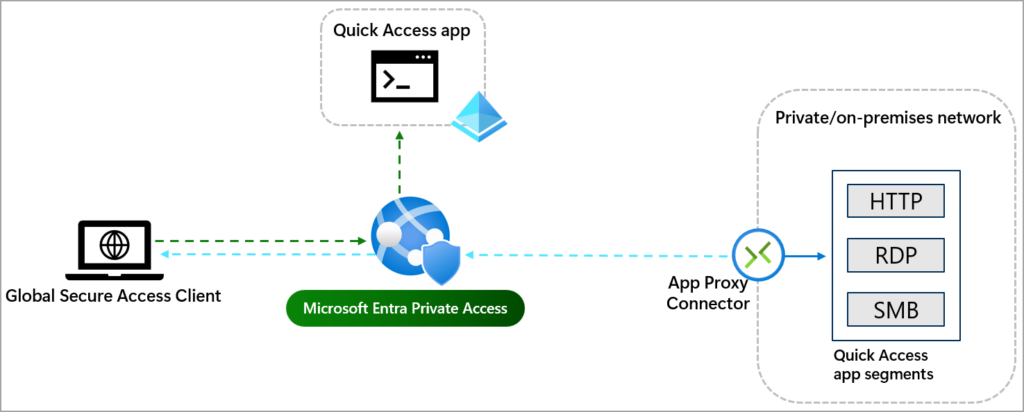
This post is a quick look at Microsoft Entra Private Access with which you can implement to access company resources such as apps file shares etc without a VPN.
Microsoft describe the service as “Quickly and easily connect remote users to private apps from any device and any network. Reduce the operational complexity and cost of your legacy VPN, while eliminating excessive access and preventing lateral movement.”
With all the security issues recently with VPN’s like Fortinet it may be a good time to look at alternatives to VPN’s and remote access solutions.
Prerequisites
