For quite some I’ve been considering writing about Microsoft’s Strong Mapping changes to certificates
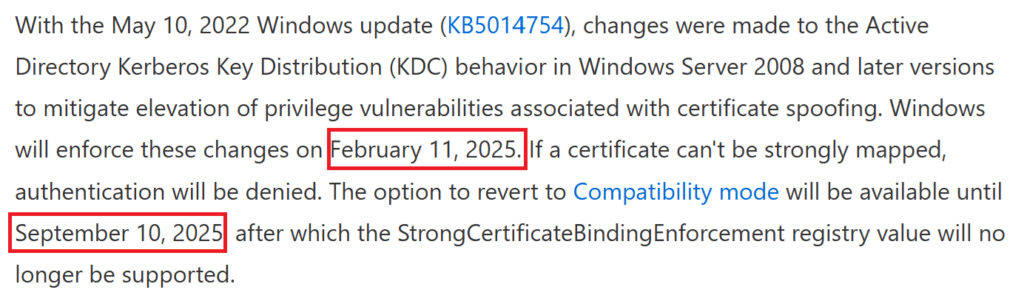
With the first enforced changes via Patch Tuesday just around the corner (Feb 11 2025), I felt compelled to share my insights that might help the community navigate the transition.
I will not cover too much on the basics as so much info is available on Microsoft’s and other posts about Strong Mapping.
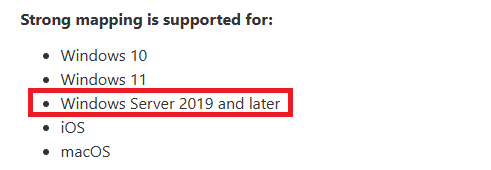
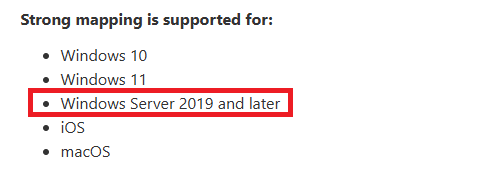
Requirements for Strong Mapping (Note 2019 Server on DC’s)
Note the requirement for 2019 Server, although not well documented the fact is Intune or Jamf for Mac (Offline Certs) through things like NDES only will be seen as strong mapped if your DC’s are 2019 and above, I have tested this on 2016 and although the certificates have strong mapping they fail to be seen as such and the DC still gives Warning that it cant see the mapping. Switch the user to authenticate the cert on 2019 or above it works and passes Authentication. The same is not true of On premise (Online certs anything above 2008r2 is ok for these) So if you are using say Intune NDES you are going to need to upgrade your DC’s
Timeline
May 2022 – Initial strong mapping changes, Certificate templates automatically got a new attribute and Domain controllers could give us Event 39 so we could know what certs are not seen strong mapped.
September 2024 – Microsoft gave the ability to add strong map in Intune (However 2016 DC’s cannot read the URL tag it uses, more on this in troubleshooting section below below)
Jan 2025 – Apple management system Jamf gave advice KB’s on adding strong mapping for Apple Certs
Feb 2025 – (was going to be November 2023 but delayed) Microsoft will push domain controllers to Full enforcement via Patch Tuesday Feb 2025 unless a reg key is added (KDC reg Key StrongCertificateBindingEnforcement on DC’s)
Sept 2025 – Full enforcement, doesn’t matter if you have regkeys in place, they will be ignored, so you must aim to be fully ready with strong mapped certs and no warnings on your DC events by this date.
What is Certificate Strong Mapping ?
A strong mapped certificate refers to a certificate that has been securely linked to a user or device in a way that ensures robust validation during certificate-based authentication. This involves using identifiers that are unique and cannot be reused, such as a Security Identifier (SID) or a specific serial number.
In Windows environments, strong mapping is crucial for preventing spoofing and ensuring that the certificate presented during authentication genuinely belongs to the user or device it claims to represent.
(You will notice once strong mapping is setup, where devices and or users are synced from Active Directory to Azure Entra AD the certificate will contain an on-premise identity. i.e a user cert that is strong mapped will have a User SID that matches the users SID onpremise thus making it hard to spoof)
Is my environment affected?
The easiest way to tell if your environment is to check your Domain Controllers for Event ID 39 , The event will show for each and every cert it finds where the user or device is not seen as strong mapped.
