Step by step guide for getting Certificates on Intune machines from your Internal PKI.
I’ve tried to add only minimal rights as I see many blogs adding things like the machine accounts and even Admin rights on servers for the service accounts, I’ve added a little extra security guidance at the end.
Before setting all this up its well worth considering Microsoft CloudPKI which means you do not need all this infrastructure, however if you’ve done your cost analysis and want to setup infrastructure to get certificates onto Intune Machines, then read on
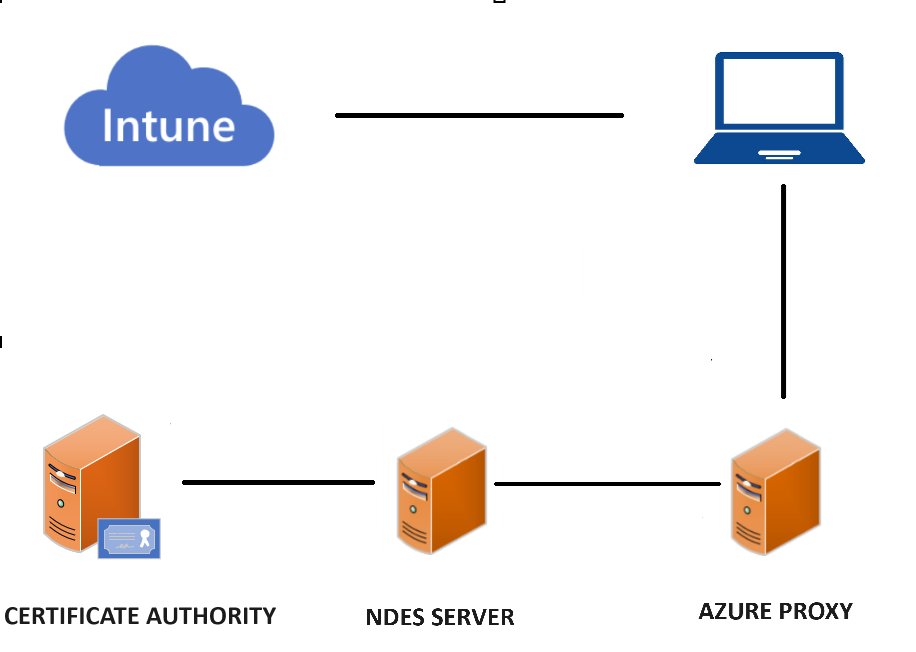
Fundamentals
The Network Device Enrollment Service (NDES) is one of the role services of Active Directory Certificate Services (AD CS). NDES acts as a Registration Authority to enable network devices running without domain credentials to get certificates based on the Simple Certificate Enrollment Protocol (SCEP).
So it can be used alongside a proxy for Intune to get PKI certs from the Internet
Overview / Prerequisites
- Internal Certificate Authority / PKI
- Active Directory
- Entra P1 License for App Proxy
- 1 to 2 Servers I’ve used a separate server for the Proxy you can put this on NDES server if you want to save on cost
- Microsoft Intune Licenses
Setup
Service account
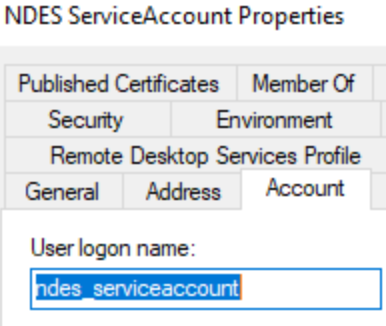
Create a standard user account in active directory (this is going to be your service account for NDES) ,Example here, I’ve setup an AD Account with the following details
User: ndes_serviceaccount
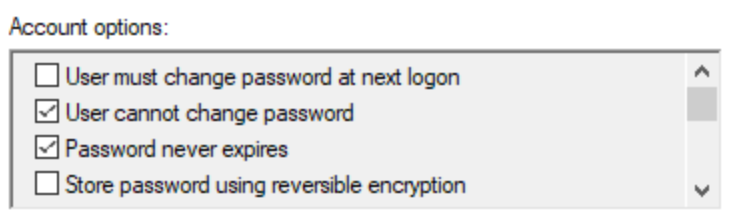
Password: ensure you set a long complex password
Certificates Setup
Essentially you need to create 2 certificates for NDES
- A IIS Web Server Certificate Template for workstations / Proxy can talk to the NDES Server
- A Template so that workstations can request for user / computer certs that NDES will request from the Certificate authority
IIS Web Server Certificate
(If you already have an IIS cert in your corp you use for things like ConfigMgr you may be able to use that, the template here is fairly generic for IIS but we are adding a little security to it
On your Certificate Server open Certificate Authority Right Click Certificate Templates and Manage
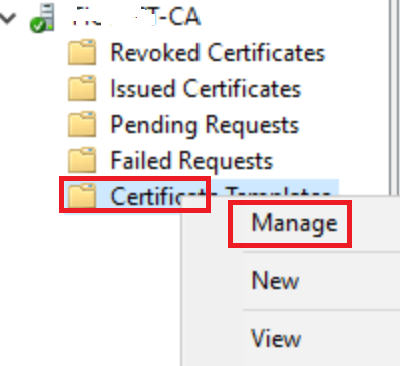
Choose Web Server Right Click and Duplicate Template
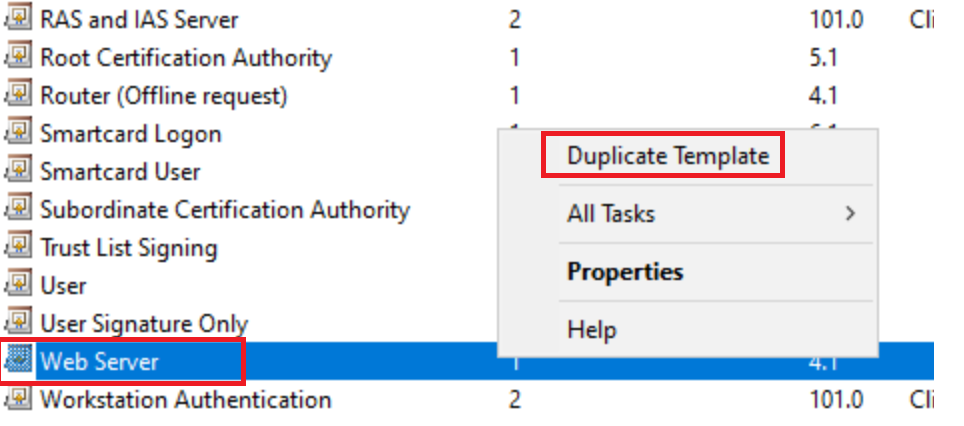
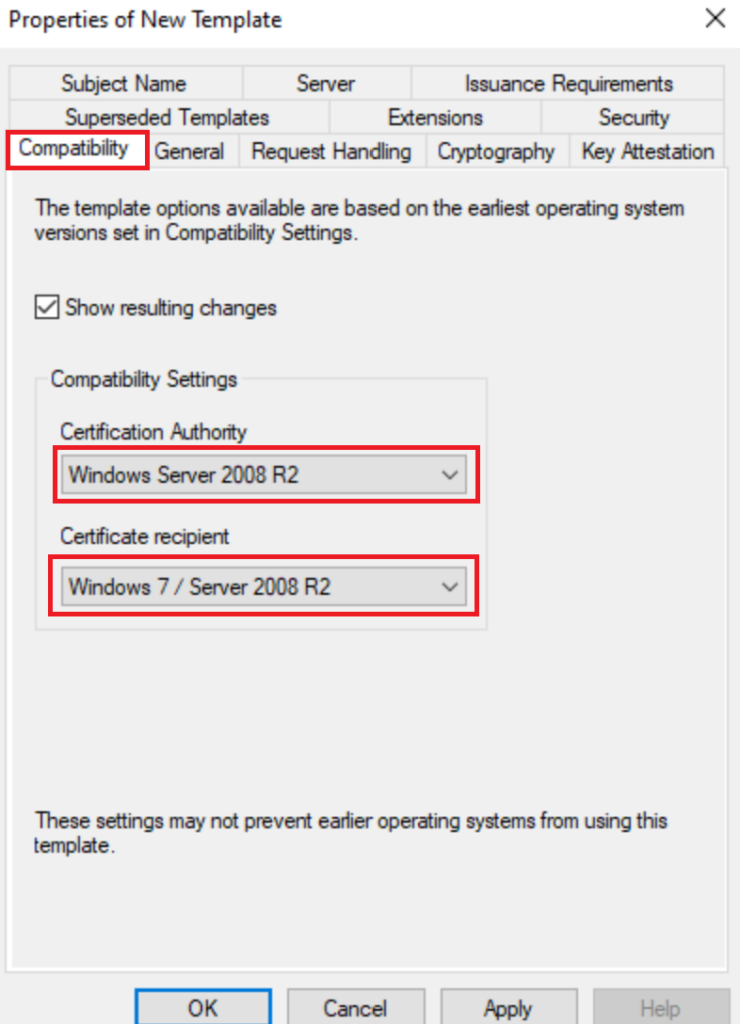
We will change is the following, at the very least set compatibility to 2008r2, when you open the cert it will be set to 2003, far more security has been added to newer template compatibility. (2016 is recommended but 2008r2 at least offers you some added security from the default)
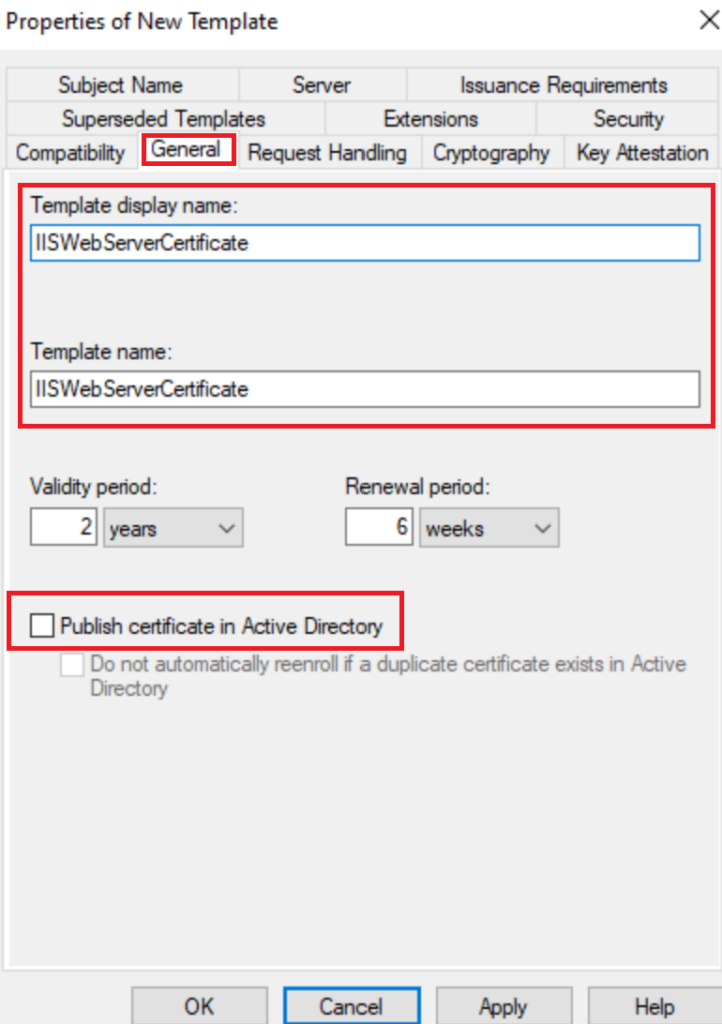
In General Add a name that will be easy to distinguish. Untick Publish to Active Directory if its ticked, I’ve used a generic IIS name as this cert could be used for other IIS services as its good practice not to have a cert for each server i.e this could be used for more or less anything with IIS on it in your domain
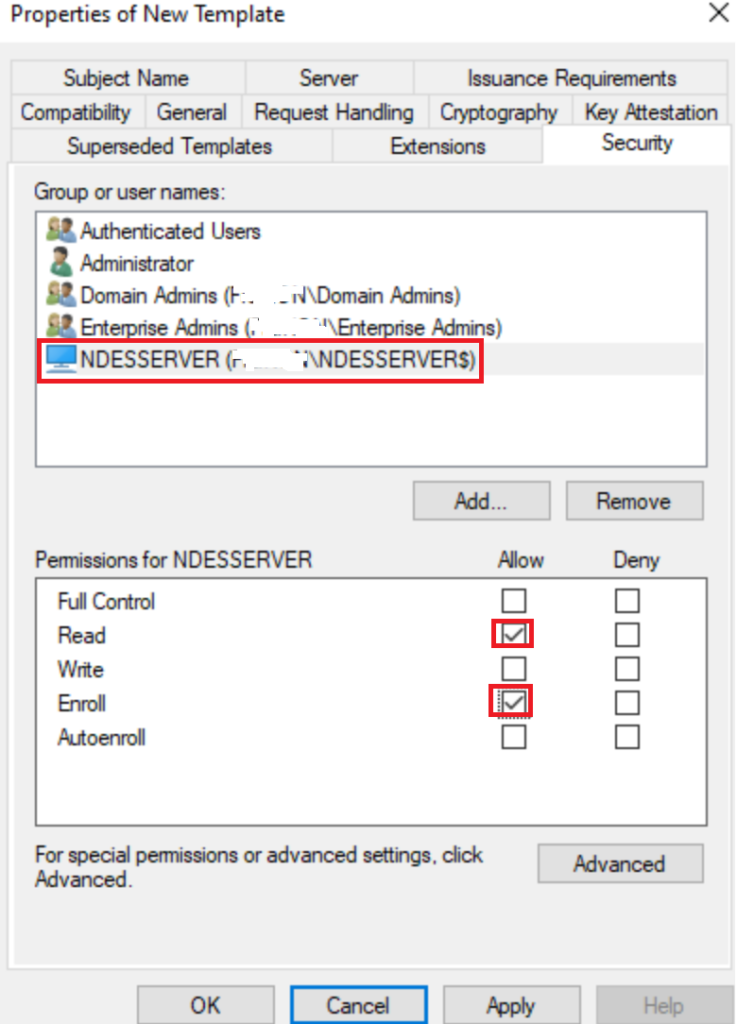
In Security Add your NDES Server as Read and Enroll
Click Apply and OK and we are done with the IIS Web Server Cert
NDES Certificate Template
(The Certificate that will be requested by workstations)
On Certificate Authority Server Choose User Template, Right Click and Duplicate Template
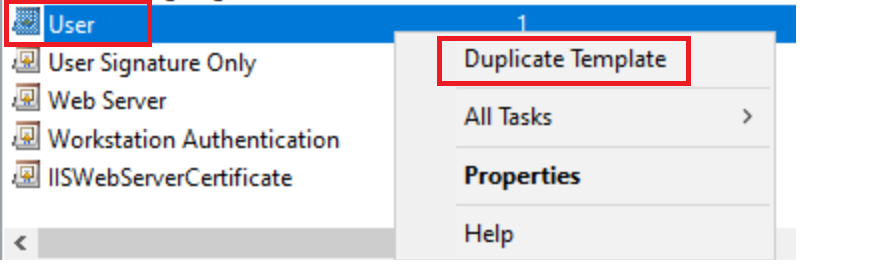
The things we will change for this one are the following, at the very least set compatibility to 2008r2, when you open the cert it will be set to 2003, far more security has been added to newer template compatibility (2016 is recommended but 2008r2 at least offers you some added security from the default)
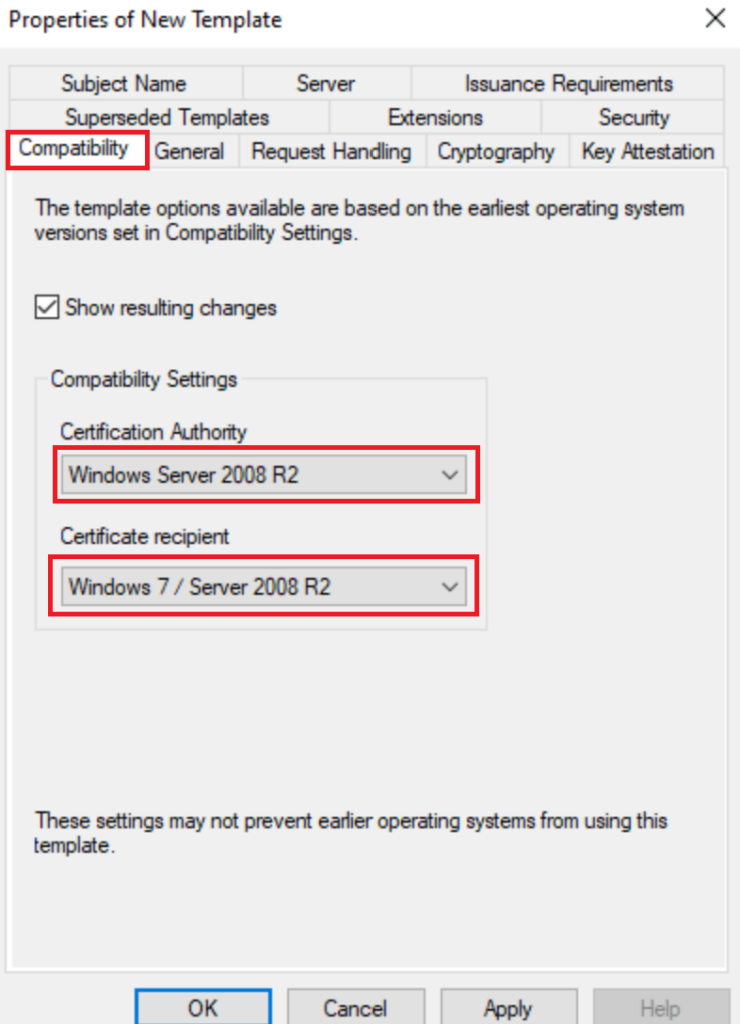
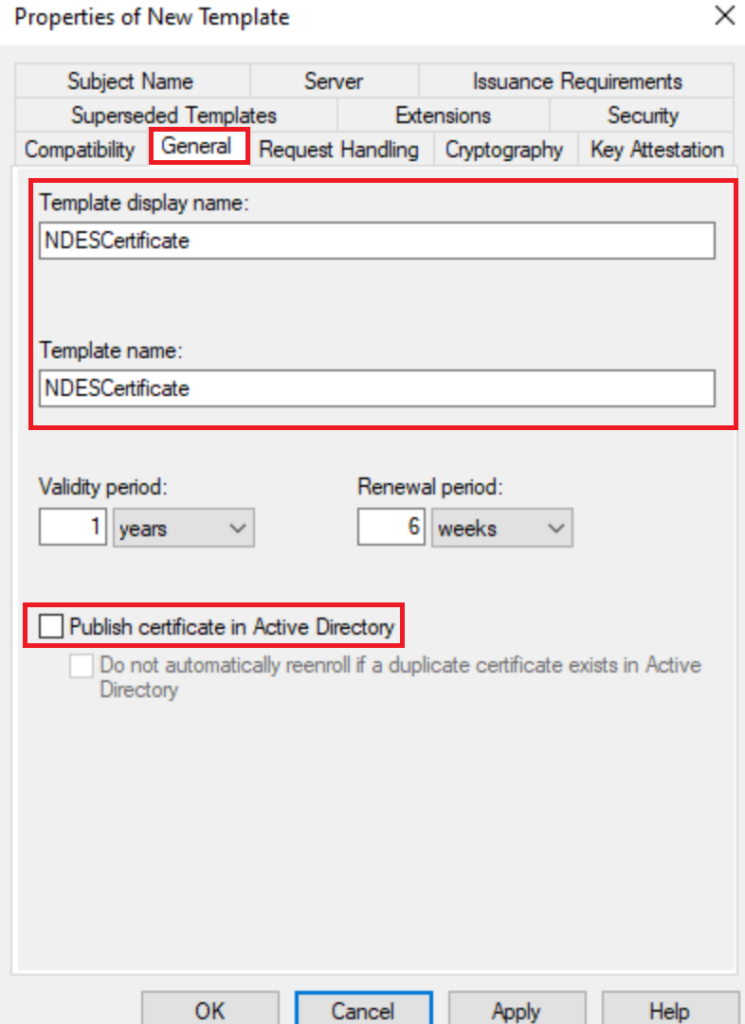
In General Add a name that will be easy to distinguish. I’ve used a generic the name NDESCertificate.
