Part 1: Core Configuration Settings
Newly deploying or even seasoned users of Microsoft Defender for Endpoint, one of the most common questions I see: “What do you actually configure?” Microsoft provides defaults, but they don’t always align with best security practices, and the sheer number of available settings (close to 60) can be overwhelming.
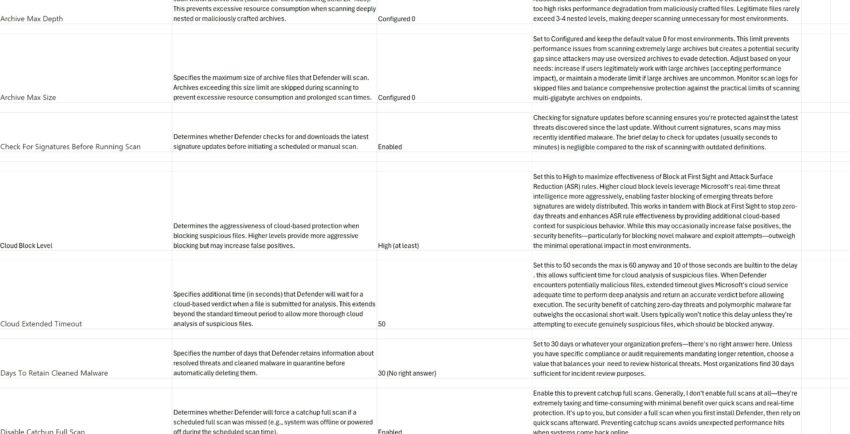
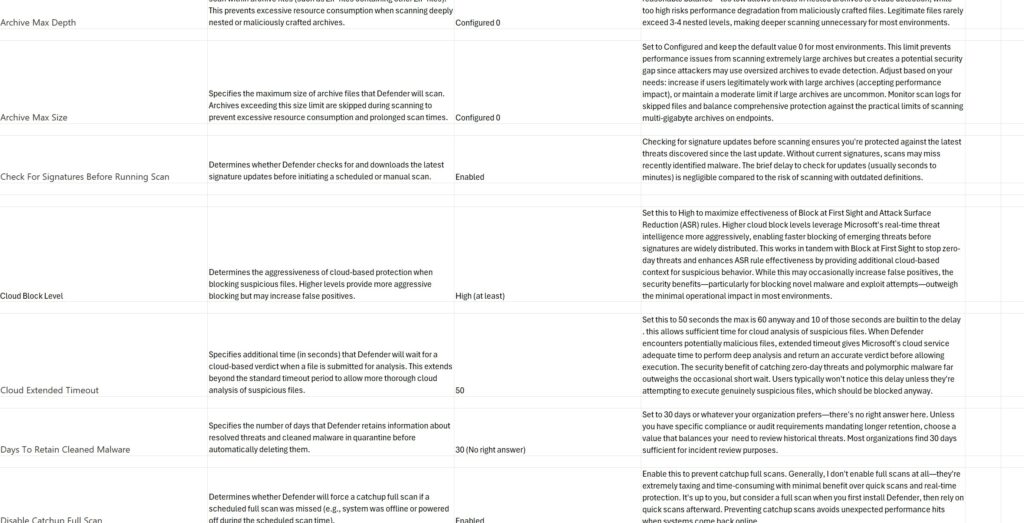
This post kicks off a Defender for Endpoint series where I’ll break down the configuration settings that matter. I’ve compiled a comprehensive baseline that provides strong security coverage while remaining practical for most environments. These aren’t just theoretical recommendations—they’re settings I’ve tested and deployed.
What you’ll find in this baseline excel sheet: Defender Baseline Excel Sheet
- Practical defaults that work for most organizations
- Clear reasoning behind each recommendation
- Performance considerations where they matter
- “No right answer” transparency when settings depend on your specific environment
The attached spreadsheet contains detailed explanations for each setting, including:
- What the setting does
- Microsoft’s default recommendation
- My recommended configuration
- Detailed remarks on why and when to adjust
Important notes:
- This baseline focuses on security without being overly restrictive
- Exclusions (paths, processes, extensions) are intentionally left out of the main policy—configure these separately for better control
- Update channels are set to “Not Configured” as I’ll cover ringed deployment strategies in a future post
- Some settings genuinely have “no right answer”—I’ve noted where your mileage may vary
Download the baseline: https://timbeer.com/wp-content/uploads/2025/10/Defender-Baseline-Settings.xlsx
As always, test in your environment before rolling to production. What works for one organization might need tweaking for another.