Go to the check my site part of the post for more diagnostics
Different scenarios for likelihood of having to take action
Scenario 1
Completely On premise devices / users – (Certificates probably already mapped)
In May 2022 Microsoft Monthly Update (KB5014754) automatically added an extra extension to certificates authority templates OID 1.3.6.1.4.1.311.25.2
Once that update was applied any certs that were due to renewal or any new templates or certs should contain the extension thus making them strong mapped. Unless you had certs with an extremely long expiry set and your devices or users have not updated their certs, if you are in this scenario and completely on premise you should be ok, unless you have not applied patches since, 2022 or your certs need renewing for devices or users as they had a 5 year validity or similar.
OID 1.3.6.1.4.1.311.25.2 (was added to certs 2022)

Check your DC events anyway and see if you have issues (steps for this outlined below)
Scenario 2
Intune environment where Users sync from On-premise i.e via AAD Connect and you are deploying certs via NDES through Intune, devices are AAD Joined Intune. (Certificates likely need mapping)
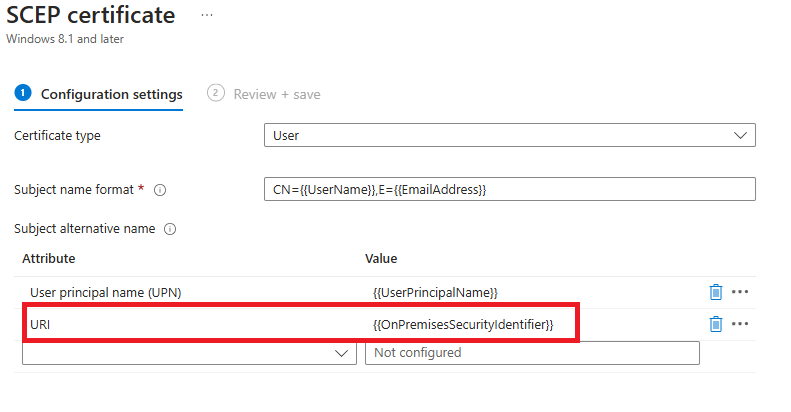
In September 2024 Microsoft added the ability to add strong mapping to Offline Certificates , i.e through Intune and NDES. You can now add the below attribute to your certificate templates within Intune
Attribute – URI Value – {{OnPremisesSecurityIdentifier}}
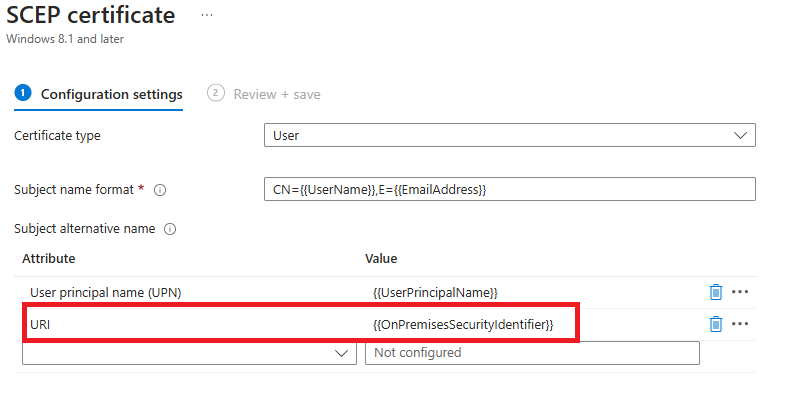
Once the user receives the new certificate or it gets renewed it will be strong mapped. The certificate will show the the new attribute tag in the cert under subject Alternative name, the URL Tag will match the users SID in AD
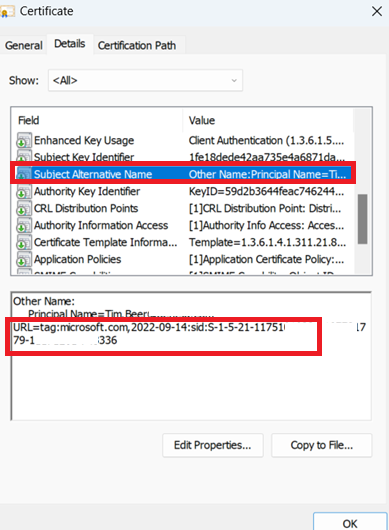
***A big note on this is your Domain Controllers need to be 2019 or above to accept strong mapping in (Offline) Intune certificates) ***
Scenario 3
Intune Entra hybrid joined devices where device certificates are Offline (i.e NDES Intune supplied certificates) (Certificates likely need mapping)
Same as above, for your device certificates add the Attribute – URI Value – {{OnPremisesSecurityIdentifier}} to your Device certificates in Intune and it should then match the SID of the Device in on premises AD, again you will need to redeploy or renew certificates.