Untick Publish to Active Directory if its ticked,
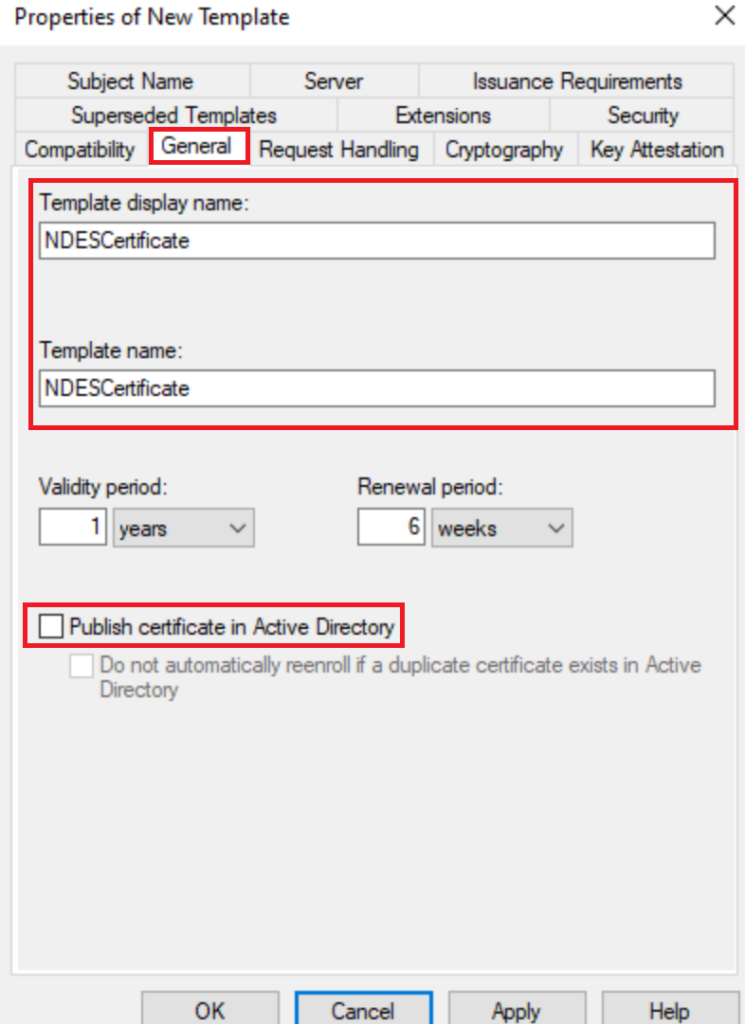
Add the Service account as Read and Enroll
Click Apply and OK and now Publish your 2 certificates
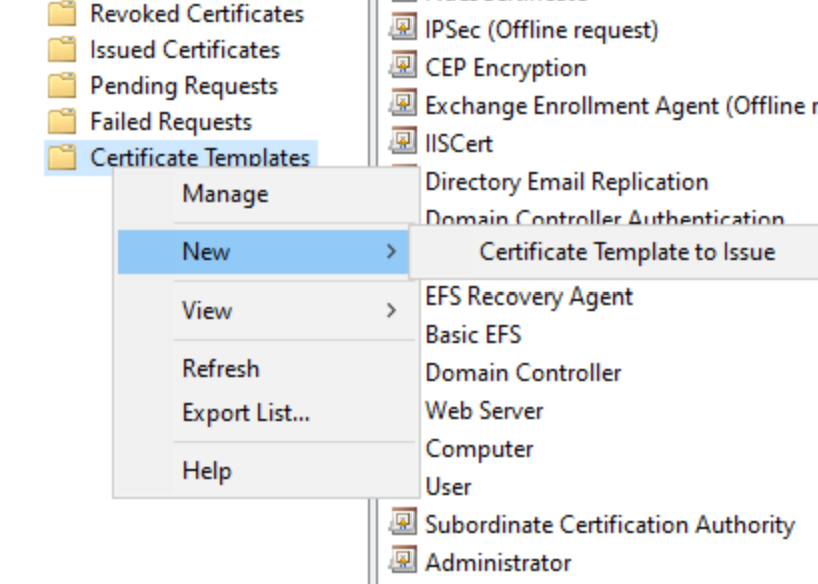
Choose both your NDESCertificate to Publish and Your IIS Cert
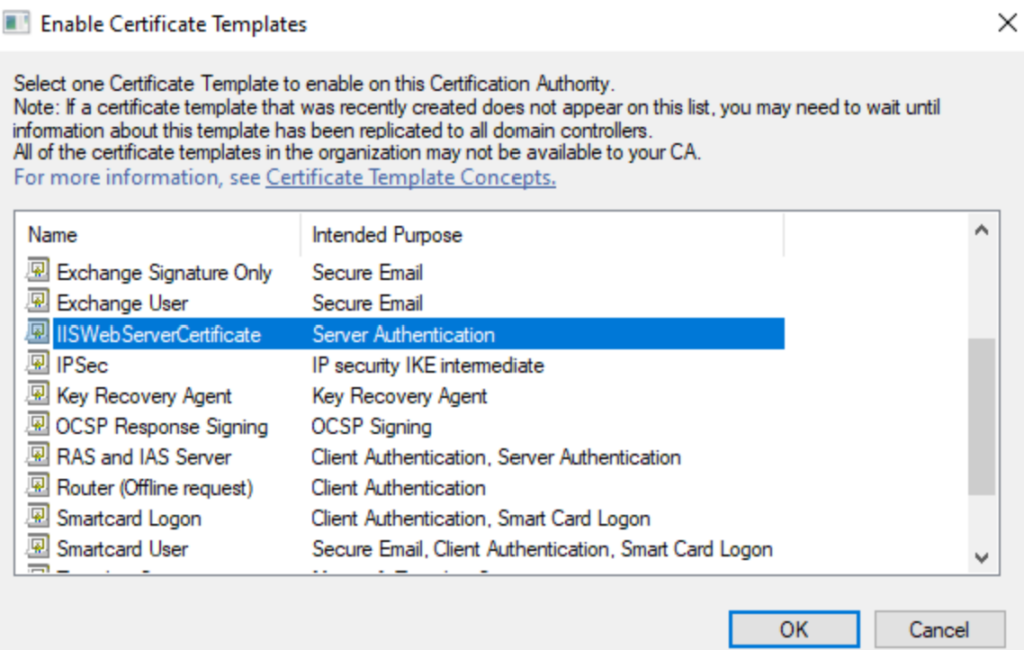

NDES SERVER SETUP
On a Separate Windows Server 2022 domain Joined Server
From the Add roles and features click Active Directory Certificate Services
Click Add Features
Click next till you get to Role Services
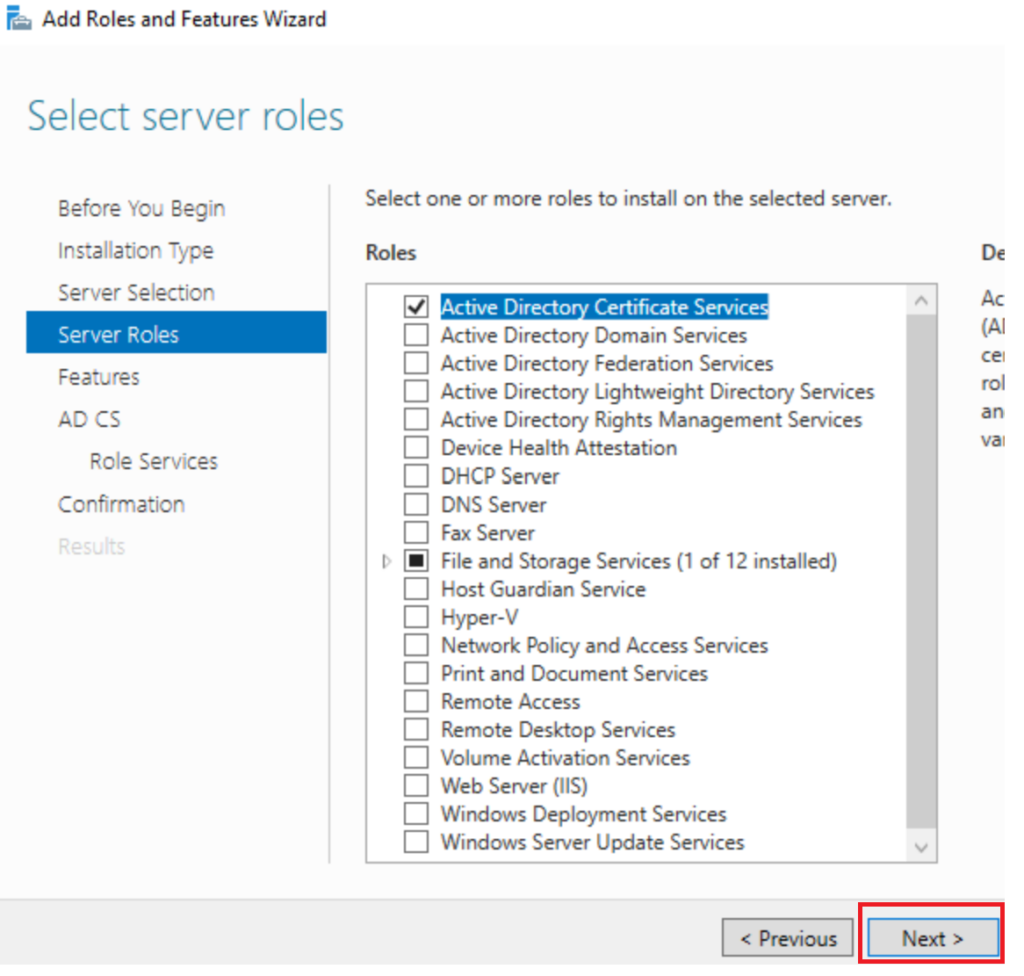
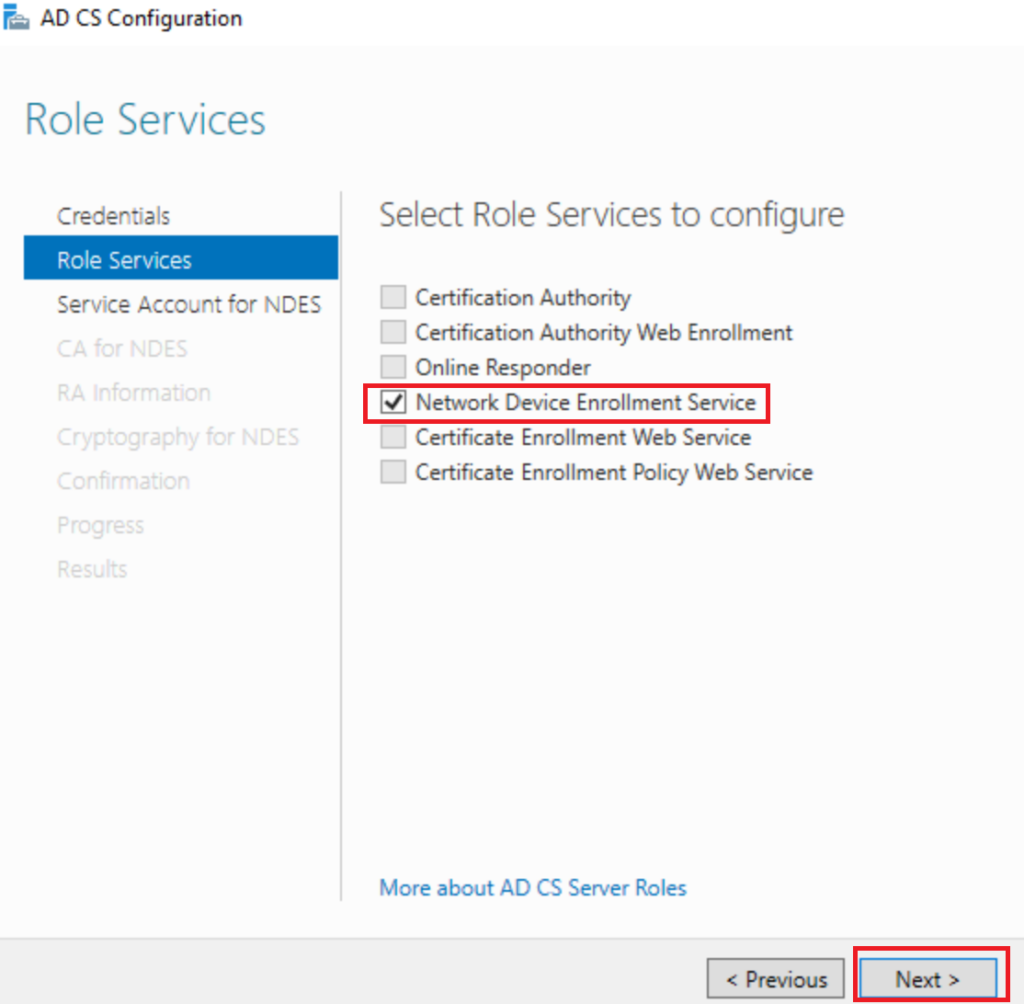
Now in Role Services Untick Certification Authority And Tick Network Device Enrollment Service click next
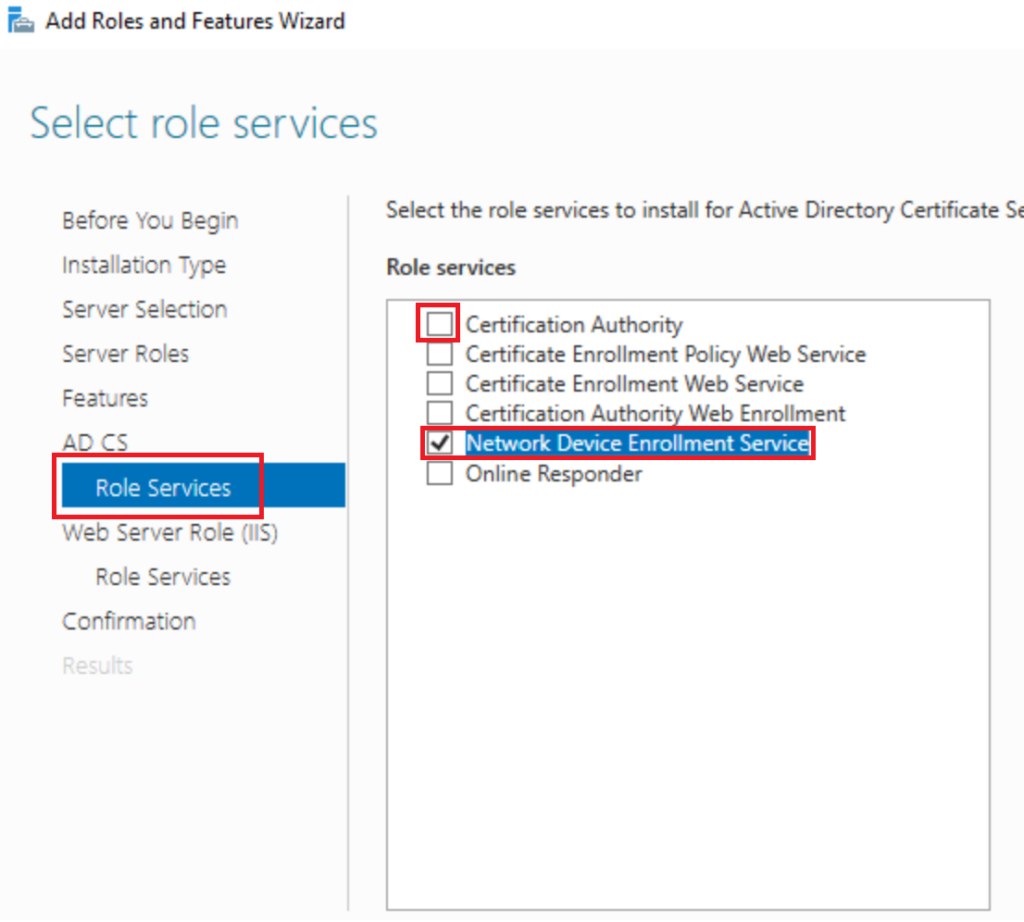
Now in IIS Role Services we need to add some IIS components
- Security > Request Filtering
- Application Development > ASP.NET 3.5
- Application Development > ASP.NET 4.8 (will likely be 4.7.2 on older versions of Windows)
- Management Tools > IIS 6 Management Compatibility > IIS 6 WMI Compatibility
