Overview
I’ve uploaded the Defender Baseline Here (and yes 24H1 is the latest)
Last week I posted a how to on implementation of the new Windows 24H2 Baseline in sections so that you can do a gradual UAT testing before going to production.
One question that came up (thanks Jeremy Finney) was how about clashes between the Defender Baseline and the Windows Baseline and considerations on roll out if using both.
Some of you may have deployed or are thinking of deploying the Defender for Endpoint Baseline which offers a good set of defender policies for securing your environment,
You will find although there are a lot of similarities between the Defender for Endpoint baseline and the Windows Baseline, in general even though older the Defender baseline is more restrictive than the Windows Baseline, this is reflected in Microsoft Documentation, posted here
HOWEVER QUITE A FEW DIFFERENCES TOO AND CONFLICTING POLICIES
Also a very important note on the Defender Baseline

Main differences
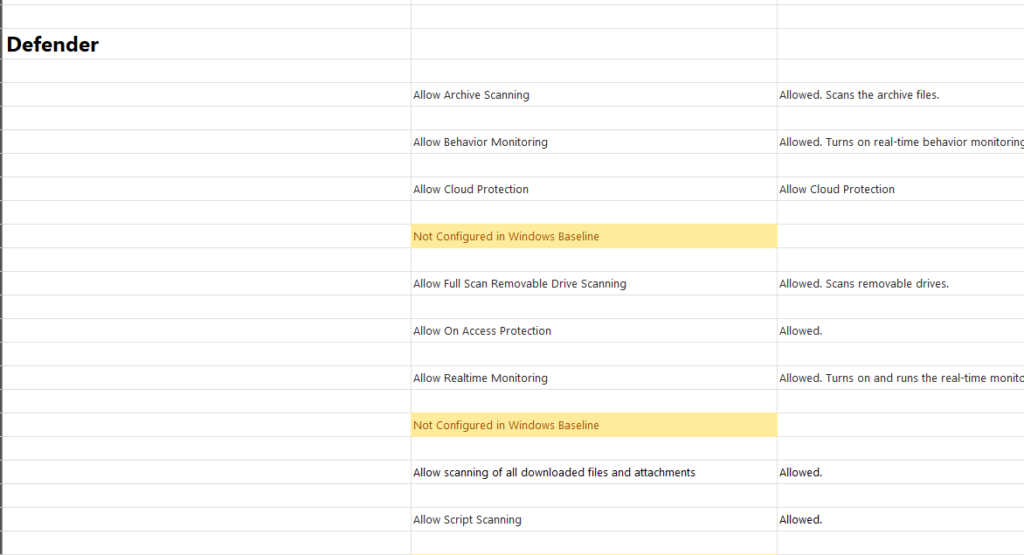
I have put a link in of an Excel sheet that will give a good overview of the main differences between the Windows Baseline and the Defender for Endpoint baseline
Highlights of Defender Baseline
The defender baseline is very heavy on the following areas
Bitlocker – Lots of Bitlocker settings are introduced, you would need to carefully consider
Defender – As no surprise there are quite a few Defender for Endpoint settings set in the Defender baseline
Clashes – I’ve highlighted in Red on the sheet policies that will conflict as they are differently set on the 2 baselines (Usually Enabled on one and disabled on the other)
Implementation of Defender Baseline or any Baseline
Because of the above differences and particularly how restrictive the Defender Baseline is and the Bitlocker settings it imposes this would need strict UAT testing to some test devices, again section by section and even breaking down those sections further. Some of the Bitlocker settings could leave your devices locked out and or unusable.
Once again I’ve put this baseline into it’s relevant sections which makes it slightly easier for testing
You can find the JSON files here
There are sections of this policy that will likely take more testing than most of the whole Windows baseline as many of the settings are very restrictive in most environments
My suggestion is to go section by section and in some sections implement a policy at a time where you are likely to see issues in your environment, restrictive policies include spawning process restrictions in Office and Adobe Apps, Firewall rules, and USB restrictions for processes.
I’ve also added an Excel sheet to Github which outlines some differences and conflicts in the Defender Baseline compared to Windows.
You can get the excel here, hope it helps
Microsoft has a very good doc for baseline implementation
Learn about Intune security baselines for Windows devices | Microsoft Learn