- Current;y Entra ID P1 license required. (This may change once service comes out of Preview)
- To Test this scenario you will need a server running something internally i.e for this test I’ve used an iis server
- Install the Global Secure Access Client on your laptop or testing device you will use to access internal resources
Setup
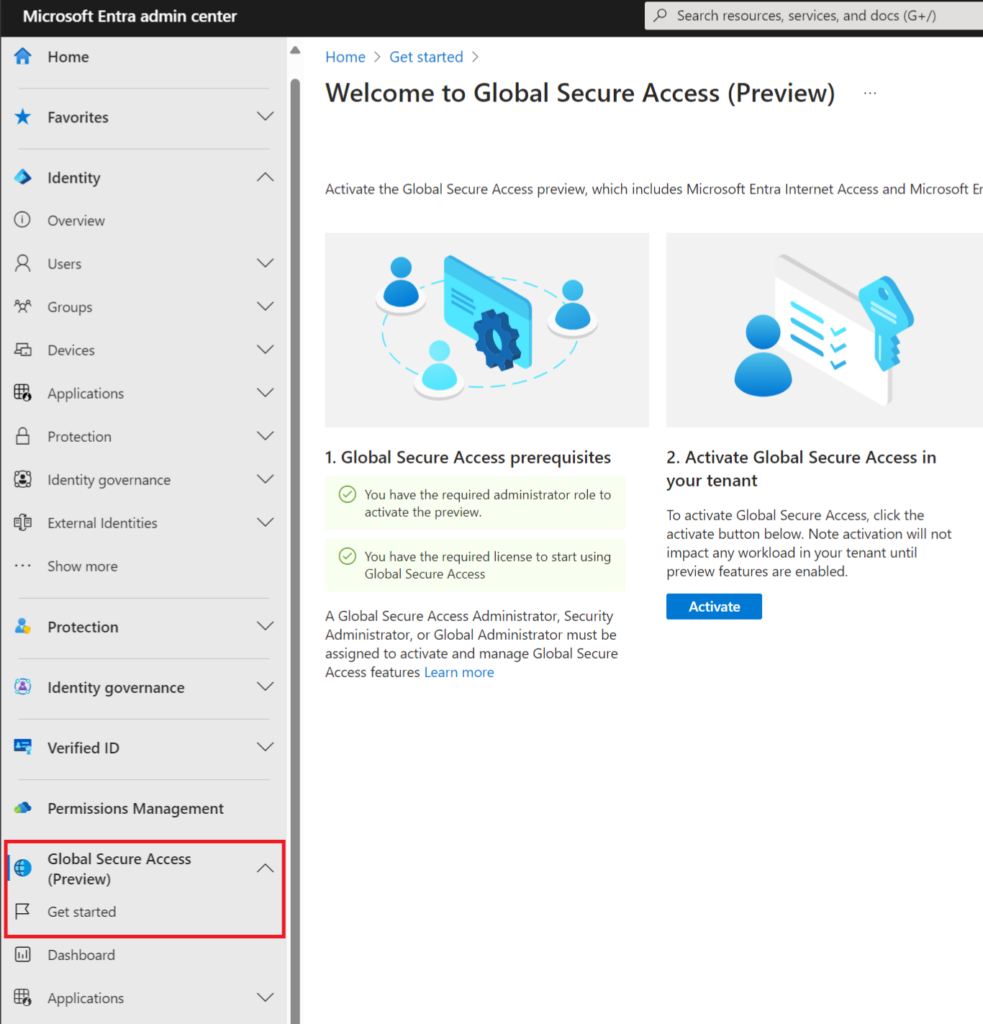
If you haven’t already done so activate the service in the Global Secure Access > Get Started Menu
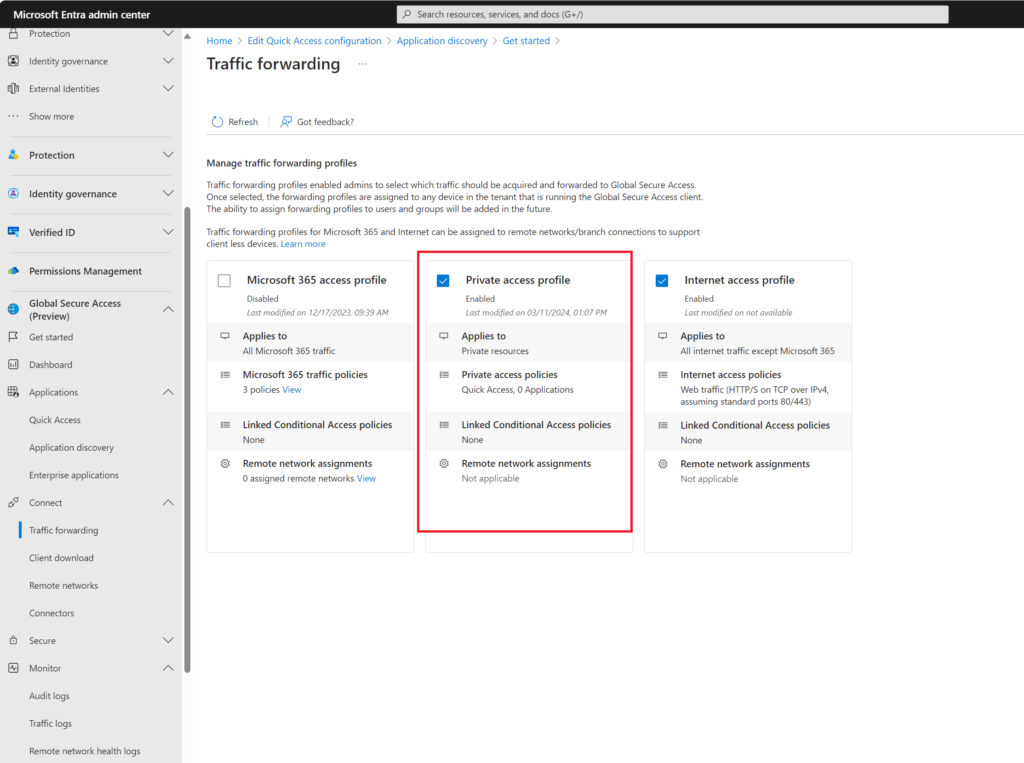
Now go to Traffic Forwarding and tick the private access profile (Internet doesn’t have to be ticked, I’m using that for a separate test.)
