Defender Attack Surface Reduction is a good choice for USB restrictions, because it will report back to Defender and give a good audit if users are attempting to repeatedly write data out to external storage.
Setup
First create your groups for your different USB Groups, for my example I’ll create.
- Intune-USB-UserGroup-Block-RWE (Will be for blocking Read Write Execute)
- Intune-USB-UserGroup-Block-WE (Will Be for Blocking Write Execute (Read Allowed)
- Intune-USB-UserGroup-Allow-RWE (This will be users that are allowed full access)
Technically the Allow Group may not be needed in your scenario, as you’ll see further down, this may be useful in some circumstances, where you block all, and then keep a record of who you are allowing by also adding them to the allow group.

Important, or you will need to do this later, from each of your groups, open and copy the Object ID
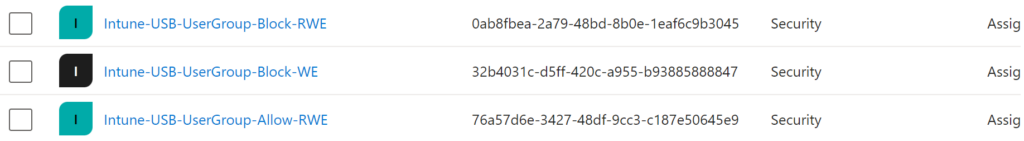
You can open each group and copy to clipboard the Object ID

Make a list of your Groups with their Object ID’s
I’ve noted them down in Notepad as we will need these Object ID’s for the policy

Now in Endpoint Security
Go to Attack Surface Reduction > Reusable Settings

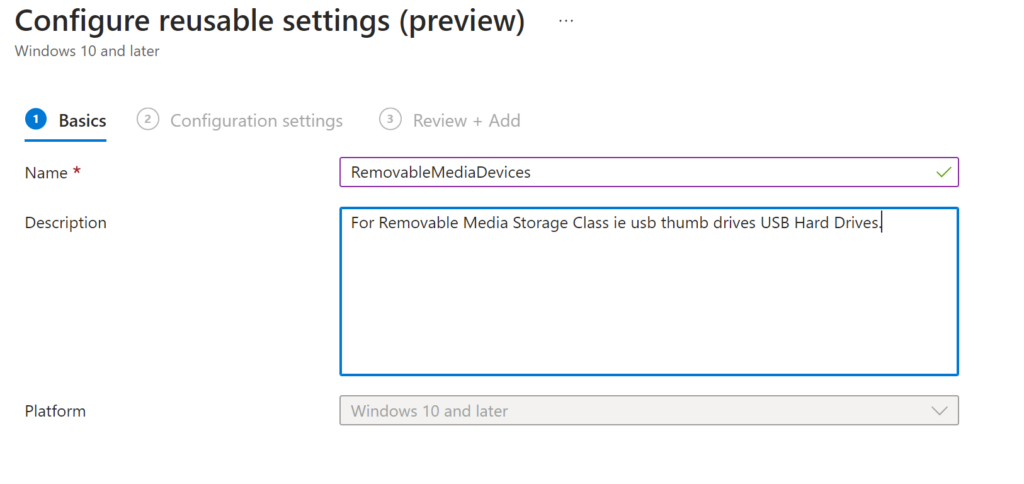
This is where we are going to add the type of USB Devices we want to block
Here I’m going to block USB Storage Drives i.e thumb drives, USB Hard Drives etc
So name your reusable setting (can be whatever name makes sense to you)
Add > Removable Storage
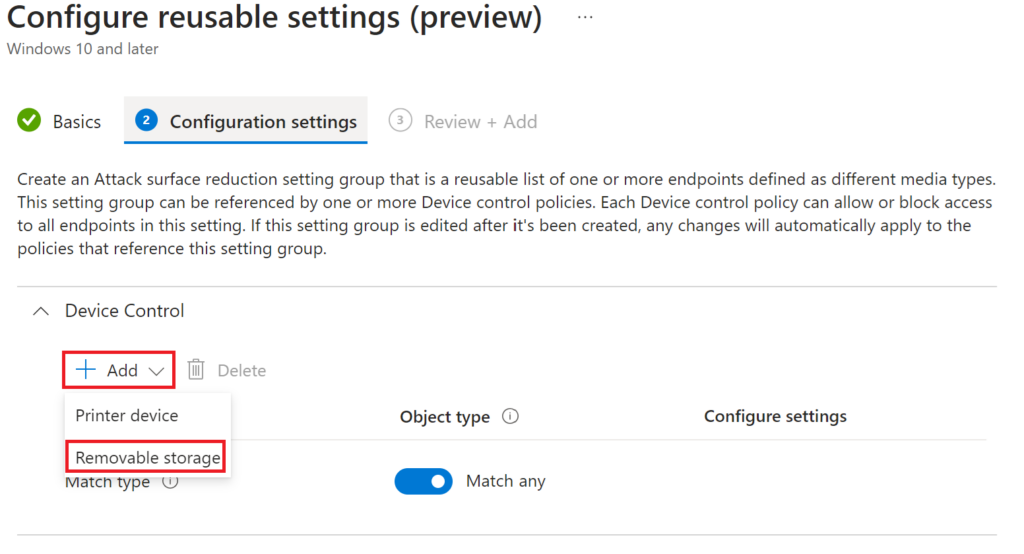
Edit instance