- iis 6 metabase is also required but this is already ticked
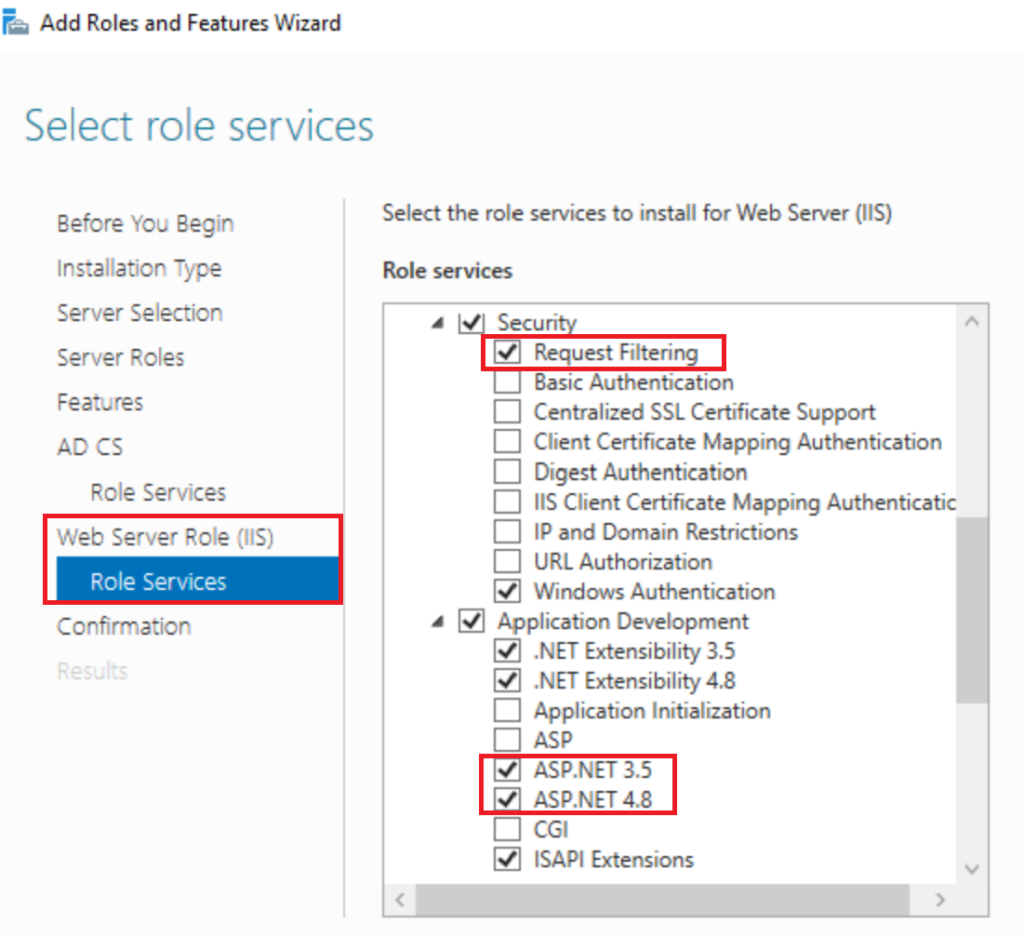
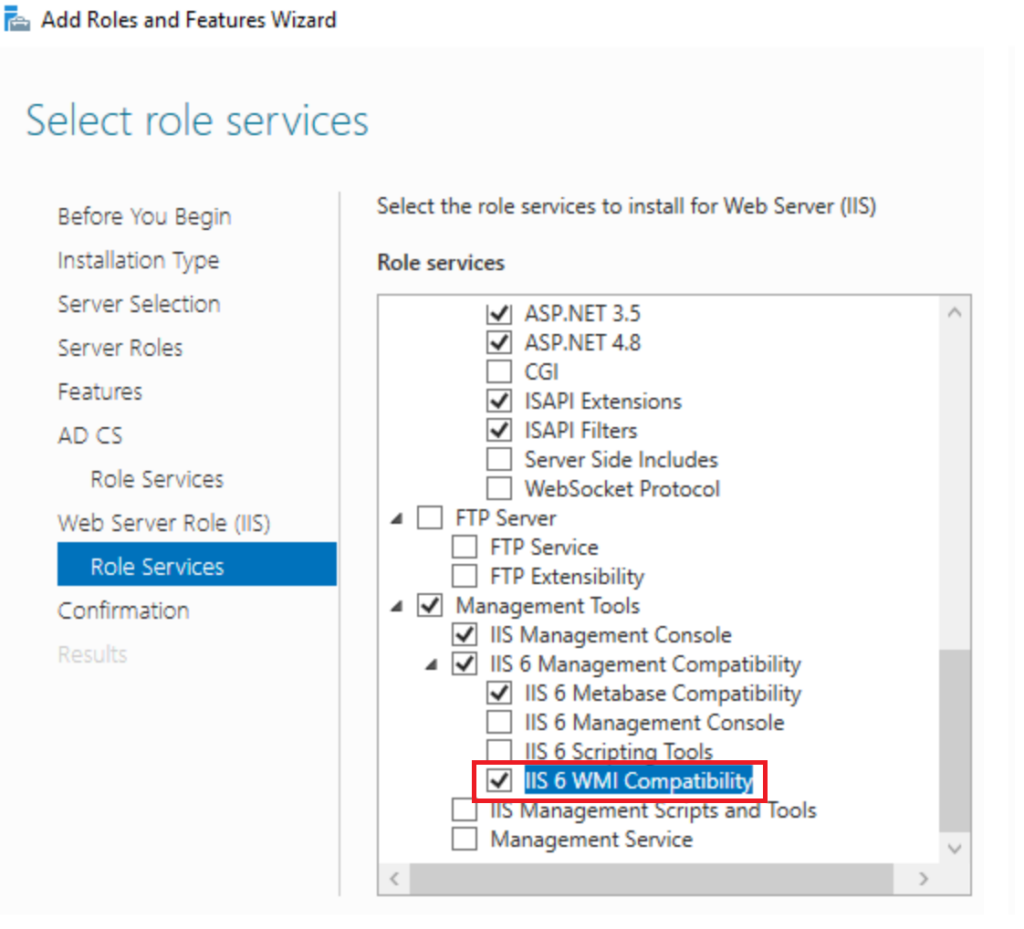
Click Next And Install
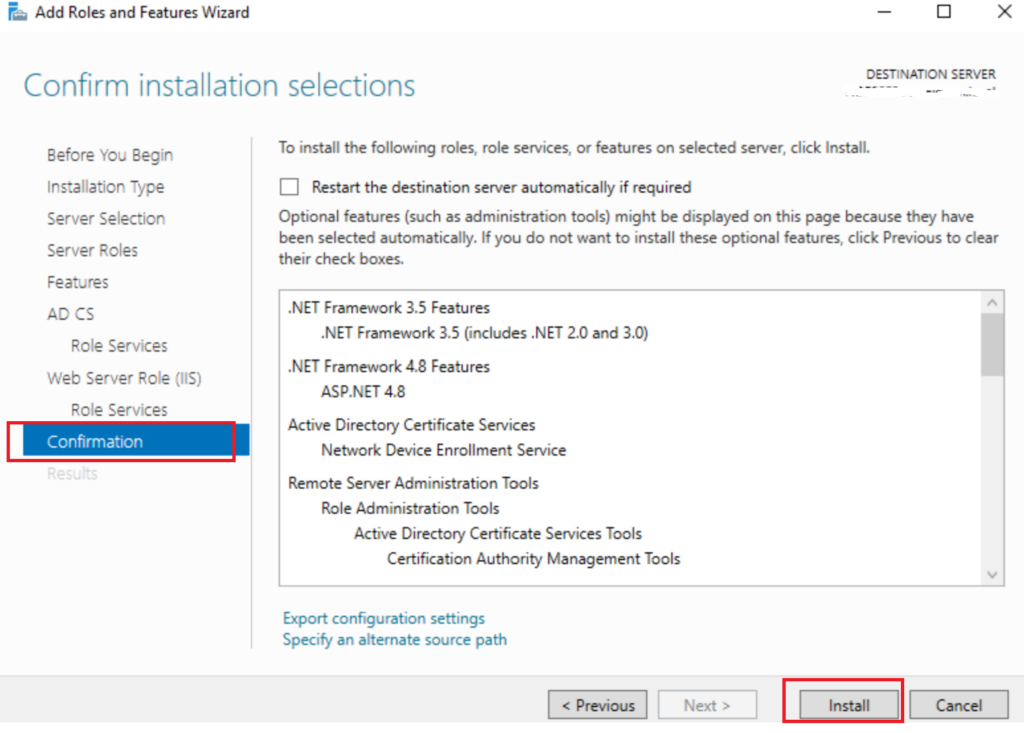
Now that this is complete, close or minimize this page do not setup yet***
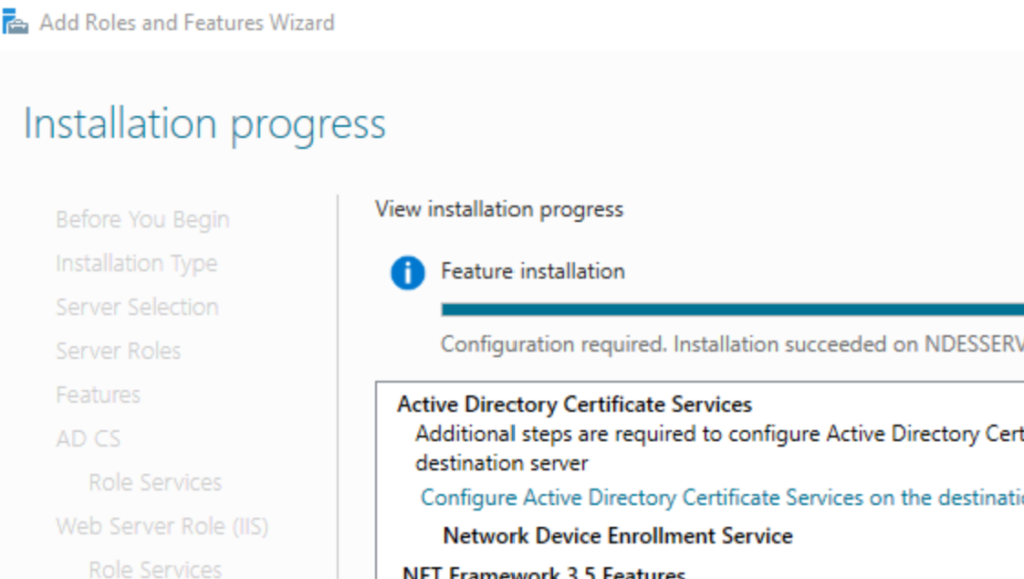
Open Add Server Features again from Server Manager and Add Http Activation for .net
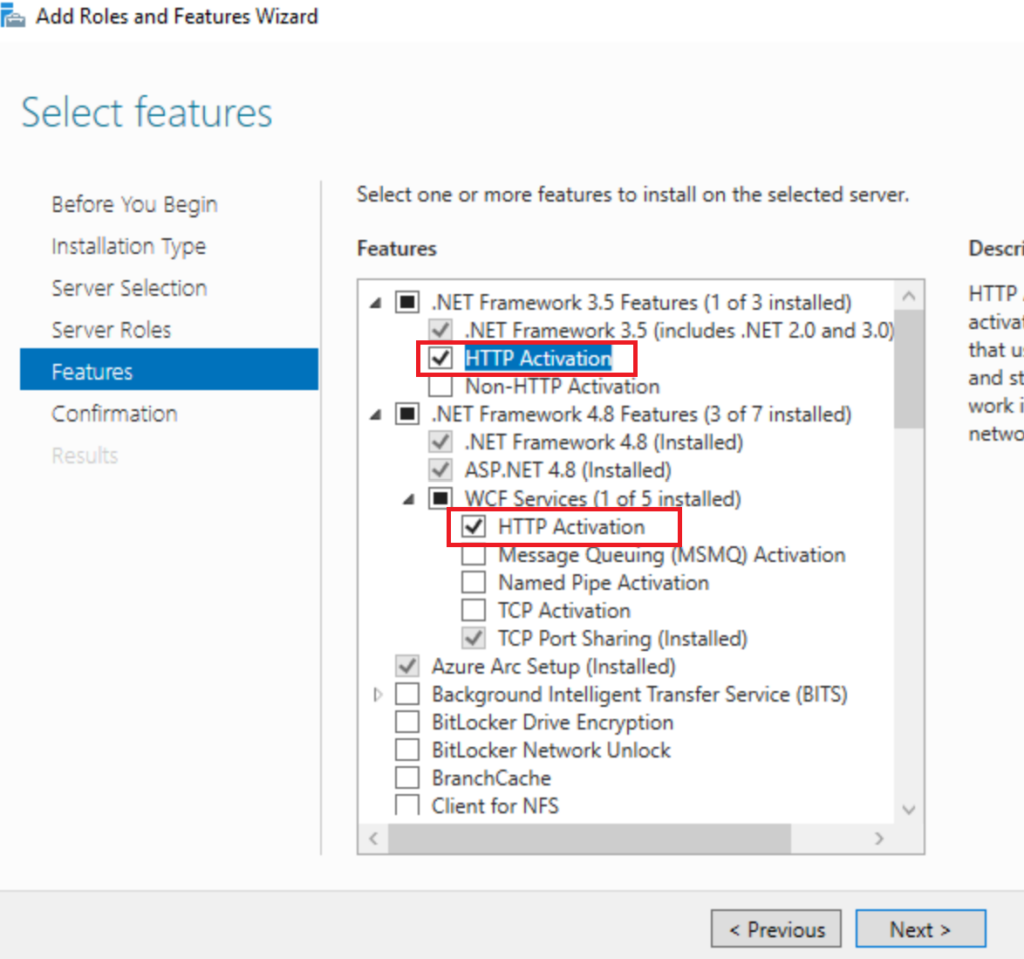
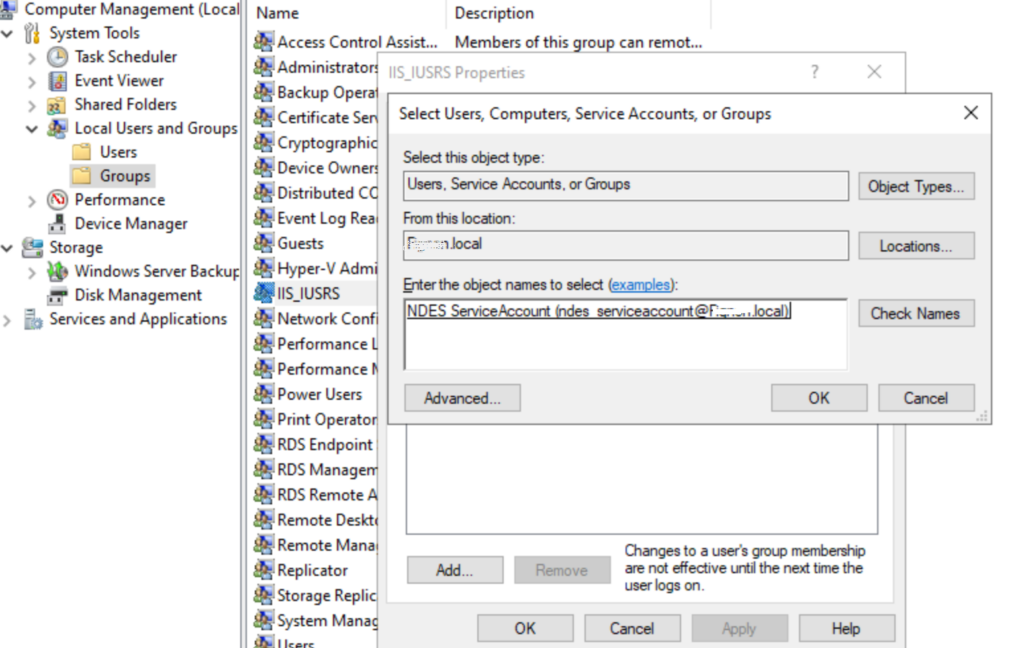
Now Open Administrative tools Computer Management Local Users and Groups IIS_USRS
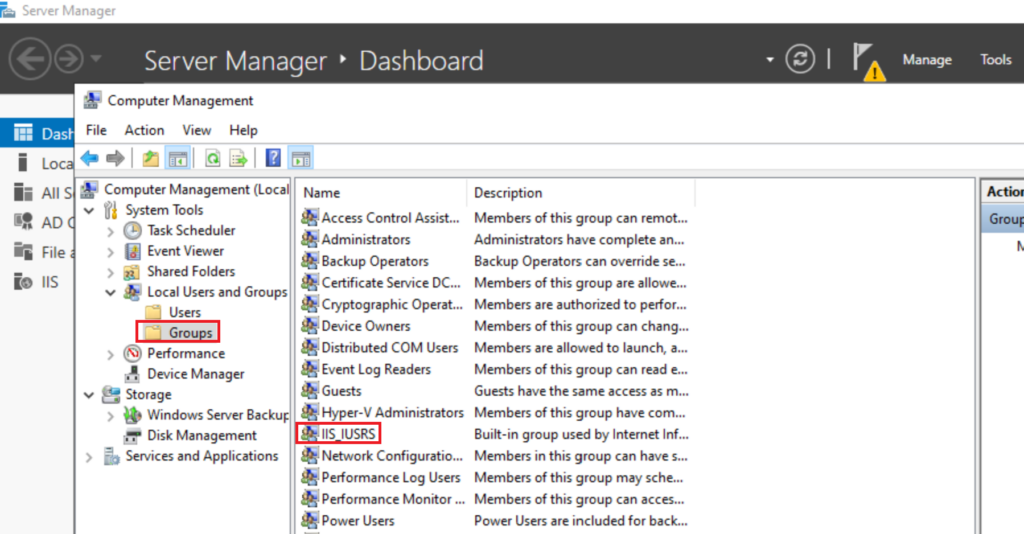
On your NDES server Add the NDES Service account you created to the IIS_USRS Group
You can now request the IIS Certificate for your NDES Server
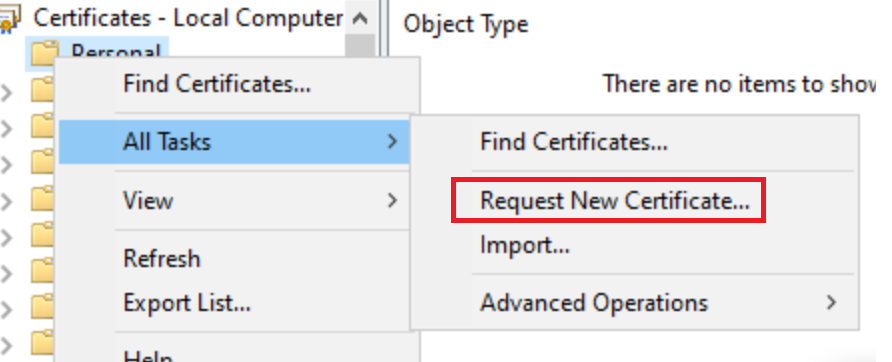
From certlm.msc Request new certificate
Choose your IIS Cert and click More Information is required
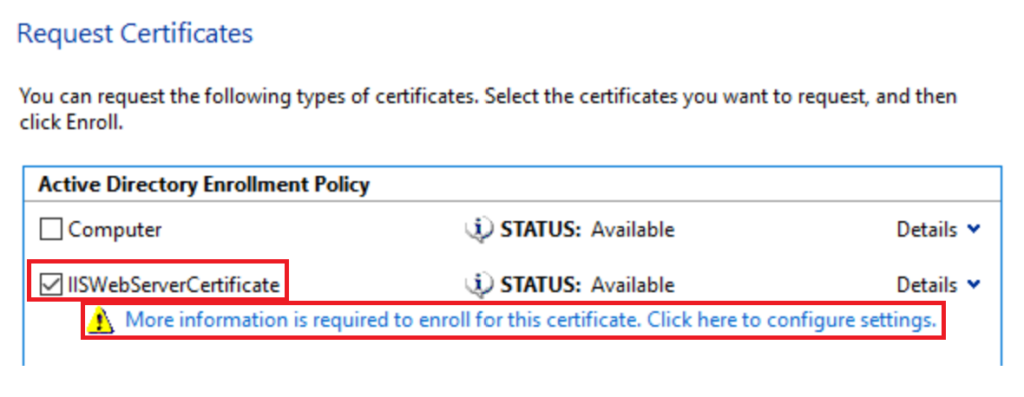
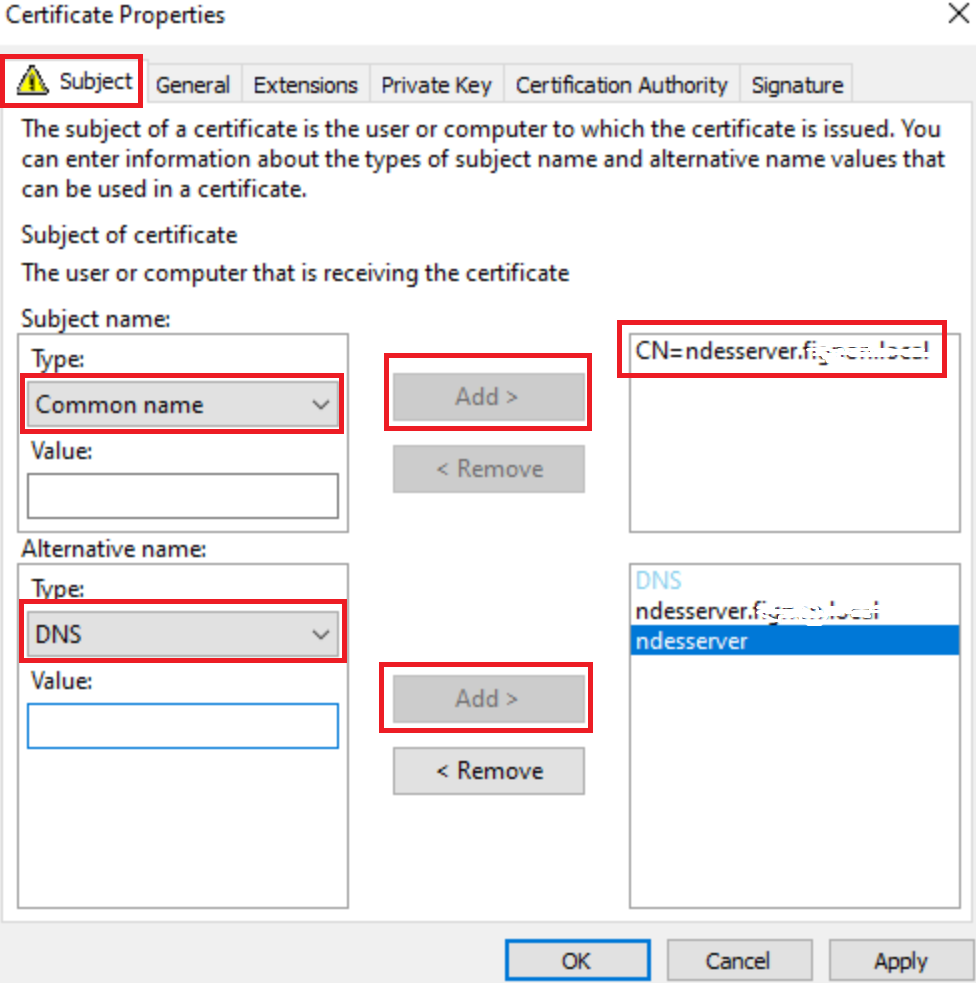
In the Subject Tab add
Common name – the fqdn of your server i.e ndeserver.mydomain.local