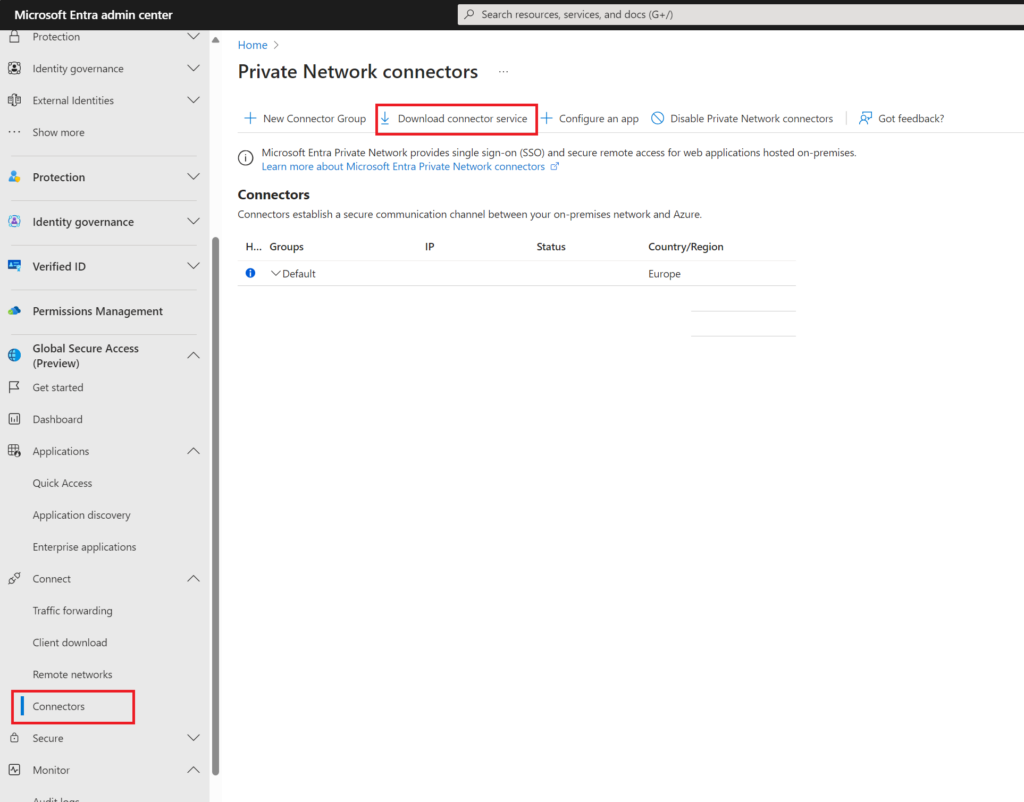
Install Connector within Network
Install this connector on your server you want to connect to (This doesn’t have to be on the exact server you are connecting to and you could setup a dedicated proxy server or choose a server in same subnet etc)
In this test scenario I’m installing on an IIS server thats running on internal network unreachable from Internet
At end of the install it will ask you to login to azure which will then register the connector in Entra Portal
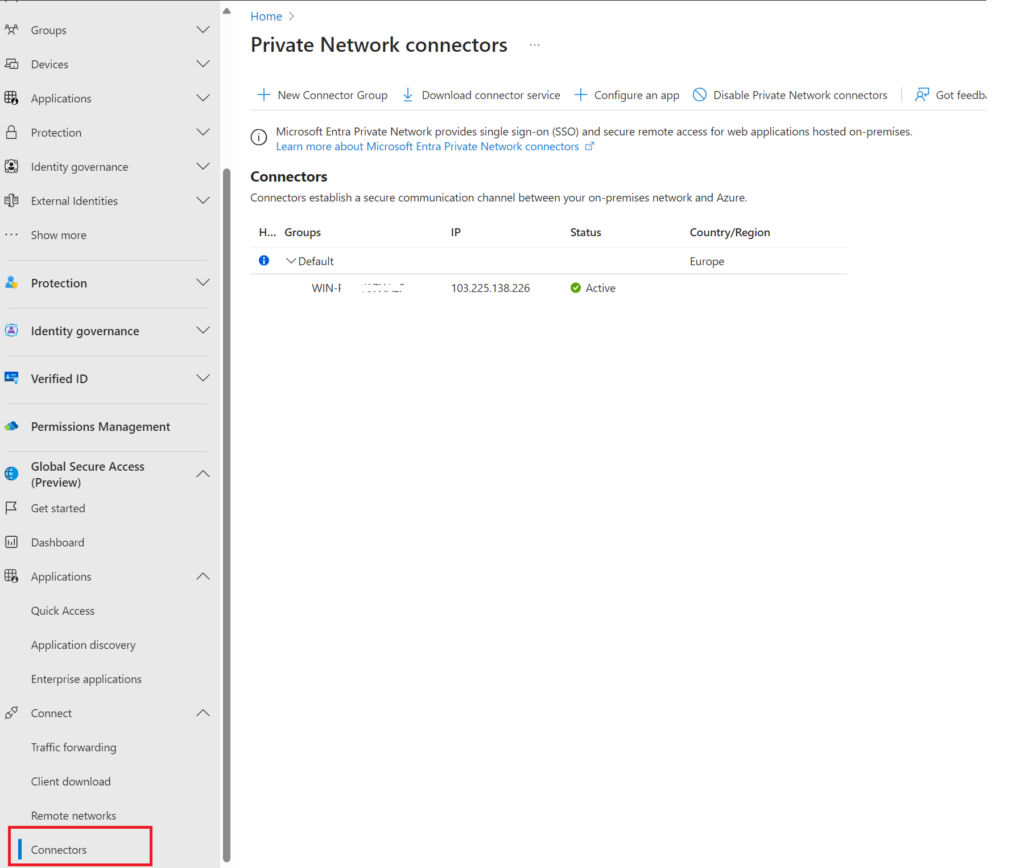