Workaround for February 2025
So you may be here like many where there has been no preparation for this, or the February 2025 patch Tuesday has just been deployed to your DC’s and your users can no longer login to wifi or VPN as certs are getting rejected .
Deploy the KDC regkey to your DC’s to keep logging events to dc’s but ignoring the fact that certs are not strong mapped
You could either deploy the regkey via GPO or Script , maybe even via SCCM (MECM)
Group policy – maybe preferable if you are deploying this before Feb 2025 patch Tuesday or its your preferred deployment mechanism
deploy key HKLM:\System\CurrentControlSet\Services\KDC StrongCertificateBindingEnforcement Dword Value = 1
Or you could deploy the regkey with script via SCCM (MECM) or even a a compliance remediation
#KDC RegKey for Feb2025
$CheckKeyExists = (Get-ItemProperty "HKLM:\System\CurrentControlSet\Services\KDC" -Name "StrongCertificateBindingEnforcement" -ErrorAction SilentlyContinue)
If ($CheckKeyExists -eq $Null) {
New-ItemProperty -Path "HKLM:\System\CurrentControlSet\Services\KDC" -Name "StrongCertificateBindingEnforcement" -PropertyType DWORD -Value "1" -Force | Out-Null
$Output = "Added Key"
} Else {
If ($CheckKeyExists.StrongCertificateBindingEnforcement -ne 1) {
Set-ItemProperty -Path "HKLM:\System\CurrentControlSet\Services\KDC" -Name "StrongCertificateBindingEnforcement" -Value "1" -Force
$Output = "Updated Key to 1"
} Else {
$Output = "Key Already Existed With correct setting - Skipping"
}
}
Return $Output
You now have till September 2025 to get Strong mapping working
Getting Strong Mapping Working
Step 1) Getting the current state of your environment
If you are right at the beginning of this journey here’s some useful steps for you to gather information
The Most Important step – Getting the events from your DC’s
Since 2022 Microsoft added events to your DC’s to display whether your DC’s are currently finding certificates that are not strong mapped – if this is the case its likely that they are warning events instead of error events, With the February 2025 Patch update these events will turn from Warning to an error, and the authentication will be denied.
Event 39