DNS NAME – the fqdn of your server and a 2nd entry of just hostname of server
In General add a recognizable name so you can easily distinguish it on your server
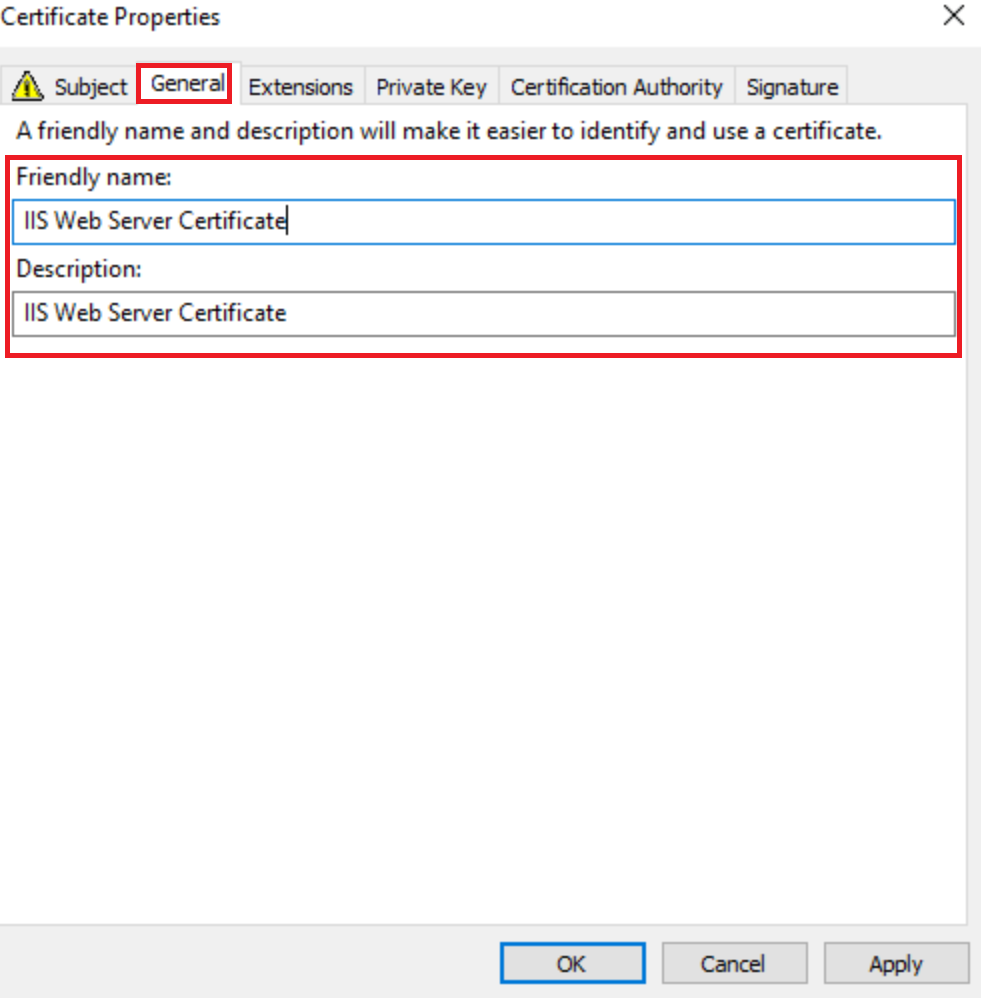
Click Apply and OK
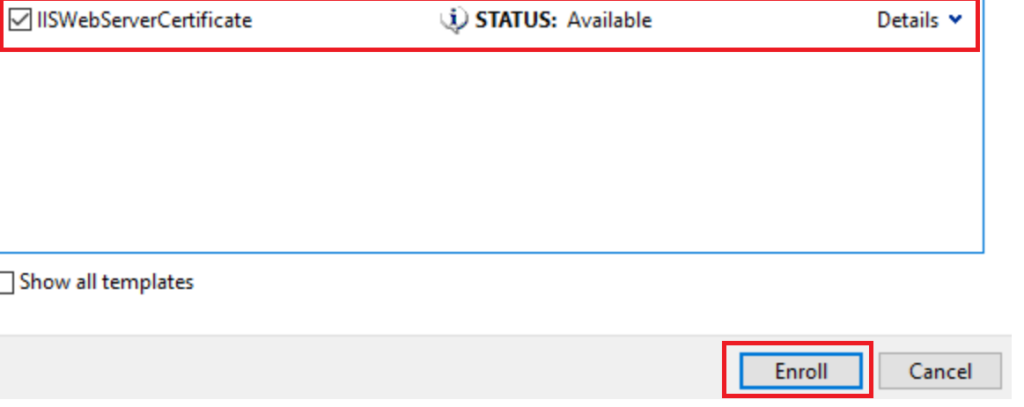
And now Enroll
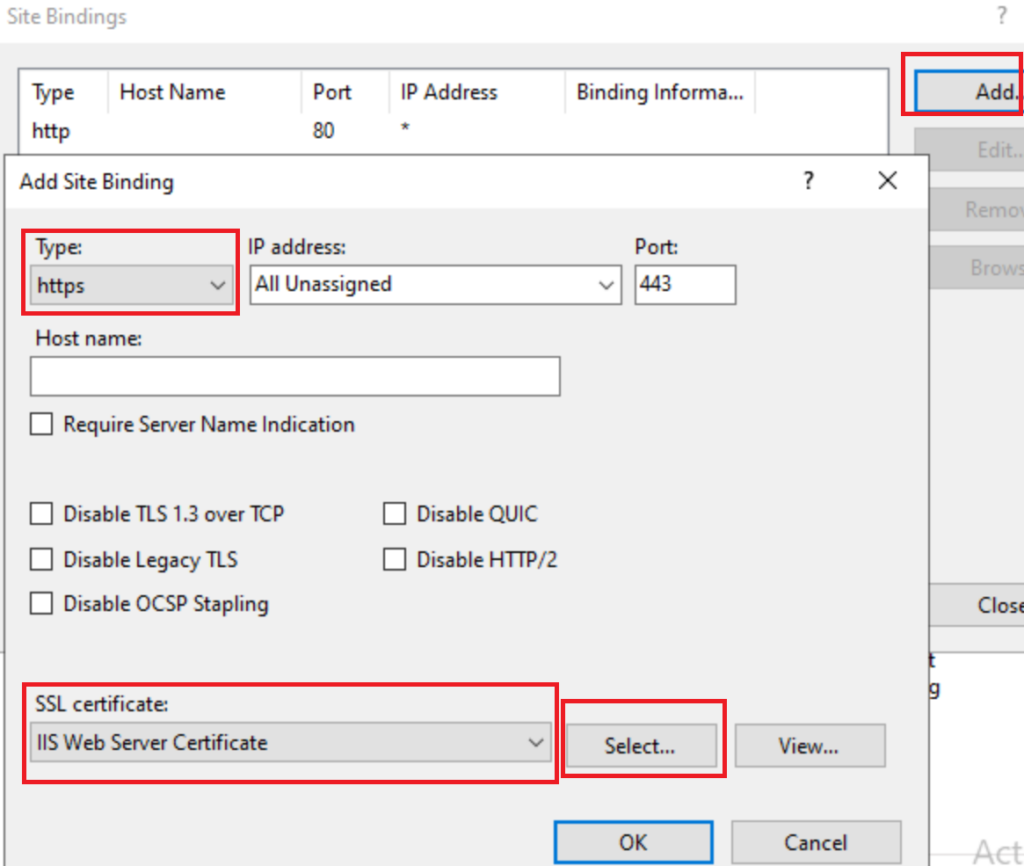
OPEN IIS Manager Default Website Bindings
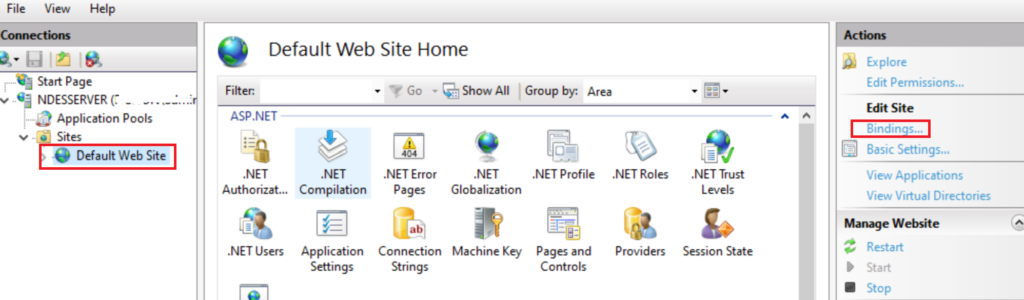
Add https Select your IIS Certificate Web Cert you just enrolled
From Default Website Request Filtering
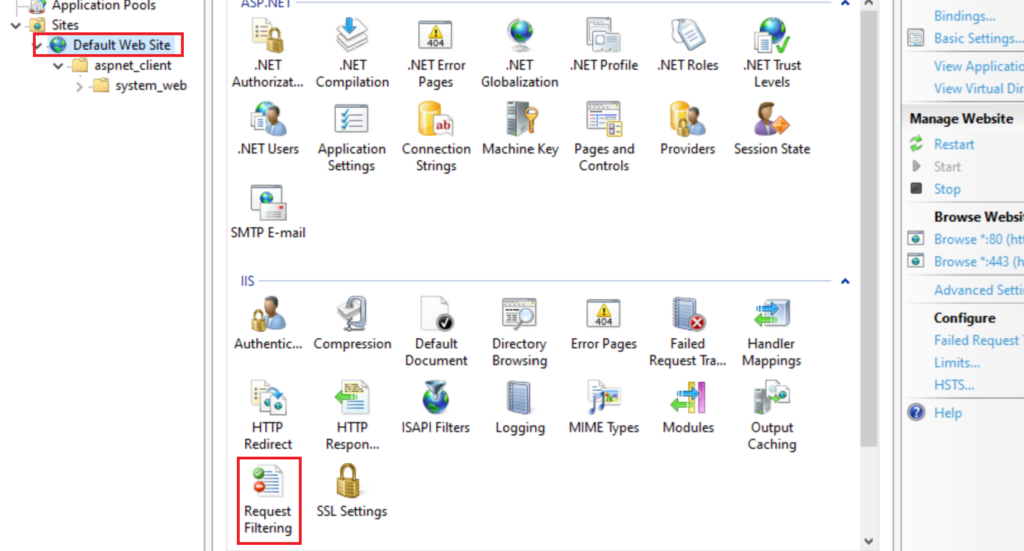
Choose Query Strings Edit Feature Settings
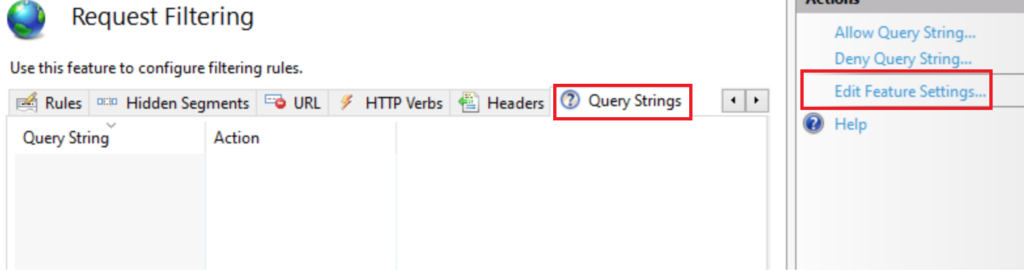
Change these 2 to 65534
Restart the IIS Server (Although we are going to restart this server fully now anyway)
Now is a good time to reboot the NDES Server
REBOOT NDES SERVER
NDES CONFIGURATION
Now that NDES components are in place and you’ve rebooted the server now its ready for configuration
THIS IS WHERE YOU NEED TO BE AN ENTERPRISE ADMIN (WITHOUT ENTERPRISE ADMIN YOU CANNOT SETUP)
Log back into NDES Server with your Enterprise Admin Account
Choose Configure Active Directory Certificate Services From Server Manager
