applied
Both Policy 1 and 2 exclude corporate devices so if you have for example an Intune device it should be seen as a company device and conditional access excludes the device from the policies altogether, and allows normal access.
App Protection Policy
Now we will set the App Protection Policy, as the policy above grants you access if you are using Edge and you have an App protection policy applied
Settings for the App protection policy
APPS > App Protection Policies > Create > Windows
Give your policy a name

Choose Microsoft Edge

These settings can be of your choosing the below is more restrictive not allowing copy and paste or sending data anywhere or printing

For the health checks its good to add disabled account as either block access or Wipe Data (Wipe data can ensure the edge session is removed if uer account is disabled in Azure
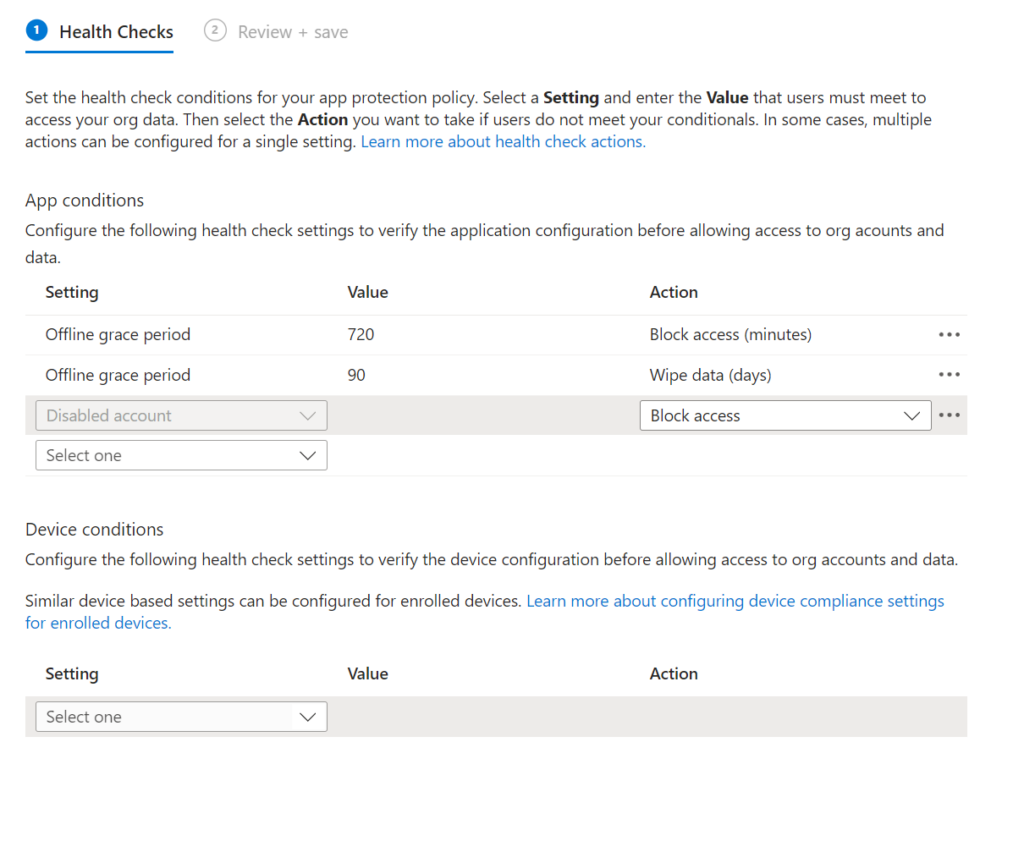
Again I’ve used the same user group the conditional access policies are pointed to