The most likely event if you are using NDES and Intune and haven’t done anything about Strong Mapping is Event 39 (Event 41 if you are using 2008 R2 for DC’s)
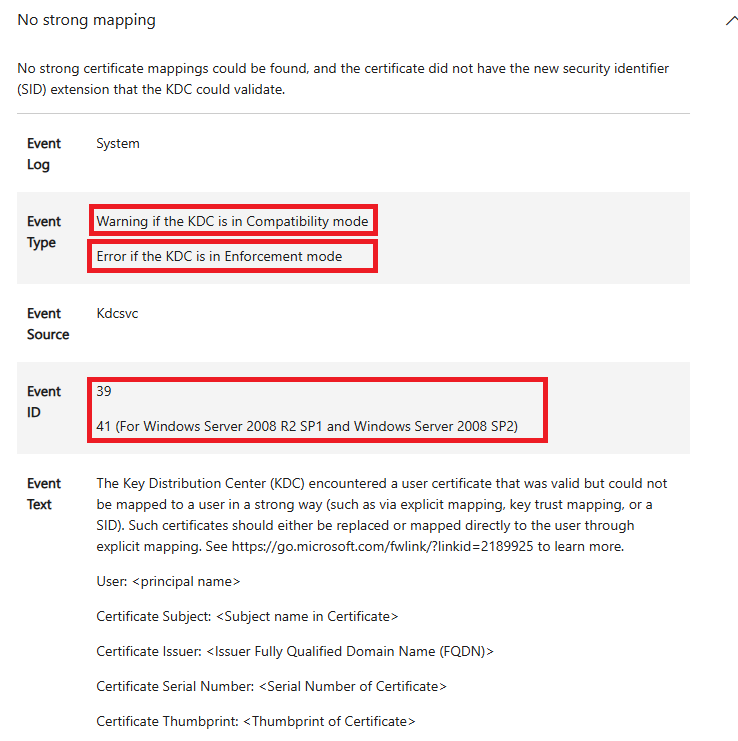
If you have one or 2 DC’s you can login and go to System Events and filter by EventID
Powershell find Event 39 on your DC’s
You can also run a powershell Script to search for Event ID 39
Get-EventLog -LogName System |
Where-Object {
$_.EventID -eq 39
} |
Sort-Object -Property TimeGenerated |
Select-Object -Last 30 |
Format-Table -AutoSize -Wrap
My favored way is to use CMPIVOT in SCCM (MECM)
I’m running a CMPivot to look for last 12hours of error 39 against all DC’s
WinEvent(‘System’, 12h) | where ID == 39

Looking at the event first thing you may notice is the event is a “Warning” this would change to “Error” if Feb 2025 Patch Tuesday has applied to your DC’s – Setting the Regkey for KDC in the workaround again will set this back to warning
If you look further into the event details from CMPivot you can take the Serial Number from the cert and see why its failing
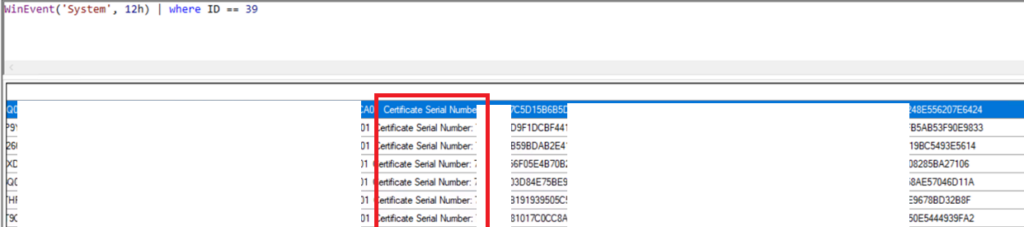
If I now go to my Certificate Authority server and search by filtering for a serial number
On View Filter by Serial Number and enter one of the serial numbers
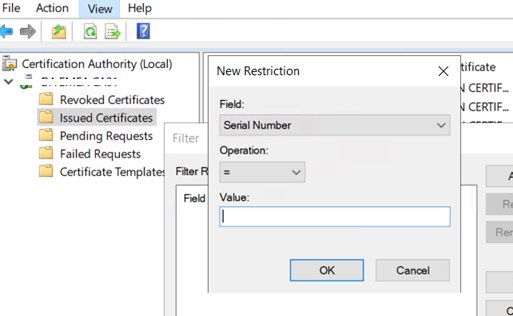
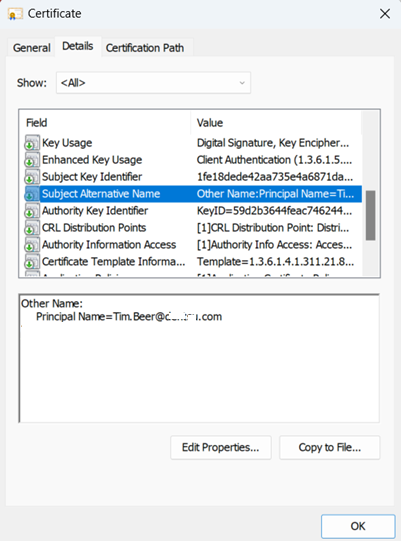
And here’s the cert this will fail as it has no URL tag in the Subject Alternative name
Remember – For Strong mapping to work it needs the new Microsoft Tag which is mapping your on prem details
Step 2) Readying and deploying new Intune Certs with strong mapping
You are likely in the scenario where you currently have non strong mapped certificates deployed to users and or devices and you now need to swap them out for strong mapped certs
Important — information, I’ve read from some forums is that just adding the change to the current certificates Attribute – URI Value – {{OnPremisesSecurityIdentifier}} will just redeploy it automatically and overwrite the old, I’ve tested this in 2 environments and even tried other changes to certs and it has not automatically deployed again, but people in forums are saying this works, will test again and update this.