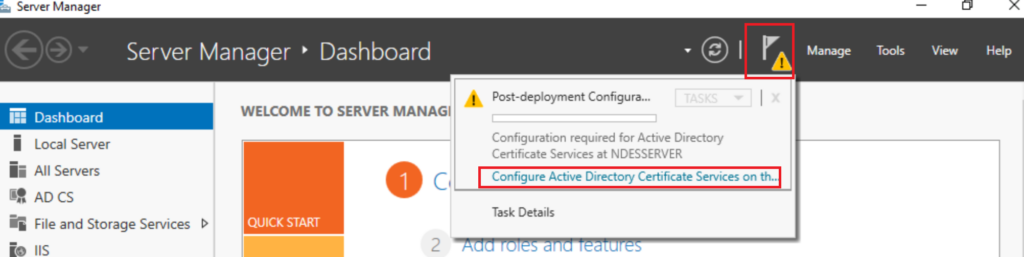
Click Next and On the Role Services choose Network Device Enrollment Service
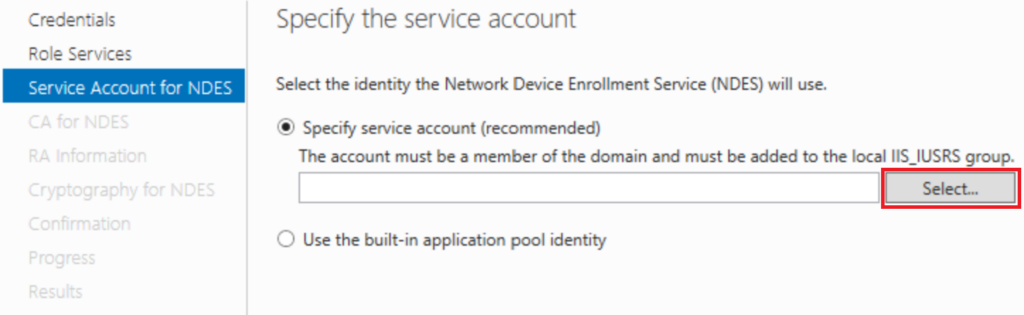
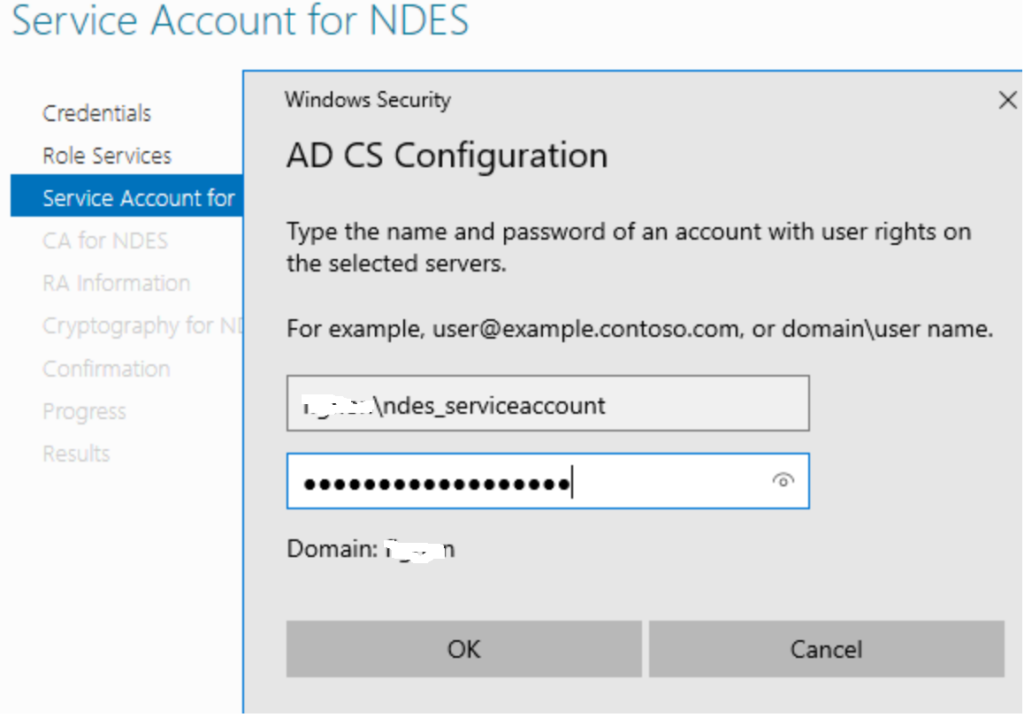
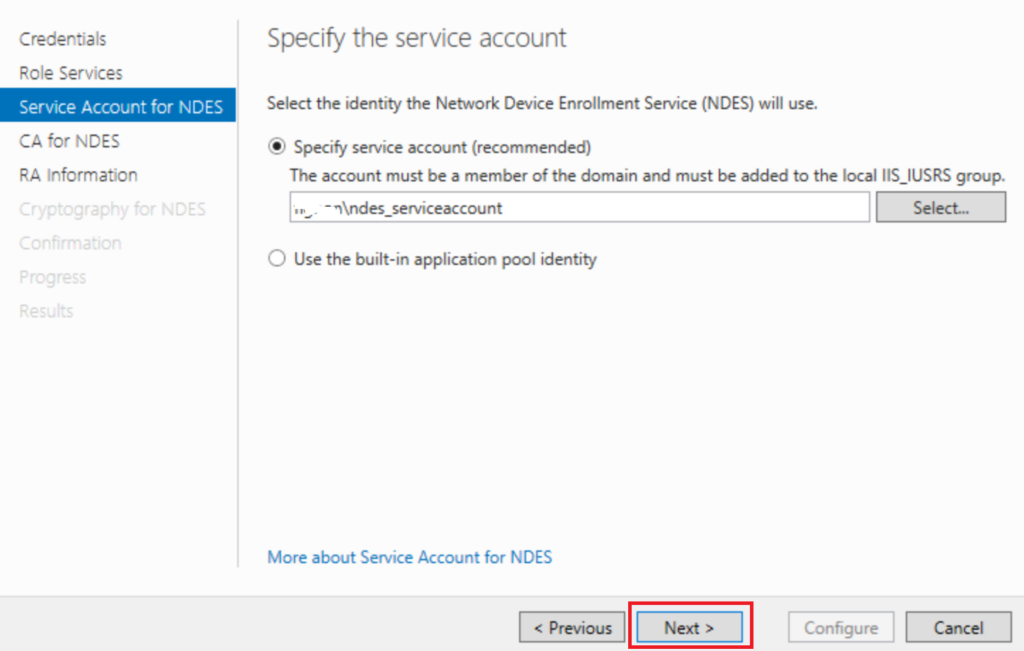
Select an Account this is where we are going to use the NDES Service Account we created earlier and added to the IIS_IUSRS Group
Authenticate with your NDES Service Account
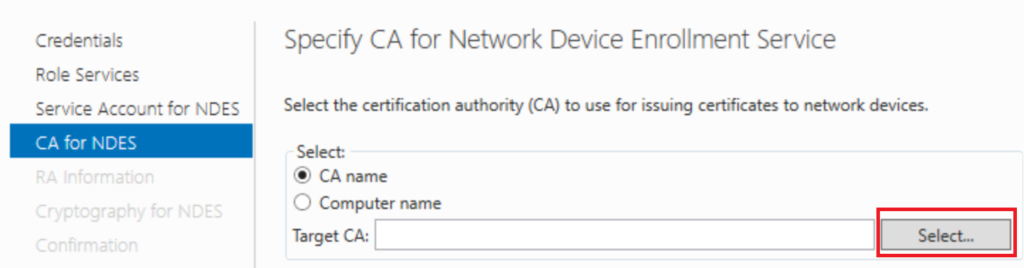
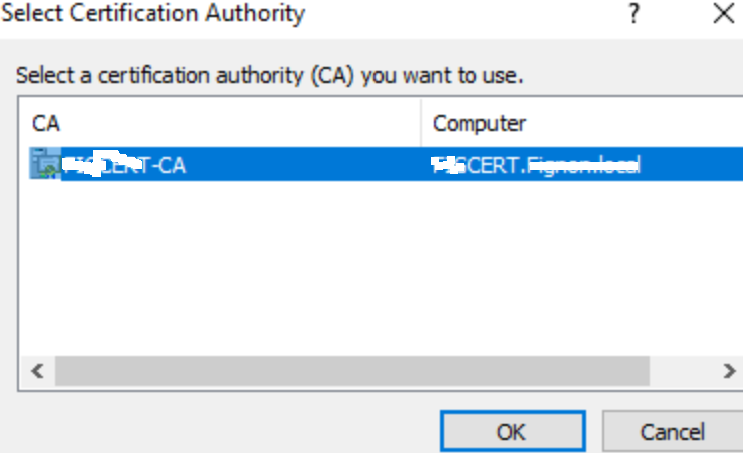
Select your Certificate Authority
You can fill in the Email Country etc but its not mandatory and not filling it out wont affect function
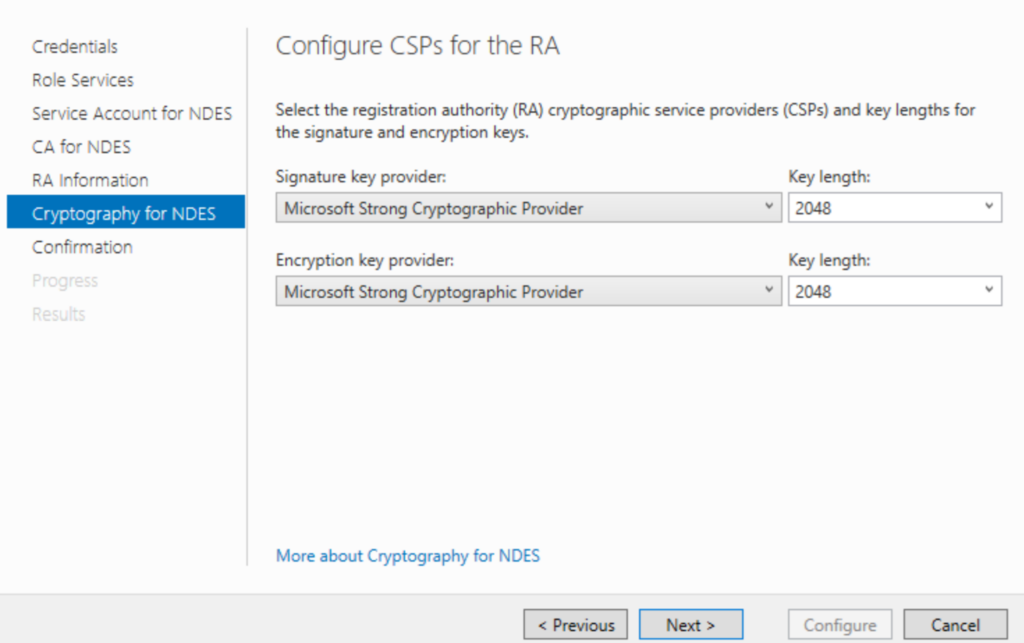
You can leave this on 2048
Finally on the confirmation screen click configure
Now that’s setup open Regedit
HKEY_LOCAL_MACHINE\SYSTEM:\Software\Microsoft\Cryptography\MSCEP
and change each of these 3 template entries to your NDES Certificate Template you made
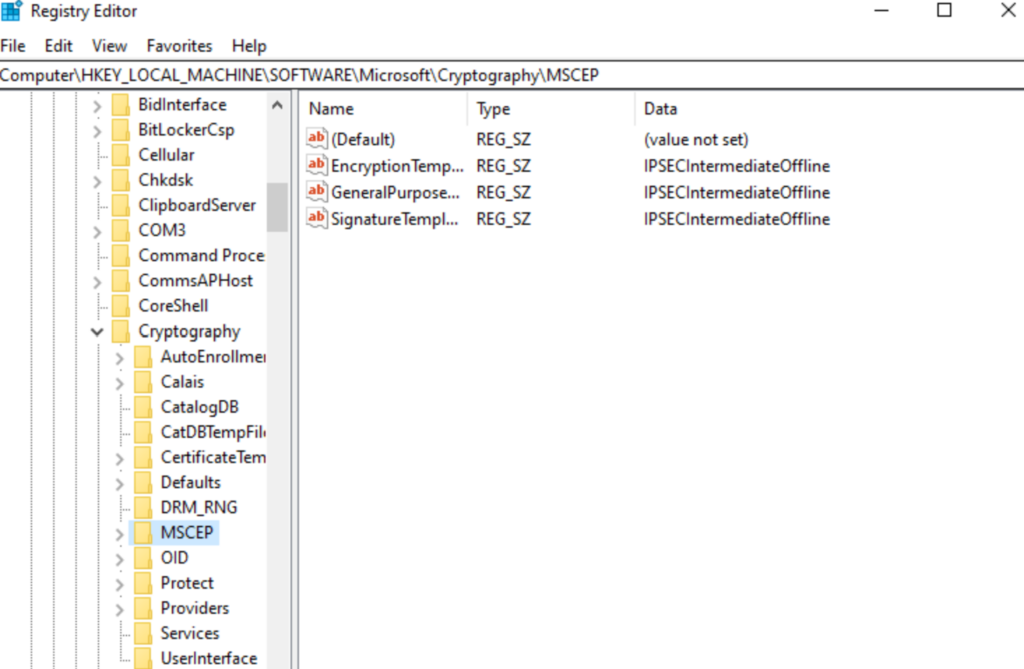
So It should look like this
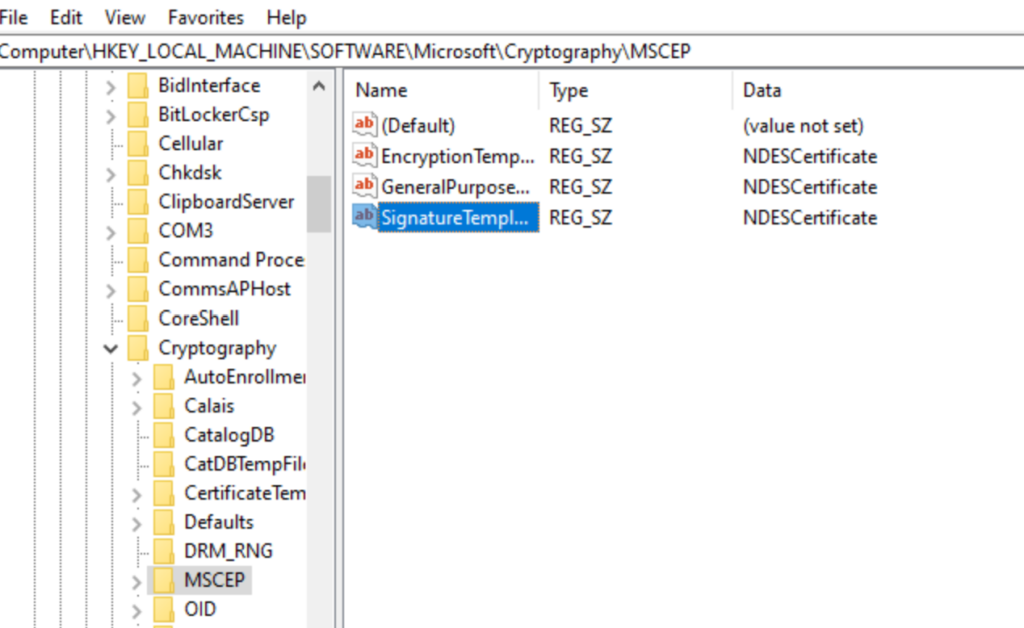
Why?