Result
Whilst the employees company device will work as normal without restriction the following should be seen on a non managed device
Scenario 1: Unmanaged Windows device attempting to Sign into Corporate Office Apps
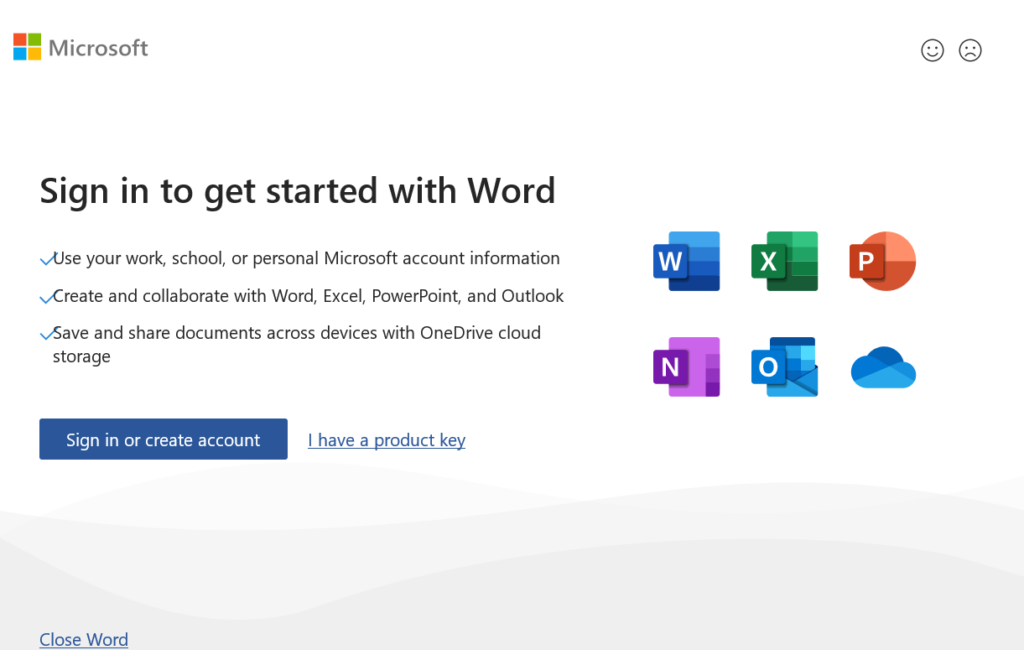
User is informed that their device is not compliant

Also for users who had already installed Office and were signed in on an unmanaged device they will lose access i.e Outlook will not be able to reconnect

Scenario 2: Using Edge on an unmanaged Windows device and attempting to sign into Corporate Office Account you are asked to switch Edge Profile

On first use you will get this popup ensure you untick allow org to manage my device (Microsoft really need to get rid of this)

User is warned that the access is monitored

In Office apps user is also warned they cant Download, Sync or Print

If user attempts to copy data they receive a block warning

Scenario 3: Attempt to login to corporate Office Account on a different browser, user recieves message they have to use edge

Verdict
Edge Enterprise and Conditional access combined offers good protection for DLP (Data loss prevention for Windows users) there are some competitors in this field in the last year or two, coming through with Enterprise Browsers Solutions, these include, names like Talon browser, Island browser, SURF and even Google who are constantly developing chrome enterprise to provide a locked down modified Chrome to help with DLP scenarios.
Wish list for Edge Enterprise with MAM
It will be interesting to see where Microsoft further develops Edge Enterprise with MAM, some of the features that will be nice to see are some of the restrictions available in Android and iOS MAM, i.e copy paste out to other corporate apps within the edge session, Copy paste character limits where you allow users to copy and paste a limited amount of data. Also I’d love to see Microsoft get rid of the Allow Organisation to manage my device screen, that’s been a hindrance for many years now.

The headsup (I think they call it) page with its “allow org to manage my device” trap:
Do you know a way to trigger this again?
If the device is not in entra/intune, what would re-trigger Edge or any windows app popping up with this again?
Basically, I am not seeing it anymore. I keep getting the “to access your service, app, or website, you may need to sign in to Microsoft Edge browser profile using stable.admin@tyhafan.org or register your device with Ty Hafan if you are already signed in.” and am going around in circles.
(Thanks for the MAM personal device restriction instruction at the top of this – hoping it takes a while to take and maybe that has fixed my problem)
Hi, interesting question, I’ll have a play with this, see if I can get this to re trigger in anyway, will let you know here