Now under Connectors you should see your your server show up as active
Install the Global Access Client
On the test laptop / desktop you will use to connect to your server for testing from outside the network install the global access Client
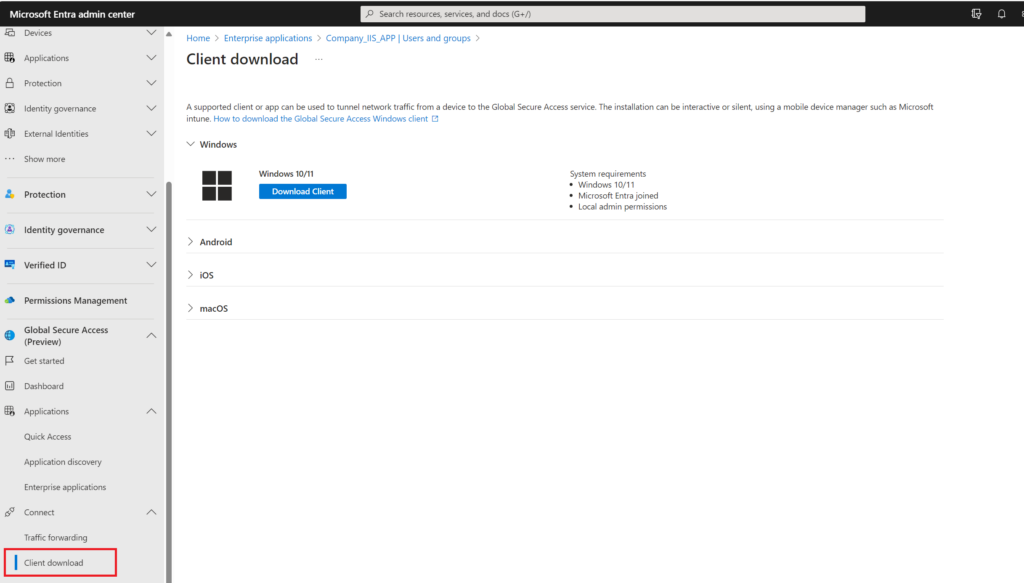
From Client Download, get the client and install on your laptop
In your tray icons you should now see the global access client
Create the Application for Access
You can either use the quick access method or create Enterprise applications manually here for this test I’ll just create a quick access application.