Here is what I’ve done in different environments either way seems to work as a more gradual rollout, though you may find the above works ok
Deployment Solution Option 1 (Preferable)
If you are happy with your current certs, as in they have always worked apart from not being strong mapped —
- Create a new cert in Intune with all the same attributes as your old certs but add the new attribute for OnPremisesSecurityIdentifier
2. Create a new Group to deploy this new cert to, I’m going to call this group Strong Mapped Cert Deployment
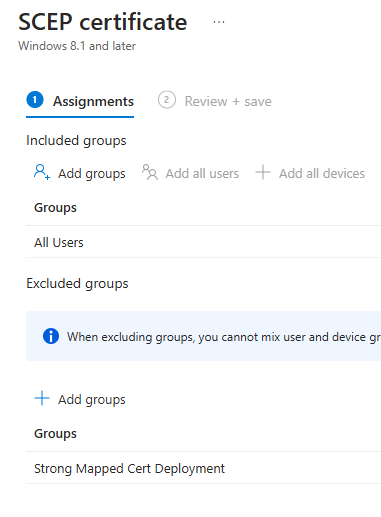
3. Deploy this new cert with the strong mapping to a new group, we don’t need to put users in the group yet
4. Original cert (non strong mapped ) deployment, exclude this new group
i.e lets suppose Original non strong mapped cert is deployed to All Users
ORIGINAL NOT STRONG MAPPED CERTIFICATE
Deployed to all Users currently – and now I’ve added the excluded new group below, this excluded new group is where I’m deploying the new cert to.
5. Now slowly and at first very slowly add users to the new Group Strong Mapped Cert Deployment
Its best to add some test users in to your new deployment group first and upon next device sync it should pull down the new cert and remove the old.
Deployment Solution Option 2
Another option that seems to work
- Add the new attribute to your current non strong mapped cert
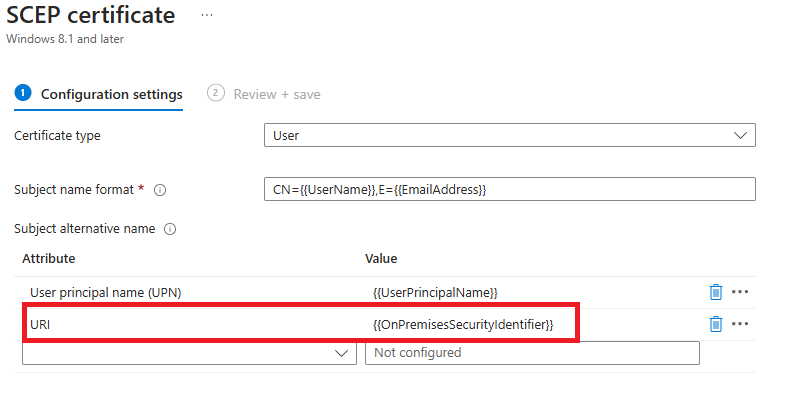
2. Change the current renewal threshold to a higher number — example lets go from 20% to 30%
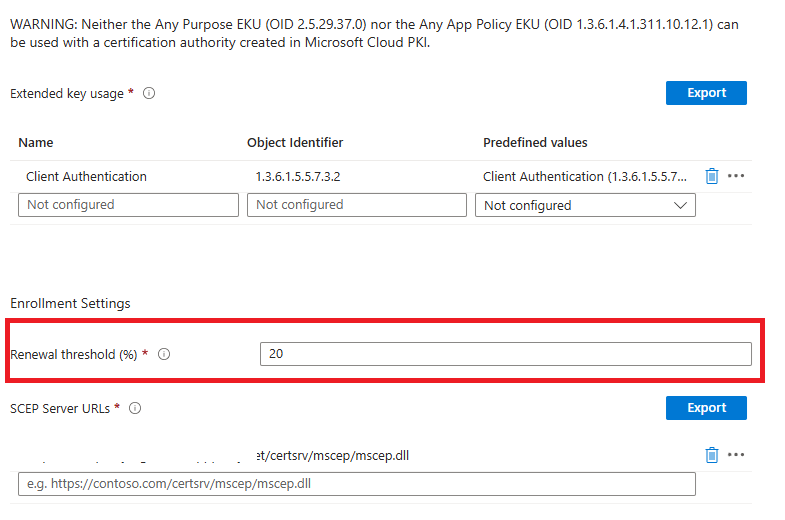
3. Keep changing the renewal threshold say every 1 to 2 days gradually till you get to say 98% –100%
This should gradually then replace everyone’s certificate for the same template but with the strong mapping in it
***EITHER WAY YOU DO THIS ESPECIALLY IN LARGE ENVIRONMENTS ROLL OUT VERY GRADUALLY, YOU CAN FLOOD YOUR CERT SERVERS WITH REQUESTS AND YOU CAN END UP WITH USERS NOT BEING ABLE TO CONNECT TO WIFI / VPN AS THEY HAVENT GOT THE NEW CERT DUE TO BOTTLENECKS OF LARGE NUMBERS OF REQUESTS***
Troubleshooting
My Intune configuration is set to strong map, I can see strong mapping sid’s in the certificates but I’m still getting error 39, what‘s wrong?