Because thats what our NDES Cert Template was called
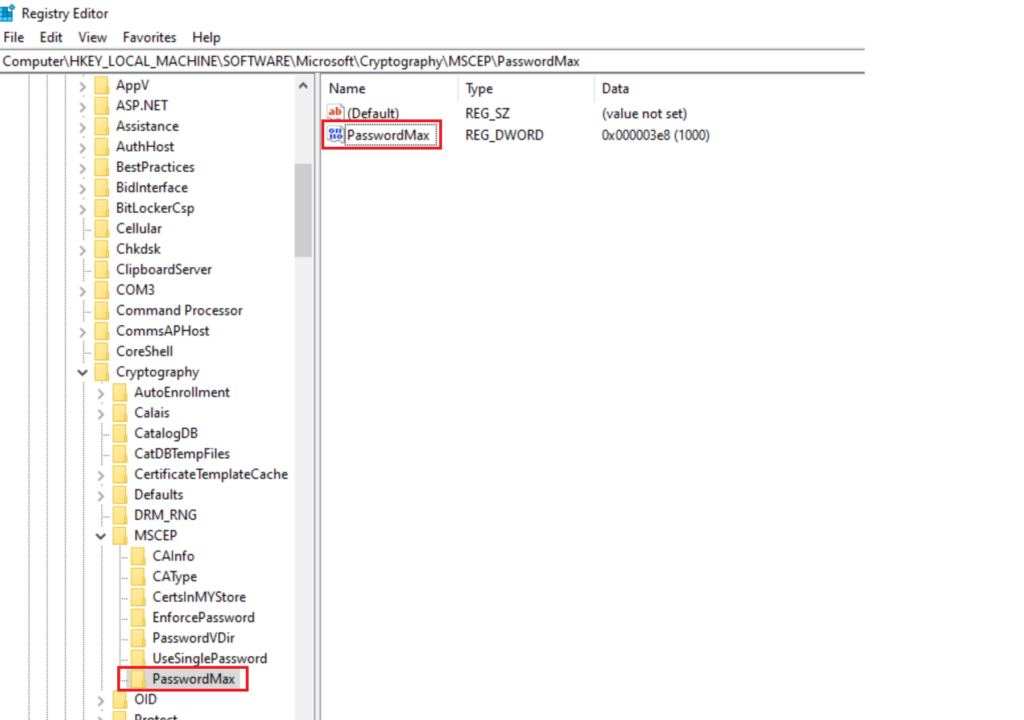
Open HKEY_LOCAL_MACHINE\Software\Microsoft\Cryptography\MSCEP
Add a key PasswordMax with a Dword Password Max Decimal of however many machines you think might contact the server at once in most environments 1000 is plenty
Service Principal
You may need to setup an Service Principal Name (SPN) although for this setup unlikely its needed
- Use the Setspn command syntax of:
Setspn -s HTTP/<computerfqdn> <domainname\accountname>when entering your commands. For example, your domain isFabrikam.com, your NDES CNAME isNDESFARM, and you’re using a service account namedSCEPSvc. In the example, you would run the following commands.Setspn -s HTTP/NDESFARM.fabrikam.com fabrikam\SCEPSvcSetspn -s HTTP/NDESFARM fabrikam\SCEPSvc
- Then disable IIS Kernel-mode Authentication for the site.
You can again now Restart IIS but preferably now as we have changed some reg keys give the Server a reboot
Reboot Server
Once rebooted you can test if MSCEP is behaving as it should
Go to
http://myndesserver.fqdn/certsrv/mscep/mscep.dll (enter your internal fqdn name of your ndes server)
You should get a page like this
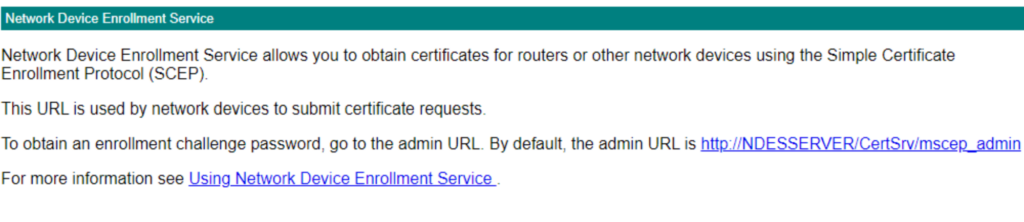
http://myndesserver.fqdn/certsrv/mscep_admin (enter your internal fqdn name of your ndes server
You should get a login prompt
Intune Connector setup
We can now add the Intune connector
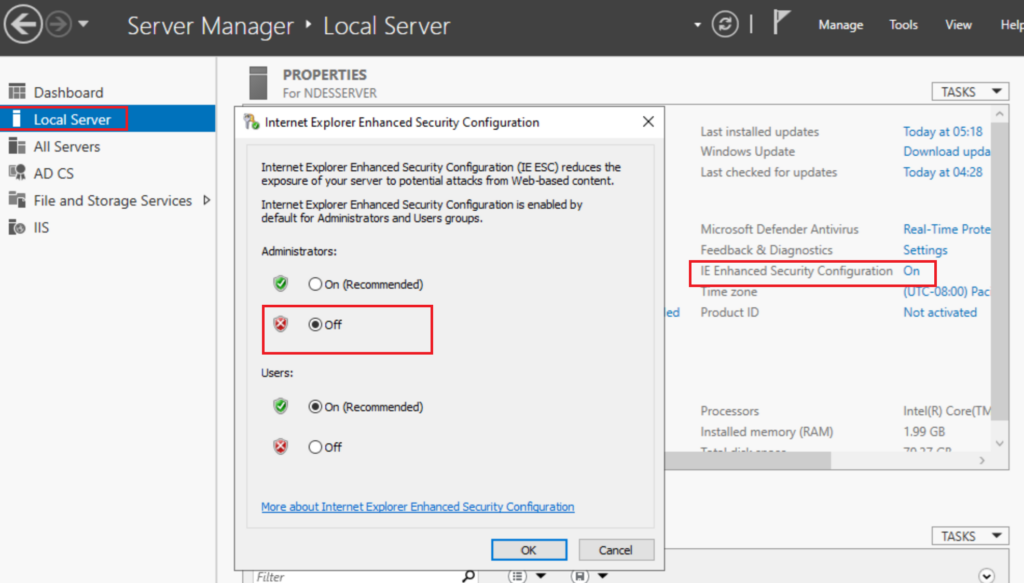
On you NDES server turn off IE Enhanced security, we need to do this as the connector login will get blocked, we can turn it back on again once the connector is installed
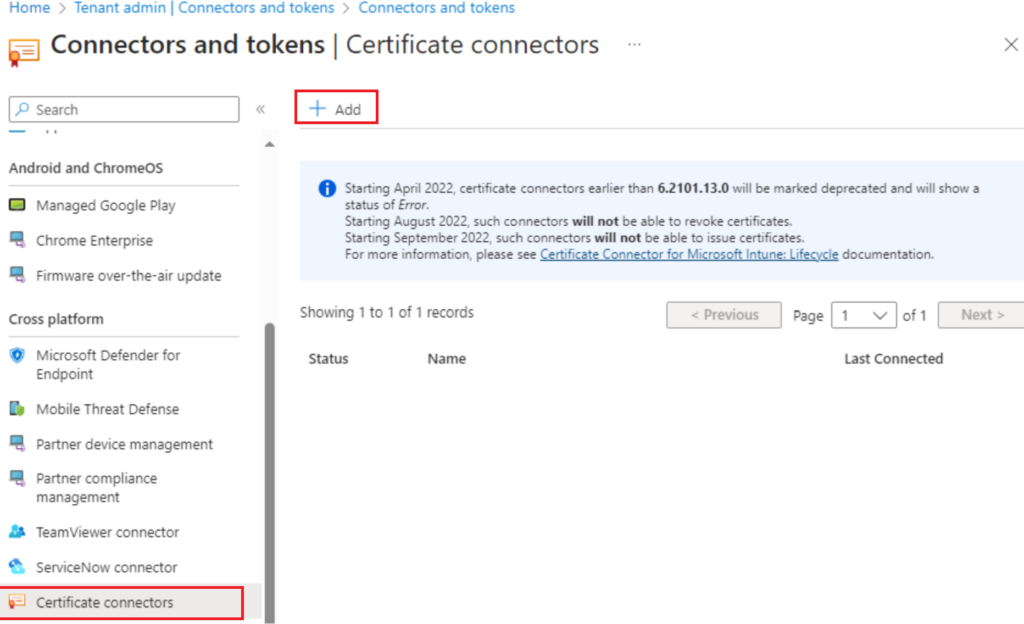
Now from Tenant Admin > Connectors and Tokens Certificate Connectors > Click Add to Download the Intune Certificate Connector
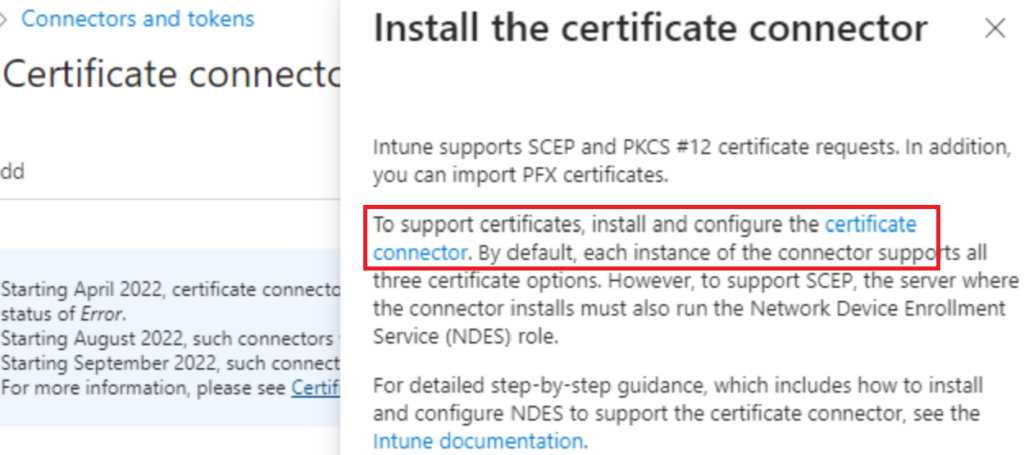