Name your app that will be created and its connector group
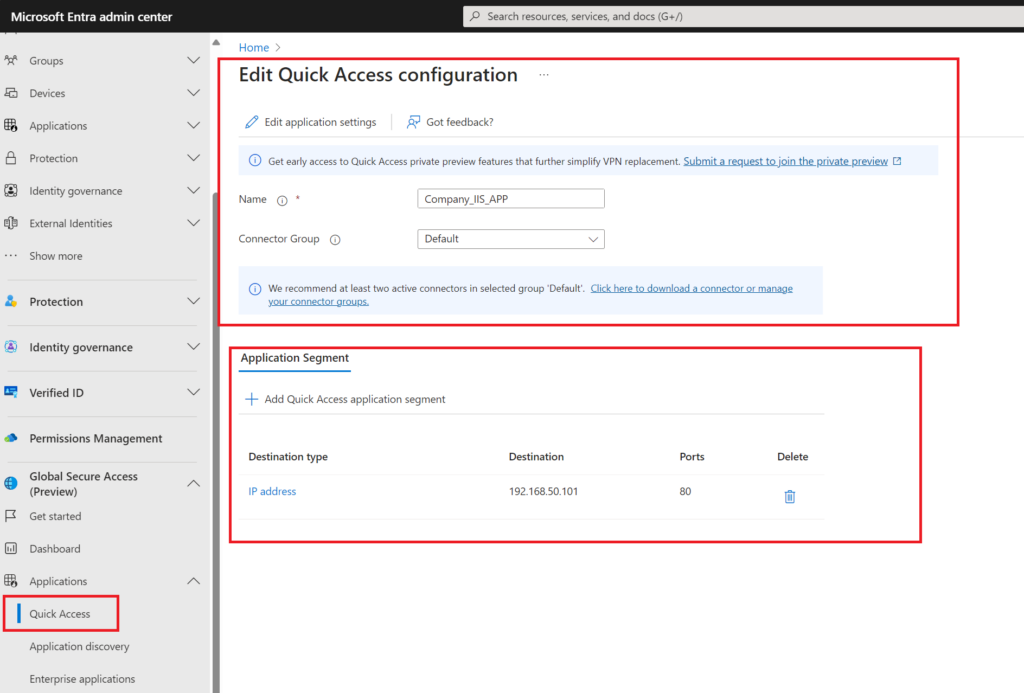
Then add the segment (which is basically the settings to access)
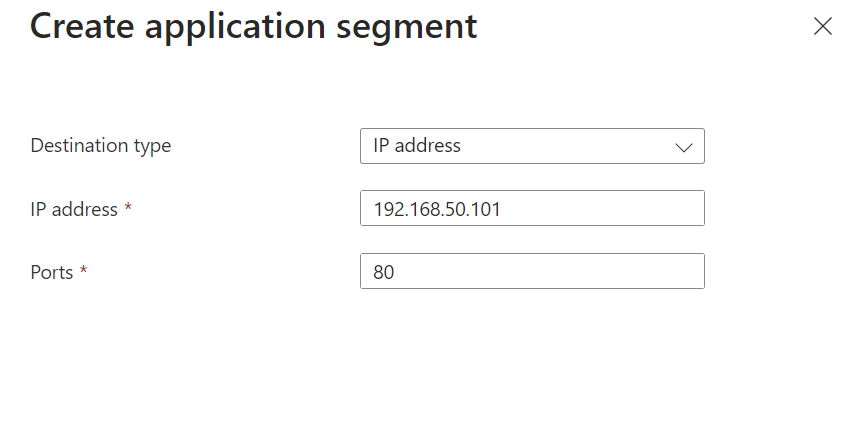
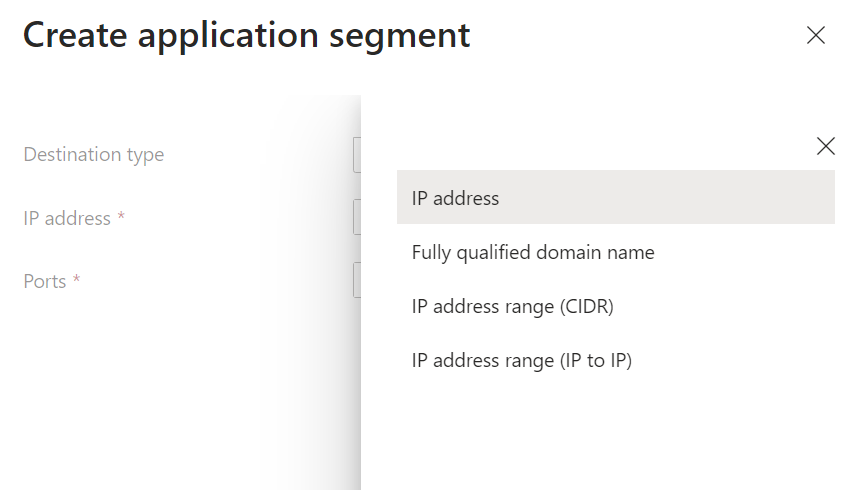
In my case I added the IP Address my IIS server is on and the port to access it, (and yes in production I would be a bit more secure than this 🙂
By the way there are plenty of options like FQDN’s and subnets to set this up properly
If you go to your enterprise Applications you will now see the app as setup