Are your Domain Controllers 2019 and above? 2016 DC’s or below do not support the new OnPremisesSecurityIdentifier, so they work fine for On premises certs as they read the OID mapping OK, but not the offline way in Intune, with OnPremisesSecurityIdentifier, you will need to upgrade your DC’s, this is true also in a mixed environment. You will see where your Users hit a 2019 or above DC they will be accepted with no error 39, where as the same user hits a 2016 or below DC it will still error There is only the smallest hint of this being documented by Microsoft in the document below, under testing I have found this to be true that you really do need 2019 and above.
Support tip: Implementing strong mapping in Microsoft Intune certificates | Microsoft Community Hub
Useful Articles
Richard Hicks all round cert and auth guru
Strong Certificate Mapping for Intune PKCS and SCEP Certificates | Richard M. Hicks Consulting, Inc.
Strong Certificate Mapping Enforcement February 2025 | Richard M. Hicks Consulting, Inc.
Microsoft
Support tip: Implementing strong mapping in Microsoft Intune certificates | Microsoft Community Hub
Apple Jamf

Hi, in a scenario where DCs are not patched immediately (2 weeks deferral) the moment the Patch Tuesday hits, this won’t take effect?
No affect till the DC’s get patched. One of the patches will add a security update that will add this change, so once we know which one another way is to defer the update. If you can though and need to the regkey can be put on via group policy before the patch that way it will keep applying. Hopefully I’ll know more on which patch etc in around 24hours time.
Did we ever find out which patch?
Hi yes, it appears to be the cumulative update for servers this Feb 2025, examples Server 2022 KB5051979 or KB5052000 for Server 2019, the strange thing is Microsoft hasn’t listed it in the features of the update, however I have tested it a few times, once the February Cumulative patch is on server it turns the Event ID 39 from Warning to Error blocking the certificate from authenticating if it is not Strong Mapped
First of all thanks for this writeup! I want to share my experience.
Our company relies heavily on the SCEP cert for 802.1x auth (lan and wifi) and VPN.
I have chosen to rollout a additional cert with a new scep profile from intune and after a while I unassign the scep profile with the old cert . In testing it worked great and the old cert got revoked and deleted on the endpoint when unassigned from the old SCEP profile.
When running in production i’m seeing a 60% succes rate that intune deletes the old cert on the endpoint. It gets revoked 100% of the time so the backend is working correctly, but some certs stay behind on the endpoint without beiing deleted. I dont know what is causing this randomness.
Interesting issue, how long have you waited for it to remove? There is one thing around revocation, do you know if your SCEP server or NDES service account has rights on the Certificate Authority. Similar to this issue https://learn.microsoft.com/en-us/answers/questions/219084/revocation-of-certificates-ndes-intune
We have the following settings in our SCEP config in intune
Subject name format – CN={{onPremisesSamAccountName}}
Subject alternative name – User principal name (UPN) {{UserPrincipalName}}
Since 10/2024 we don’t get any event id 39 anymore in the logs of our dc’s.
Does this mean we’re ok and don’t need to add the strong mapping?
Generally as long as you are not getting Event 39 on DC’s your environment is all good and happy that it can read users or devices certificates OK. Wondering if your scenario is a mixed environment with Azure AD Connect syncing users, and what kind of devices Windows or Mac and if pure Azure AD or Hybrid? Regardless it seems like your environment is fine, no Event 39 and generally all good.
Can you comment Microsoft article about OID support for “Device” type certificates over Intune PKCS? Use case is Radius auth with Mac workstations. I found from the article following paragraph:
https://learn.microsoft.com/en-us/mem/intune/protect/certificates-pfx-configure
This update applies to users and devices synced from an on-premises Active Directory to Microsoft Entra ID, and is available across all platforms, with some differences:
Strong mapping changes apply to user certificates for all OS platforms.
Strong mapping changes apply to device certificates for Microsoft Entra hybrid-joined Windows devices.