Very Important I could not get the setup to complete if I chose to use the Domain Ndesserviceaccount as the login, till I added the Service account to login as a service from secpol.msc
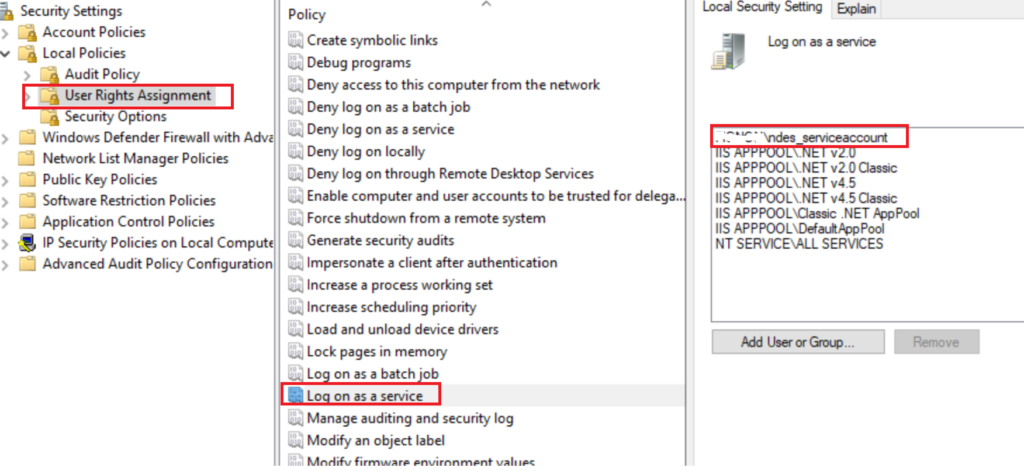
Run the exe from your NDES server
very Important run as Admin otherwise it fails at last step on rights
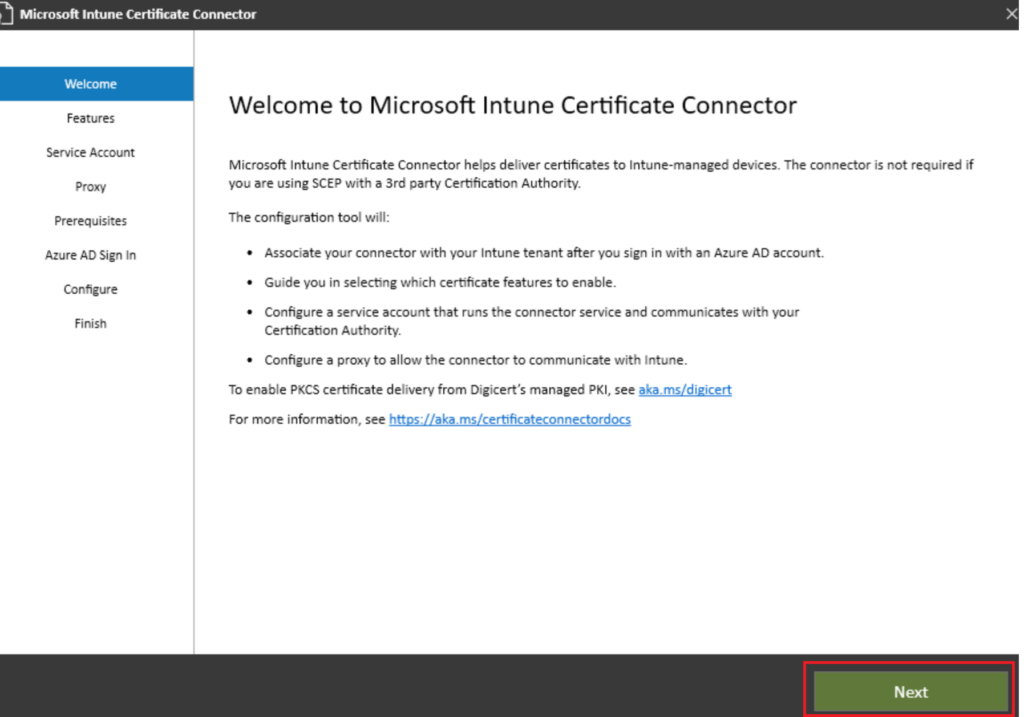
Choose SCEP and certificate revocation (for revocation this will depend if you gave NDES rights to revoke a little more on this at the end)
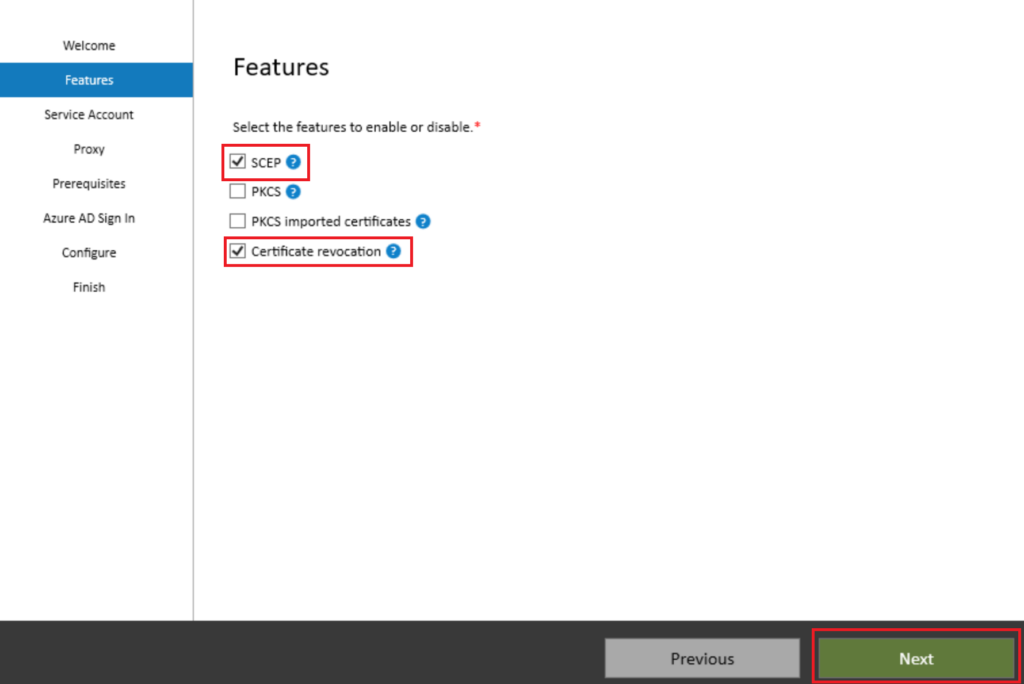
For the account choose your service account
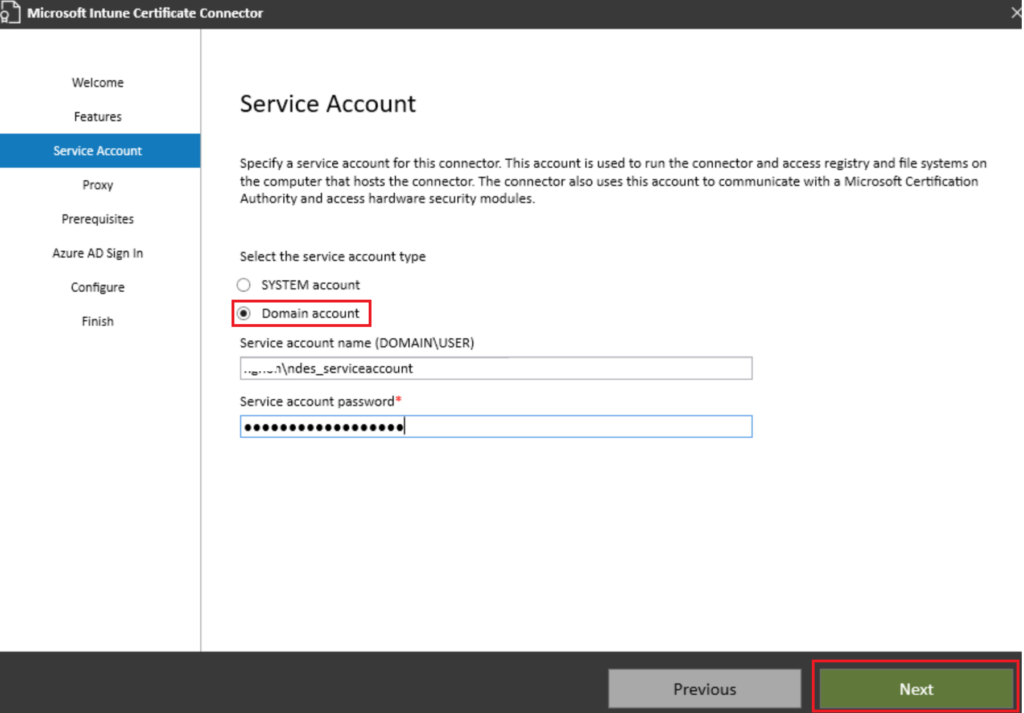
I’m not using a proxy
Hopefully this is all green
Now sign in with your Intune admin / Azure Admin Account (Needs either Global Admin or Intune Service Admin Role)
Finally we are done
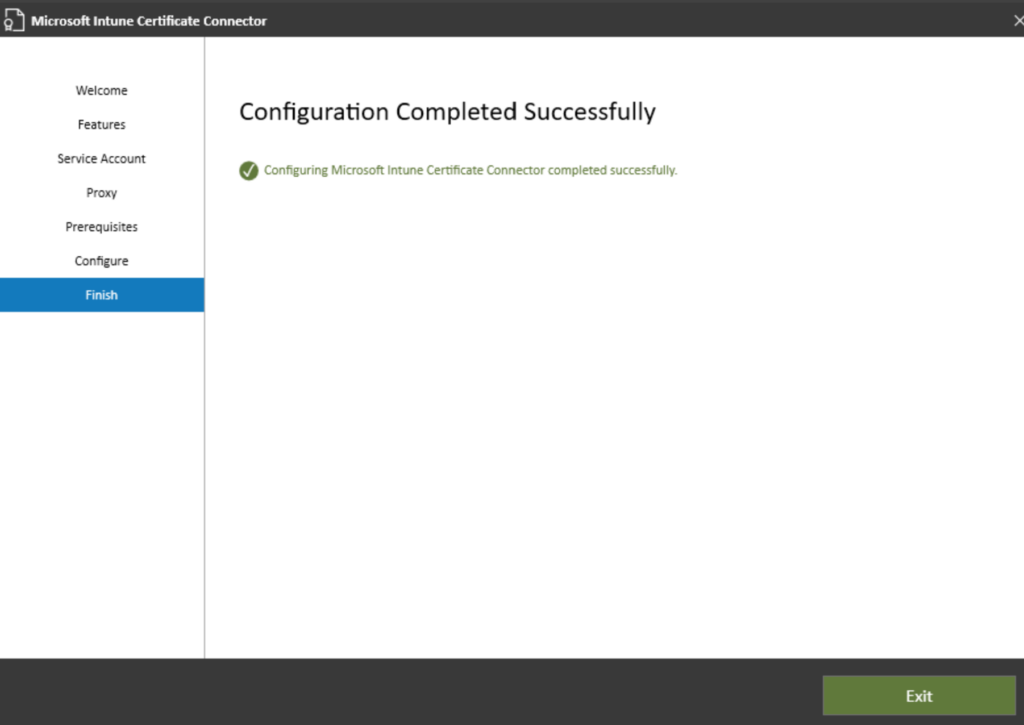
Exit and give server a final reboot
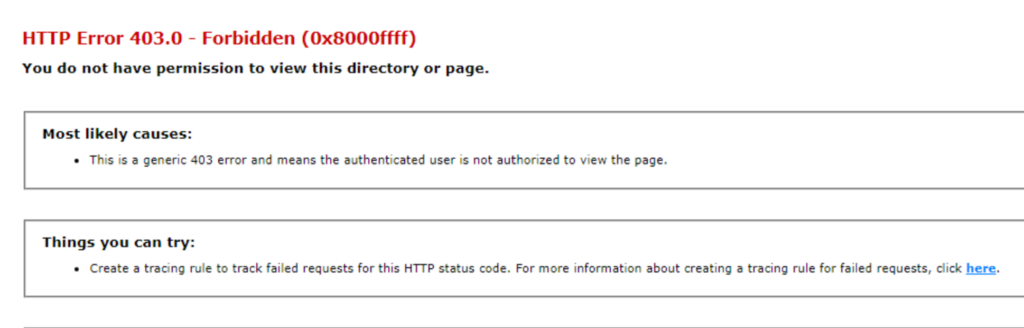
Now when you visit
http://myndesserver.fqdn/certsrv/mscep/mscep.dll (enter your internal fqdn name of your ndes server)
You should get 403 (this is now working correctly and the app pool has been secured)
Proxy Setup
Now that the server is setup we can now setup a proxy server so that its safely accessible from the Internet and your Intune workstations can get a cert wherever they are located
I’ve chosen this to be setup on a separate server I’ve called this server NDESProxy and its a domain joined Windows2022 Server as well
It can be setup on the NDES server if you wish but I’ve kept it separate
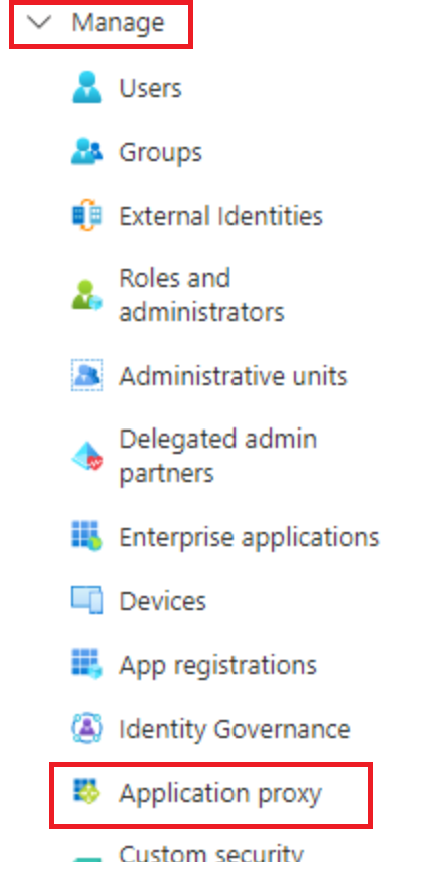
From Azure Portal or Entra Portal
Choose Application Proxy
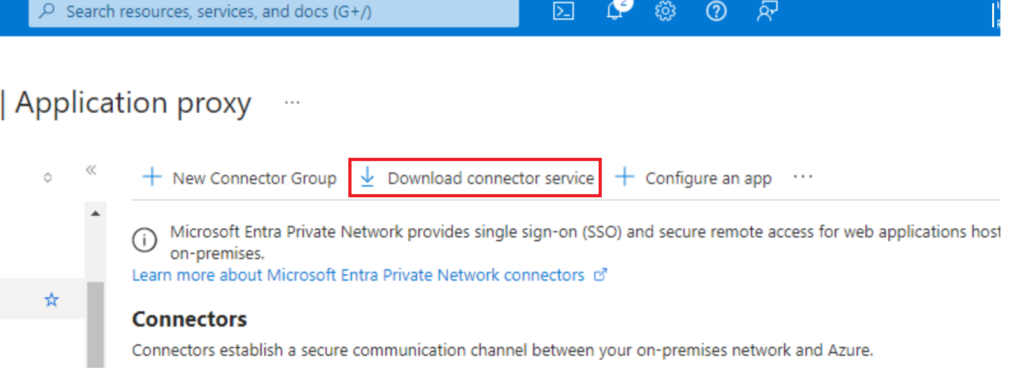
Run the Setup
Sign in with a Global Admin Account
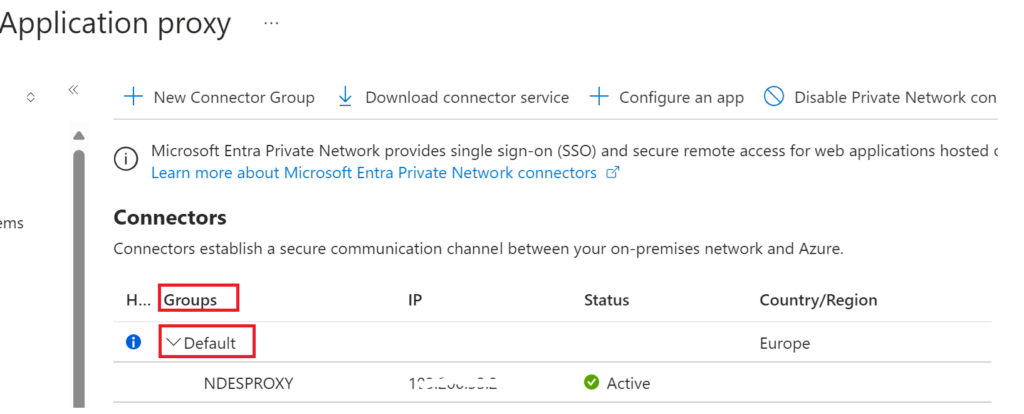
Setup completes and we can now see its in a Default Group