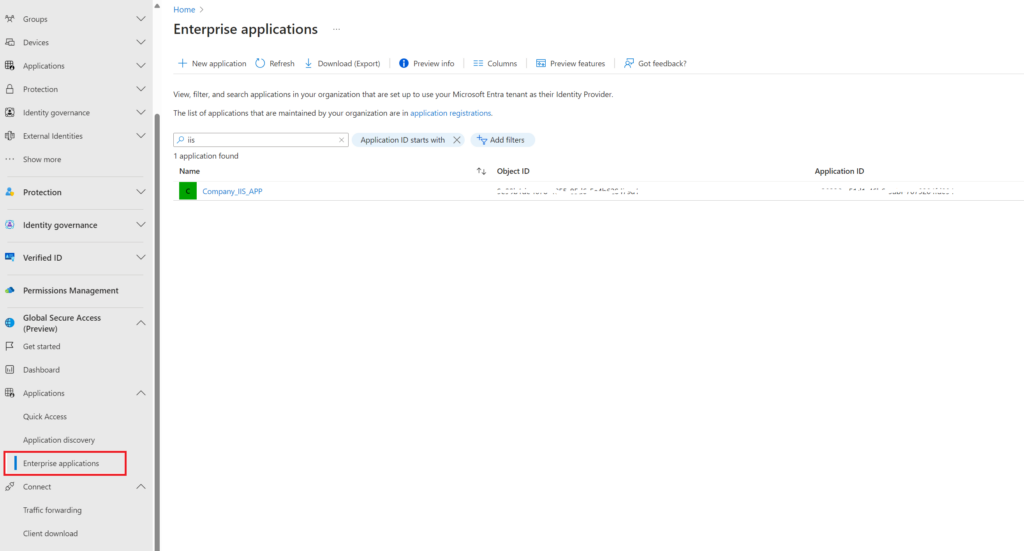
If you open the properties of the app you will see the has to be assigned to users as by default this option is on
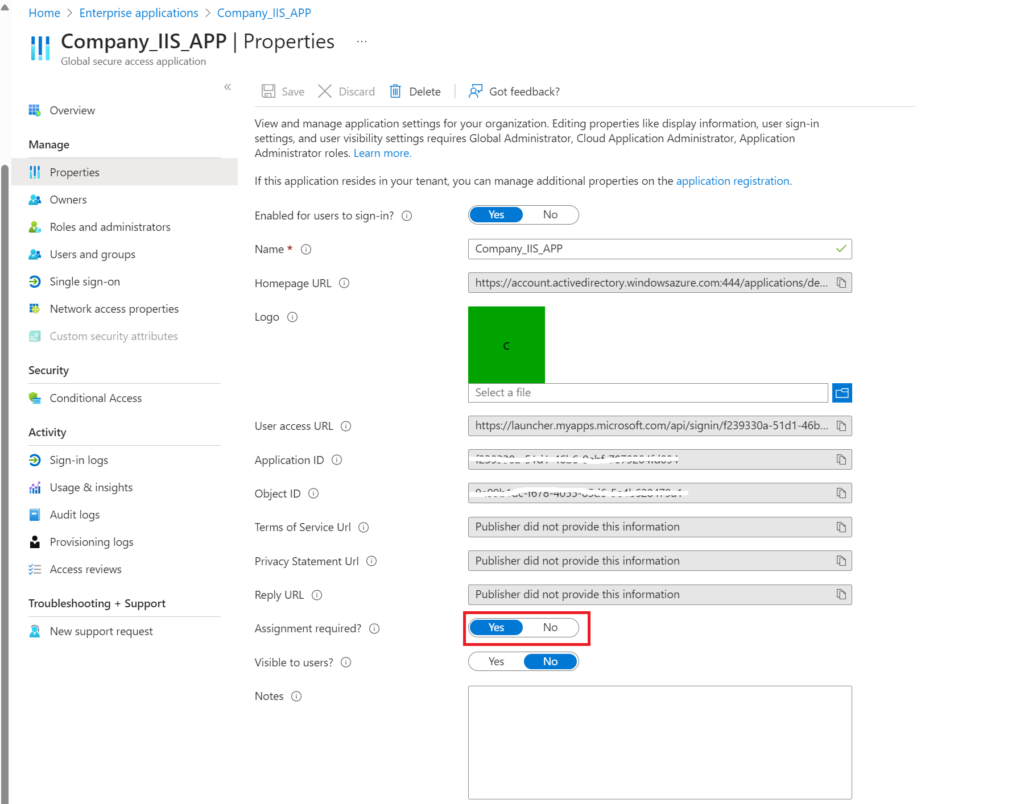
So in Users and groups add the user account you want to test
Testing on an off network laptop
If I now use a laptop with my username on it in my case Intune Entra Joined laptop
I’ve tethered this laptop to my mobile phone so its completely off my internal network and purely on the internet
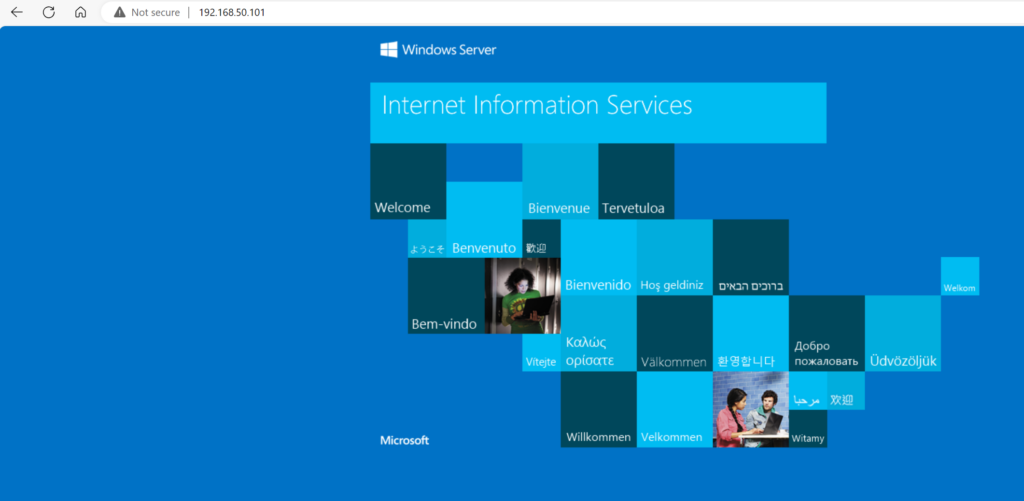