So if we want to use Device certs with OID on macs, it will not work? As I understand Device type works only for Microsoft Entra hybrid-joined Windows devices.
We updated Microsoft Intune Certificate Connector to latest version 6.2406.0.1001 and enabled SID in the registry (EnableSidSecurityExtension). Generated new cert for Mac workstation (Intune profile). Mac received the cert and new OID was present. The problem was that mac could not access the network (802.1x auth). From the logs there was a mismatch of SID:
Old certs: Security ID: Domain\workstation
New certs: Security ID: NULL SID
Certificate template in Intune (PKCS) was not changed.
Intune PCKS profile/settings:
Certificate type: Device
Subject alternative name
DNS: CN={{DeviceName}}.domain.internal
User principal name (UPN): {{DeviceName}}$@domain.internal
Subject name format: CN={{DeviceName}}.domain.internal
Seems like it doesn’t know how to align computer(device) with this cert. If we map this cert directly to this mac computer object in AD (domain joined mac), trough Computer Name Mappings, it will start to authenticate to the internal network.
If we disabled SID/OID generation from registry, macs will get cert with old values (no OID) and they would get network access automatically (SID will be aligned). So it is strange that adding OID field, will mess up the whole AD authentication thing. Correct me if I’m wrong.
I’m going to try a few things with Mac certs this weekend as there seems to be some strange things with certs on Mac, getting something a bit similar with Jamf Mac delivery coming through NDES, will write here what I find out.
Hey Tim. Any progress on this topic? Did you manage to sort it out?
Hey there, we recently had a project to get a bunch of Macs to use 802.1x. These Macs were managed via Jamf. Whilst I was working on the Windows side, my colleague worked on the Jamf side. We were deploying device certs but was able to get the UPN injected into the SAN. When the devices were connecting, the UPN in the SAN matches the user object in AD and authenticates.
Is there any impact on computer certificates?
I see only changes regarding user certificates is this correct?
There is but only in a few scenarios, mainly where if you are using Hybrid Joined devices and for those hybrid joined devices they are still getting their certificates from NDES. If you have hybrid joined devices and they are getting certs from on premises then as long as those devices renewed their certificate since mid 2022 then they are likely ok as on premises added the mapping automatically.
Its best explained by Microsoft in this statement here
“”For device certificates, only Microsoft Entra hybrid joined devices will have SID information, so strong mapping changes are applicable only to Windows devices that are Microsoft Entra hybrid joined. For other device types, like iOS or Android, strong mapping is not supported for device certificates, and user certificates should be used instead.””
Hello Tim, as answer on your question regarding my earlier comment on February 13, 2025 at 10:13 am
I’ve waited more then 2 weeks but no cert deletion on arround 40% of our endpoints. On the backend everything is working alright including the rights for NDES. Intune cert connector processes a revocation request to NDES, NDES processes and logs the revocation request to ADCS and ADCS revokes the cert correctly. So that chain is working correct. But the correctly revoked cert is not deleted on certain endpoints.
Also no difference in OS/patchlevel or newer or older enrollment or things like that. It’s completely random.
I stopped searching for a solution. Its just a onetime thing so I created a remedation script to delete the old cert and watched the DC logs for disappearance of eventid 39 in the system logs.
I think your “deployment solution 2” is a better option when your not having much devices or only use the cert for VPN. I also thought of this option, but for me the risk was to high because it is directly applied to ALL assigned users/devices on that SCEP profile(1000+ in our situation). So you cant easily scope the assignment. The risk for our PKI dependency on this cert is to high risk because NAC relies on it.
Glad your script is helping you, To be honest I have seen some weird things like this, some people say Oh just change a cert detail everything will get deployed automatically but just haven’t seen it in my environments, always just sat there. On a 35k user site ours did seem to replace OK once we deployed new, and was only left with about 50 which for some reason just sat there not wanting to replace and those in the end we deleted and re did a device sync, and it pulled down new interesting as somewhere on the web I saw someone with similar issue to yours and they also used a script.
We are seeing the same problem. Can I ask how you identified the right certificates to delete with your script as it looks like we’ll need to do the same.