On the Edit Instance Page we enter the PrimaryID and give it a name PrimaryID is very important, see below, name can be of your choosing

ensure the PrimaryID is one of the below depending on what you want to block in our case we want to block removable media so the primaryid will be RemovableMediaDevices
- RemovableMediaDevices
- CdRomDevices
- WpdDevices
- PrinterDevices
The reason is these ID’s come from the CSP ./Device/Vendor/MSFT/Defender/Configuration/SecuredDevicesConfiguration
Defender CSP | Microsoft Learn

Save click Next and Add
The reusable setting is now created for Removable storage and you may note that its not yet assigned to a policy which we create next

Click on summary and click Create policy

From the drop down choose
Win 10 – 11 and Server and Device Control and click Create

I’ve called my Policy Removable Media Access and put in a description

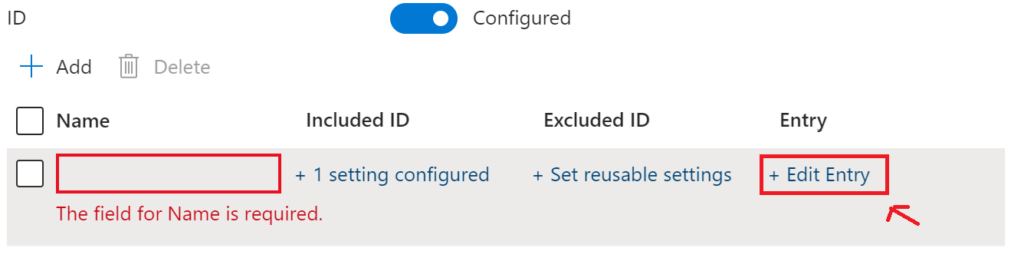
Scroll to the the bottom of the policy and the first thing we will do is add our reusable setting we just created

Select RemovableMediaDevices from Setting Group, then click Select

This will now change to 1 setting Configured

Now click Edit Entry
Name your Policy and if you like add a description
First I’m going to add my allow RWE Rules and Group

In the Access mask I’ve chosen

And In Audit Allowed I’ve chose to Send Event, this way at least Security can audit events if needed
Now we add the others
This time we add the Deny Write And Execute (So Im not denying Read) and Ive added the group Object for that.
In the Audit for Deny I’m sending Notification and Event the Notification will give the user a quick toast notification to say they are denied access if they trigger it by trying to read a blocked action
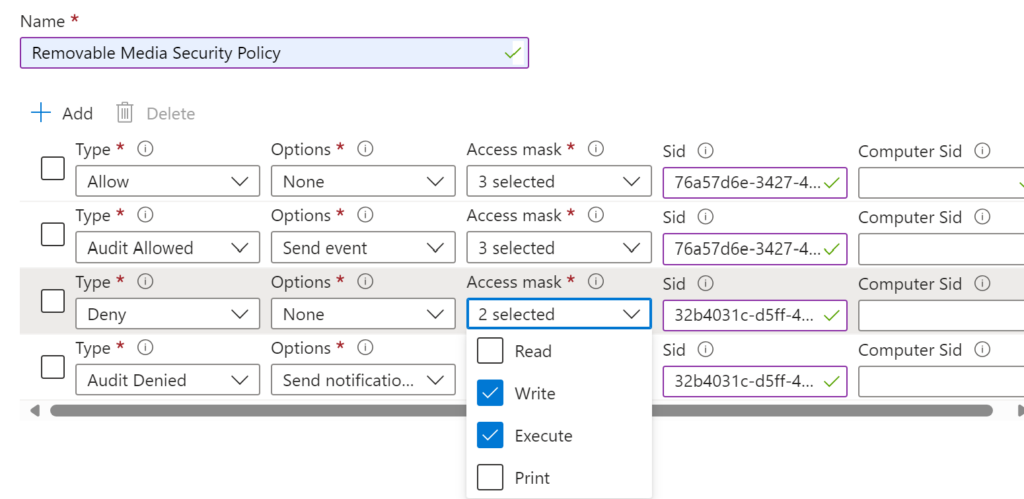
Finally my Deny All Rule