So this is purely coming from the internet into the network through a tunnel created by Entra Private access and you can see this on the Global Secure Access Client
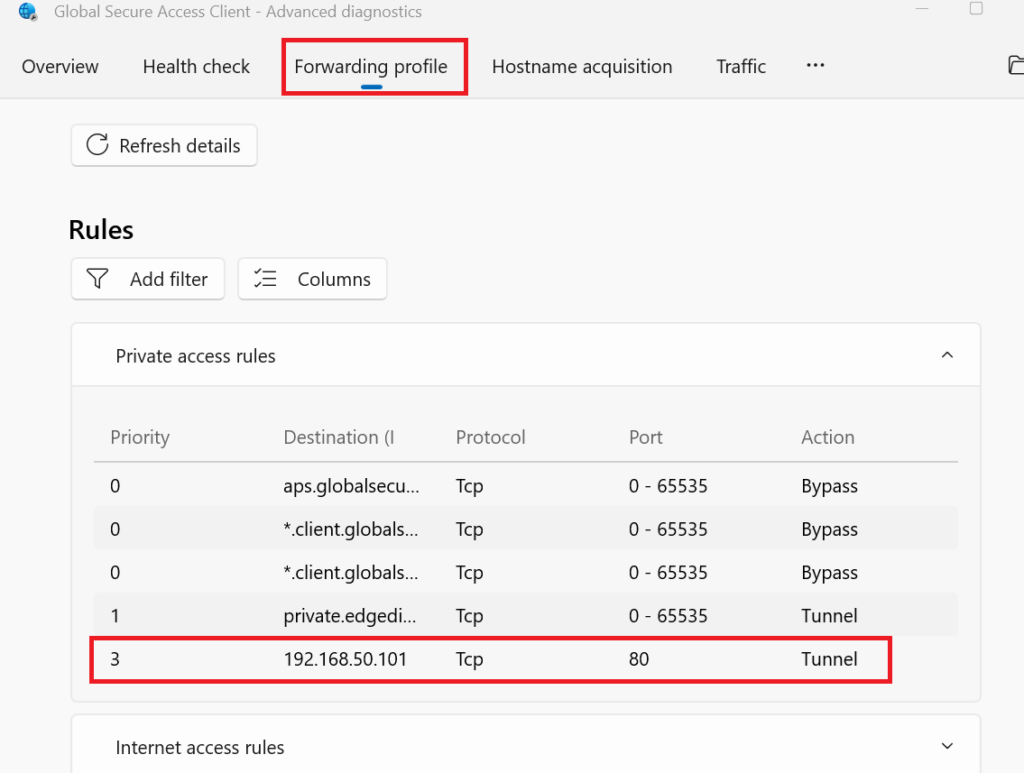
From your Tray icons on you laptop go to Advanced Diagnostics and open the forwarding profile, you’ll notice any updates in the console for example if I add an address or port in the Entra Portal it’ll take approximately 5 mins to reflect in here.
Summary
Entra Private Access is currently in preview and has a lot more features to be tried and tested including integration with Conditional access to secure the solution further
Currently this is looking like a great secure alternative to VPN’s and other remote access solutions
As more or more devices become cloud only but with a few legacy apps that haven’t moved to SAAS, or with file shares this solution makes it easy to setup there is also upcoming no need for Global Access client for some scenarios.

1 thought on “Microsoft Entra Private Access – A quick look at accessing internal resources without VPN”