Thanks
Got an odd problem: Intune will not accept the {{OnPremisesSecurityIdentifier}} variable. Trying to add URI = {{OnPremisesSecurityIdentifier}} gives red warning:
“A value is required for Value. Provide a value that can combine any supported variable with static text. For UPN and Email addresses, use the format {{AAD_Device_ID}}@contoso.com. DNS values must not include symbols or an @ sign, e.g., {{DeviceName}}.contoso.com or {{DeviceName}}”
So odd, I tried to reproduce thus today by trying device certs, user certs etc but so far all accept. Do you know in your environment if just for testing purposes if you do new cert does it accept it into a new certificate?
Attibute URI Value {{OnPremisesSecurityIdentifier}}
We have an issue where the PKCS certificates are issued with the SID on already installed clients. But when a certificate is issued during pre-provision the certificate is missing the SID. The {{OnPremisesSecurityIdentifier}} would be nice to include in the PKCS request to?
We have an issue where the PKCS certificates are issued with the SID on already installed clients. But when a certificate is issued during pre-provision the certificate is missing the SID. The {{OnPremisesSecurityIdentifier}} would be nice to include in the PKCS request to?
Thanks to everyone for the work and research. As of March 26, I’m still dealing with this.
I have two NPSs in a cluster, and I don’t understand why switching from one to the other results in failures on one and successes on the other when this shouldn’t depend on them but rather on the ADs or, at most, the CA.
I see event 39, and in those cases, authentication works, but I understand that it’s in a grace period.
The issued certificates, whether manual or automatic, do not have the required OID (1.3.6.1.4.1.311.25.2), and I can’t find it in the CA either, which makes sense since it’s not updated.
Given this, is there something I’m misunderstanding?
Hi we are using device based certificates and not user related certificates for SCEP.
First question is will the identifier {{OnPremisesSecurityIdentifier}} work for devices the same as it does for users? Has anyone been able to test this?
Our domain controllers for the CA are running server 2016 is this going to cause an issue as the article above refers to how it needs to be server 2019 or can we continue running server 2016 for the time being?
Any help would be of great help as I am new to taking over the intune side of our environment.
I CANNOT replicate Error 39 for strong mapped certificates on my 2016 DCs. I CAN replicate the errors with non-strong mapped, however. Has this deficiency been patched?
So what do we do with 2016?! 🙁
Thank yuo
Unfortunately only way really is to upgrade DC to 2019 or 2022, I would say or 2025 but you have to be brave to go 2025 on a DC as still some issues in some environments with 2025
Thanks for your article. It was a nice read. We are currently facing a problem where we have a client that have a bunch of Intune devices that are AADJ only. We have writeback enabled on AADC so these objects appear in the on-prem AD under registered devices. These objects in AD have the ObjectSid in their attributes.
When we created a test SCEP profile in intune and add the URI – {{OnPremisesSecurityIdentifier}} and push it out to a bunch of pilot devices, the certs will get issued but there are no SIDs present in the SAN on any of the newly issued certs. They are still generating event ids 39 on the DCs. We are issuing device certs by the way.
We have currently deferred our DC updates until next week to resolve the new Strong Cert mapping from Microsoft, but I”ve hit a bit of a wall. I’ve enabled the regkey on our connector server as we are using PKCS certificates, however the SID appears under OID rather than in SAN – is this expected/non-problematic? We are currently facing an issue with accessing file shares and SYSVOL/NETLOGON locations when using our VPN and I haven’t been able to get to the bottom of it.
Any tips would be greatly appreciated!
Hi, so sorry just to allieviate your first worry yes PKCS will not have in SAN. This is expected and yes in OID is all good that should work fine..
Wondering what your other issue could be I’m probably completely off the mark here but………
Troubleshooting your other issue
Certificate Chain Validation: Ensure your PKCS certificates have a complete, trusted chain back to a root CA that domain controllers recognize…..
Time Synchronization- Certificate-based authentication is time-sensitive. Verify NTP sync between VPN clients, domain controllers, and certificate authorities….
CRL/OCSP Access — Domain controllers need to validate certificate revocation status. Ensure CRL distribution points or OCSP responders are accessible from your DCs
Registry Key Verification- Double-check that the StrongCertificateBindingEnforcement registry key is set correctly (typically to 1 for compatibility mode initially)
Event Log Analysis– Check the System and Security logs on your domain controllers for certificate-related errors (particularly Event IDs 4768, 4771, and certificate validation events)
Quick diagnostic steps:
Test file share access from a domain-joined machine without VPN to isolate the issue
Verify certificate properties using certlm.msc to confirm SID presence
Use klist tickets to check Kerberos ticket acquisition after VPN connection