ASSIGNING THE WHOLE POLICY TO A SEPARATE GROUP
Click Ok and you can now Assign it, you can assign it to ALL USERS or a USER Group you want —
Why?, if I assign it to all users will it block all? No because the user must also be in one of the groups in the Sid (Object ID) rules for it to apply any of the block or allow rules
If you want to do some testing first an play it very safe create a test user group to test out the policies
At the moment as long as all the rules have a corresponding Group SID (Object ID) nothing will change for the user till the user is put into one of the corresponding Groups

Now to test out the policies I add a user account to….. Intune-USB-UserGroup-Block-RWE
You will find you now need to reboot or easier still log off and log on again for the change to take effect, as it needs to read the User group as you login
Plug USB in and……

Attempt to open drive

If you open Powershell and do Get-MpComputerStatus
You can see if your policy has been updated, and when, typically it will happen on any login or reboot also every time policy pushes but this can be many hours

Also note the DefaultAllow this helps in our situation because for example here is a scenario…
Your whole company will be blocked from removable storage use but you know that there will be cases where users will need to be allowed
You can leave the user in the Intune-USB-UserGroup-Block-RWE and now for say a period of time add the user additionally to the allow Group as well Intune-USB-UserGroup-Allow-RWE
The user after log off log on will now have access to USB removable media again
Why, will it not clash with the block?
Because Default allow is on it will read down the list and see which groups the user is in and allow from our policy

(All users are in the All Users Group I deployed the complete policy to)

Where I had trouble rolling out in a typical way
I also tried rolling the whole thing out in another way which is
Deploy the whole policy to the Deny group and turn off the deny Sid rule in the policy i.e
This kind of works, for example the whole policy is pushed assigned to the Deny RWE Group and as there is no Object ID for deny thats the default rule HOWEVER I kept getting intermittent issues when adding to the allow groups I get the feeling (also semi confirmed by my chats with Microsoft) that this is because of this — when you hover over Sid in the policy you will see this note

So to sum up this is what has worked 100% for me
Deploy the complete policy to a seperate user group of your choosing but the policy itself will do nothing until the User is in one of the SID Groups that are separate and defined in the SID rules
Notes
Look in HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender\Policy Manager\ to see your restrictions applying
MDE Device Control – Leveraging Reusable Settings in Intune – Microsoft Community Hub
Device control walkthroughs – Microsoft Defender for Endpoint | Microsoft Learn

Great post – will be trying this out Tim. Thanks for the write up
Thanks Carl and thank you for the great info on PrimaryID’s, I’ve now added a little more info around these.
Very information and detailed post. would you please clarify if the same can be applied on device group instead of user group?
Hi yes device groups seem to work ok too
Thank Tim for your response.
I am following your guidance to apply the same kind of settings on Computer objects but its not working as expected specially for Read only and Read-Write
Just to heads up my configuration
Grp_DeviceControl_F VM01 TrendMicro USB (Full)
Grp_DeviceControl_R VM02 SanDisk USB (Read-only)
Grp_DeviceControl_RW VM03 KingSton USB (Read Write)
ASR Policy > Default Block – All USB but Allow only Approved
4 x Reusable settings to allow match any
Rule order
Full Access > Allow & Allow Audit > TrendMicro USB > Read, Write, Execute, Print
Read-only Access > Allow & Allow Audit > SanDisk USB > Read, Execute
Read-Write Access > Allow & Allow Audit > KingSton USB > Read, Write, Execute
Deny All > Deny & Deny Audit and Notification > Read, Write, Execute, Print
Behavior
Working scenario >>> VM01 can access TrendMicro USB (Full), but denied all others
NON Working scenario >>> VM02 & VM03 can NOT access SanDisk USB (Read Execute) & KingSton USB (Read Write)
Appreciated your kind advise/suggestion to identify the cause.
Just to clarify, i am using three different USB to control per device group under single device control policy
Ok this is weird, I’ll try to set up a similar scenario in my environment, and see what I get
That would be great. Thanks for your effort.