
This post will focus on Entra Intenet access (currently in public preview) with the aspect of providing a Content filtering Secure Web Gateway similar to perhaps Zscaler.
Microsoft describes this in the following terms
Microsoft Entra Internet Access provides an identity-centric Secure Web Gateway (SWG) solution for Software as a Service (SaaS) applications and other Internet traffic. It protects users, devices, and data from the Internet’s wide threat landscape with best-in-class security controls and visibility through Traffic Logs.
Entra Internet Access features
- Protect user access to the public internet while using Microsoft’s cloud-delivered, identity-aware SWG solution.
- Enable web content filtering to regulate access to websites based on their content categories and domain names.
Other features include
- Prevent stolen tokens from being replayed with the compliant network check-in Conditional Access.
- Apply universal tenant restrictions to prevent data exfiltration to other tenants or personal accounts including anonymous access.
- Enriched logs with network and device signals currently supported for SharePoint Online traffic.
- Improve the precision of risk assessments on users, locations, and devices.
- Deploy side-by-side with non-Microsoft SSE solutions.
- Acquire network traffic from the desktop client or from a remote network, such as a branch location.
- Dedicated public internet traffic forwarding profile.
- Apply universal Conditional Access policies for all internet destinations, even if not federated with Microsoft Entra ID, through integration with Conditional Access session controls.
Client
The solution utilizes a client (Global Secure Access Client) (available for, Windows, Mac, Android and iOS)

Quick Setup
Here we will setup basic the web filtering which will use the Secure Web Gateway
First because this is in public preview you may need to activate the service
Entra Admin Center > Global Secure Access Preview

Once activated
You can follow the Microsoft guide to setup
This Microsoft guide will take you through the main setup

Once setup ensure you enable the traffic forwarding rule for Internet traffic
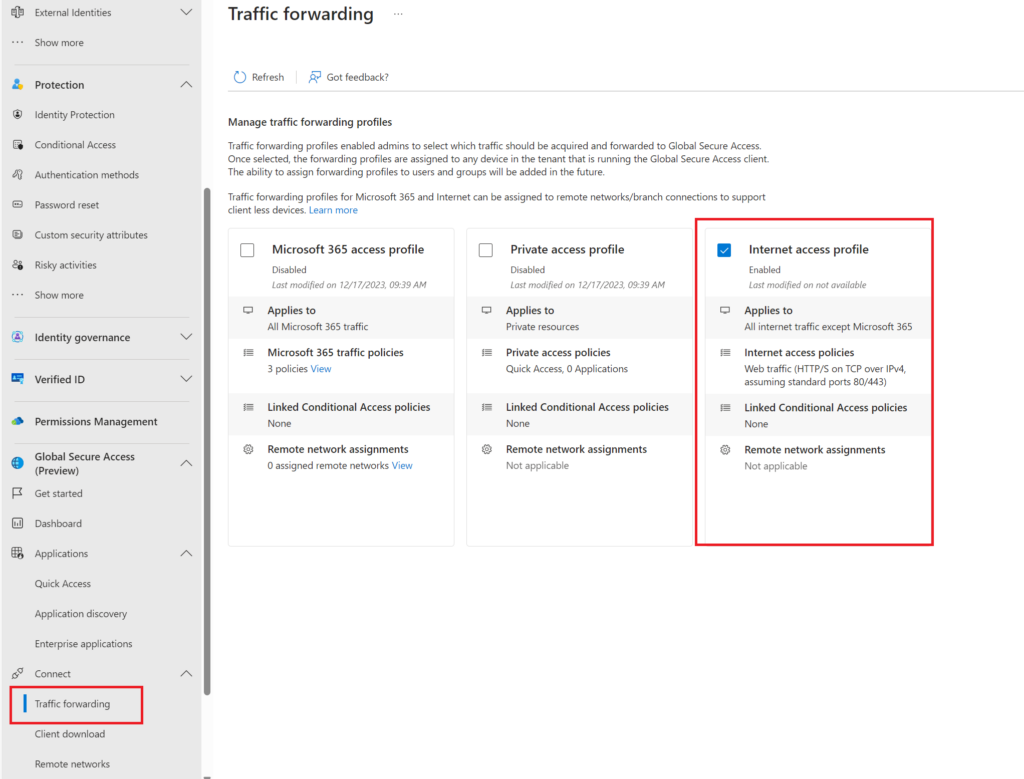
Result
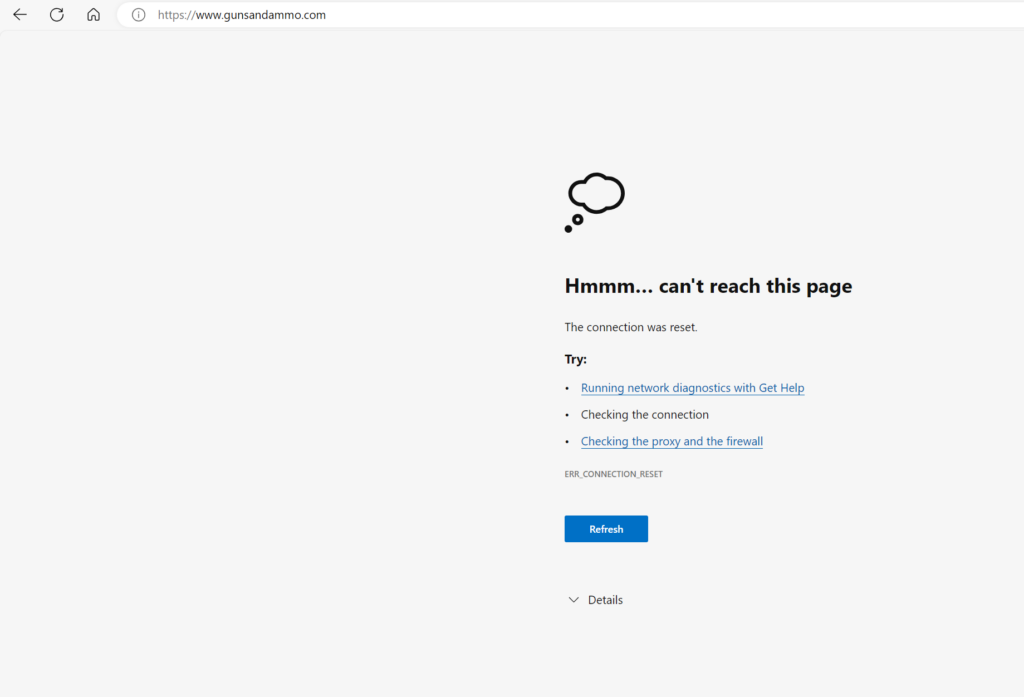
In my policies I added Weapons as an example category to filter

Going to a site that falls under weapons gives…..
Or in another browser (chrome)

or an incognito window

In the console under traffic logs you can see what has been blocked

On the traffic Logs under columns there is a ton of extra information available that makes finding why something was blocked easier


Now you can see why the site was blocked, under what policy filter and rule

Another Test
Lets say a group of users need to access a blocked site now lets allow gunsandammo


Now its accessible

Review
Entra Internet Access seems to be a much more comprehensive solution to Defender web filtering especially the reporting, although this can be expected, considering an agent is needed that sends much more telemetry back. In early testing one of the main
features I’d like to see…
- Corporate block notification rather than a user left guessing why a site is not reachable.
- Also another feature that would be useful is a very quick add to allowed or block sites i.e you could add a fqdn just by clicking add to policy.