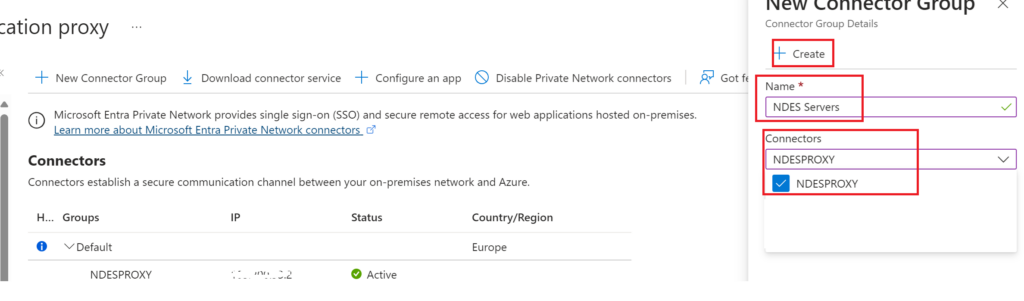
So lets setup a group for this I’ve named this NDES Servers and added the NDESPROXY
One thing you may notice is currently there is no app assigned to this
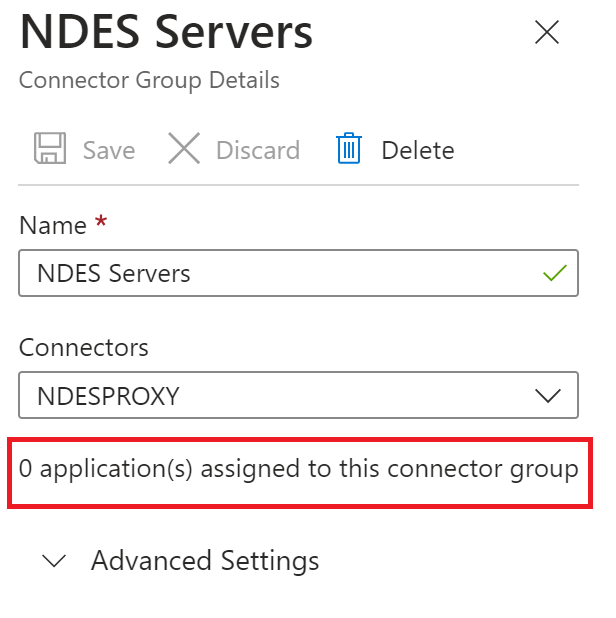
So now go to configure an app
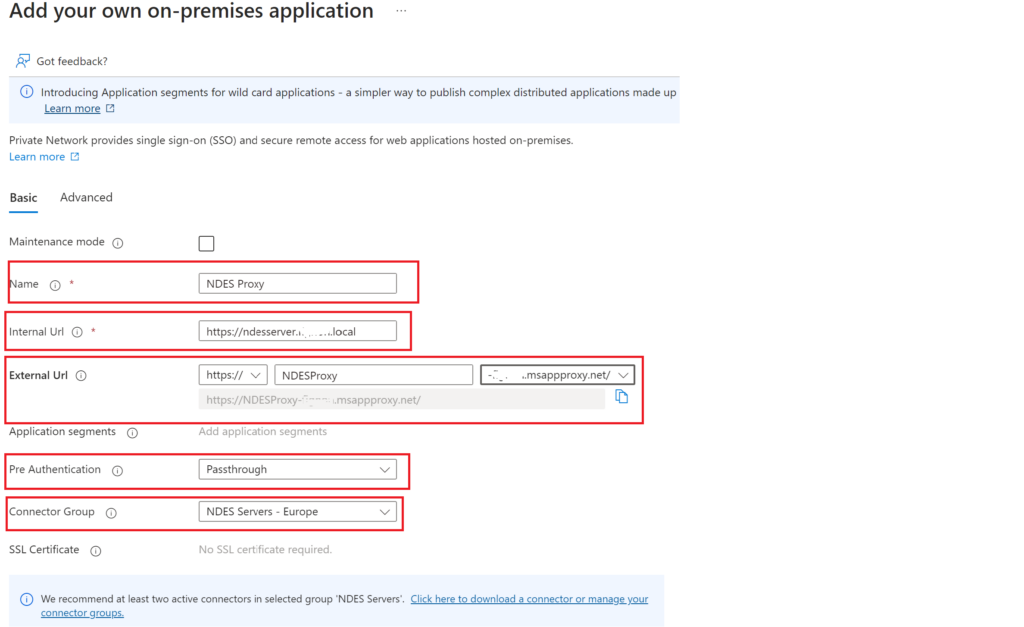
Name: you can choose a relevant name for the app
Internal URL: is your Internal FQDN of you NDES server
External URL: what do you want to get to it by, it will add an msappproxy.net address ie https://ndesproxy-mydomain.msappproxy.net,
There are other options of domain suffix and you can even use your own domain name but then youd have to put certs on the app proxy server with the dns entries in
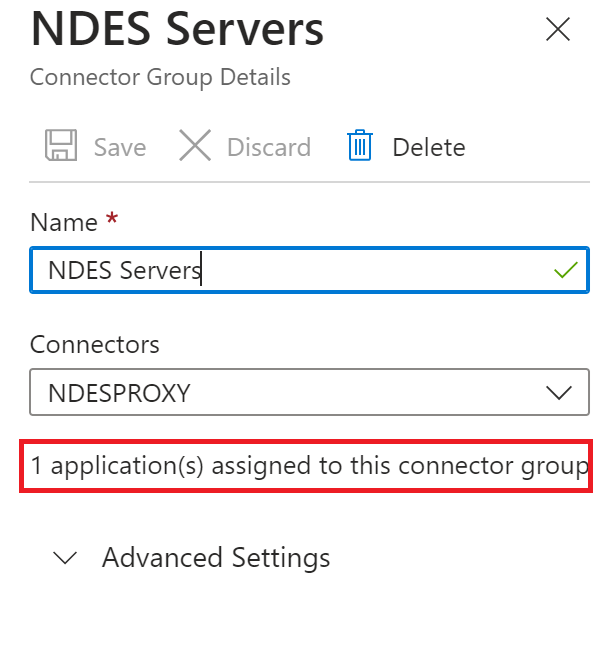
Now we can see an App is assigned
We are now done for all the infrastructure one test you can do now is go to your app proxy address from a web browser and this should be what you get from http://myndesserver.fqdn/certsrv/mscep/mscep.dll (enter your internal fqdn name of your ndes server)
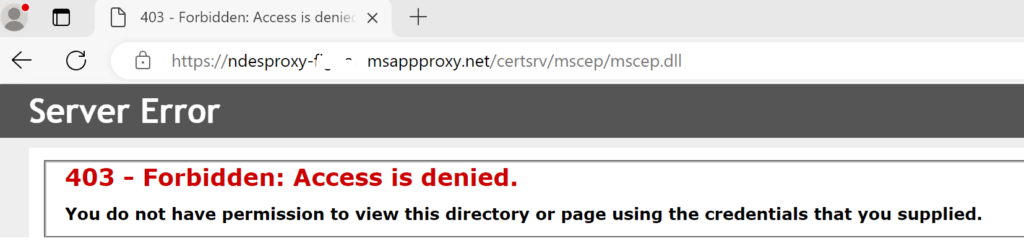
Intune Certificate setup
Now last thing is to setup your Intune certs
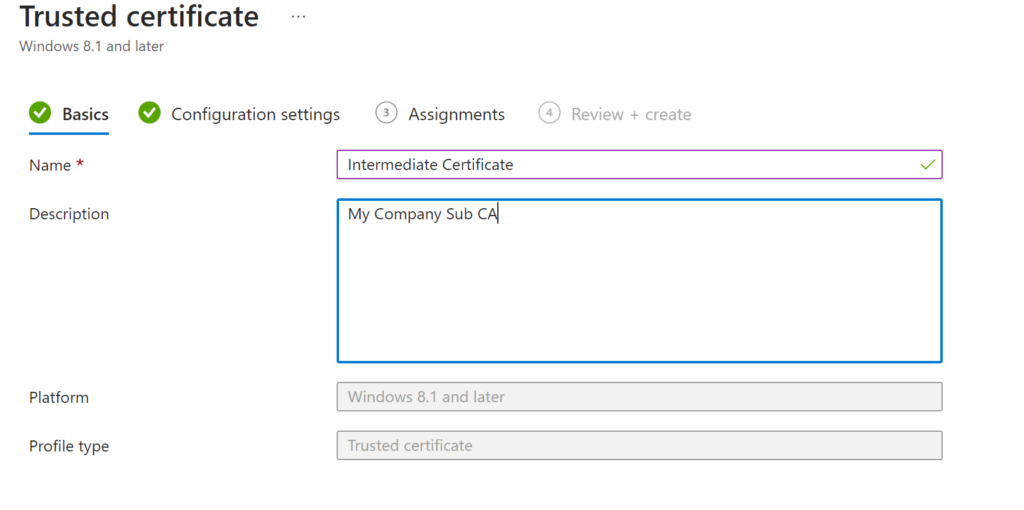
First from one of your servers export the Root Certificate and Intermediate / Subordinate Certificates (If you use Subordinate certs as well
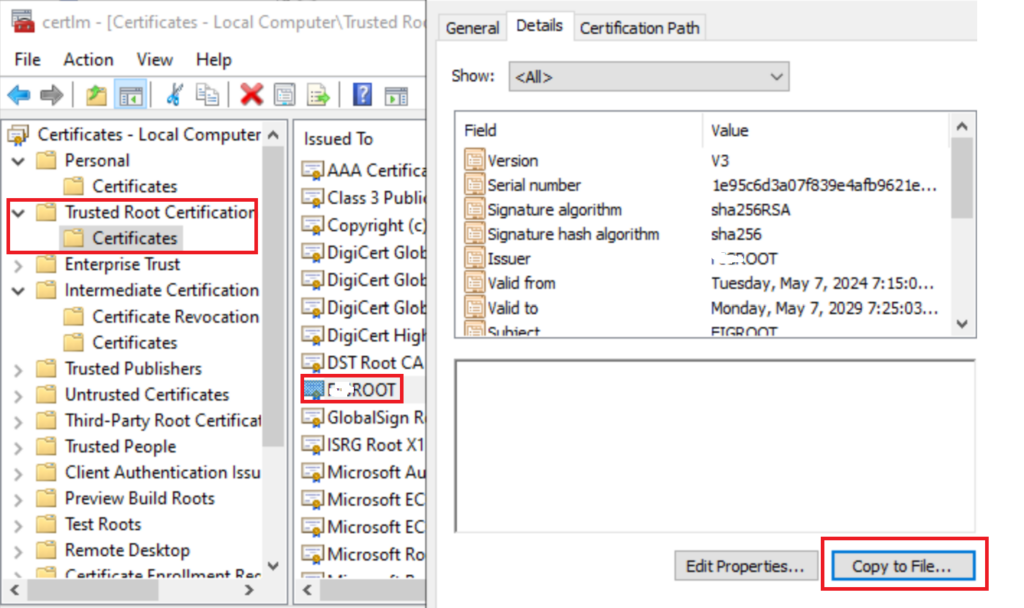
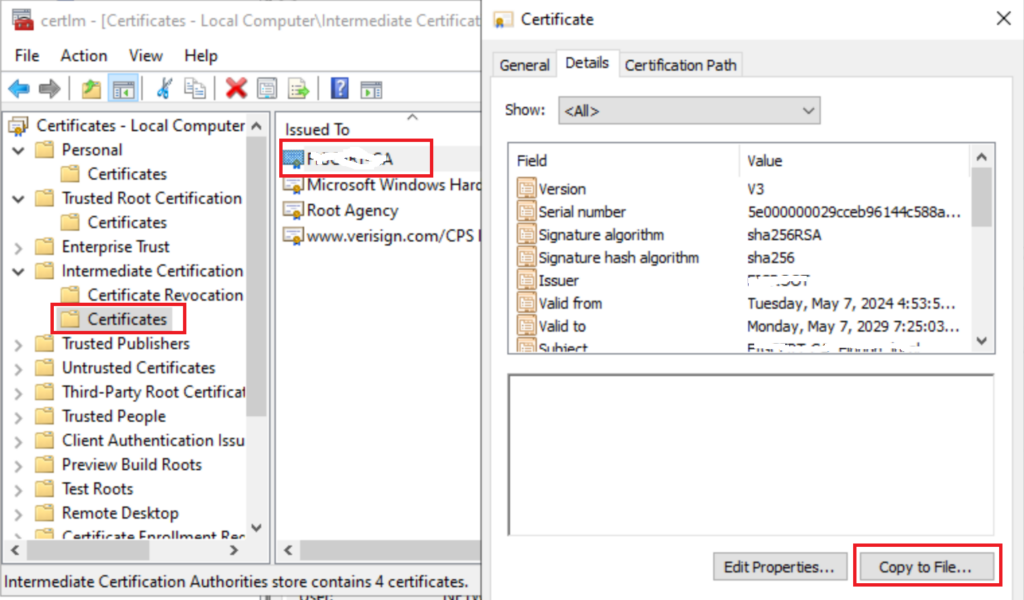
Now go to Intune Console > > Device Configuration > New > Trusted Certificates
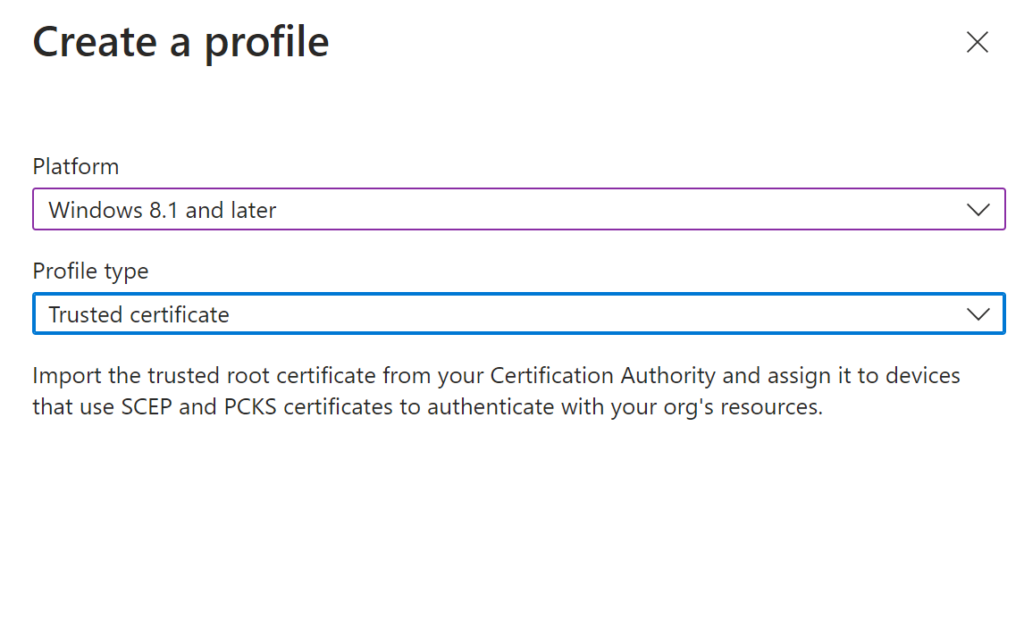
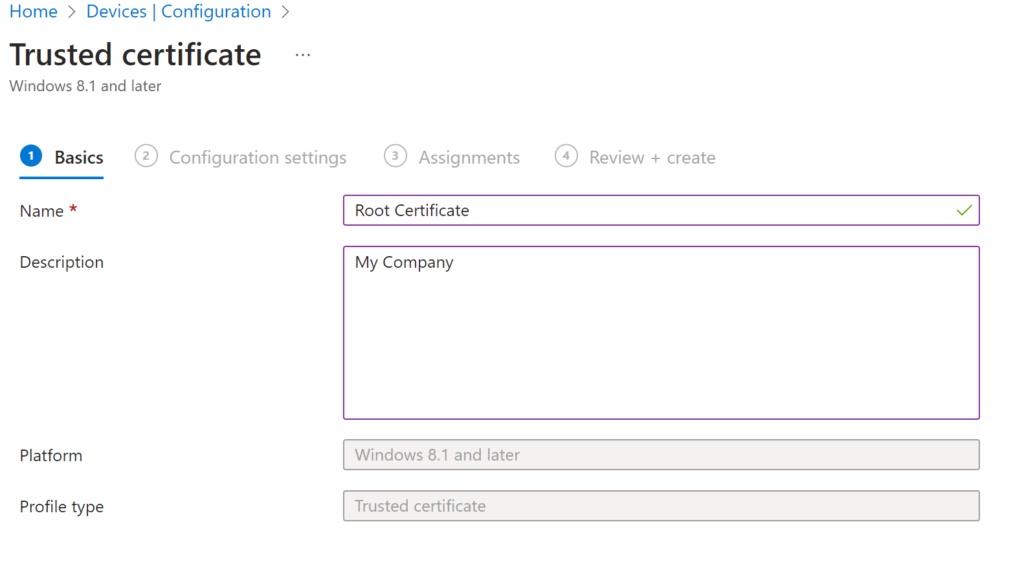
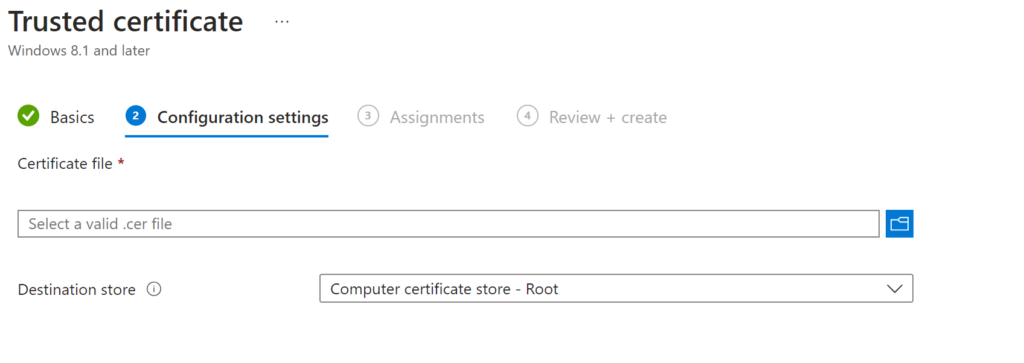
Add Your Root Cer file you just downloaded
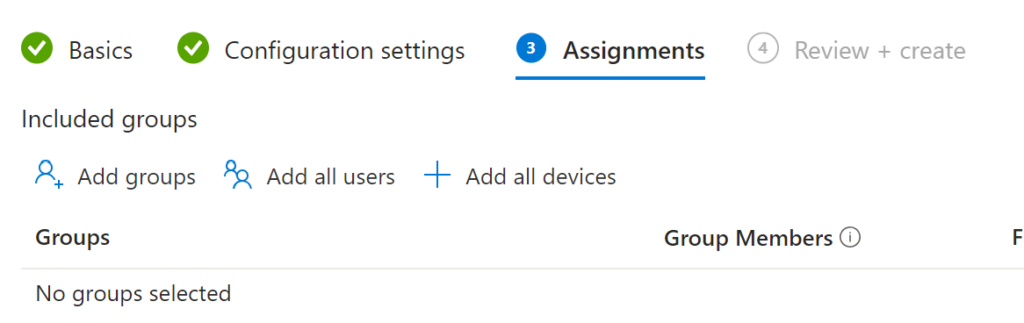
And now assign it to a group (I prefer using device groups for these)
Now do another but this time for your SUB / Intermediate Certs
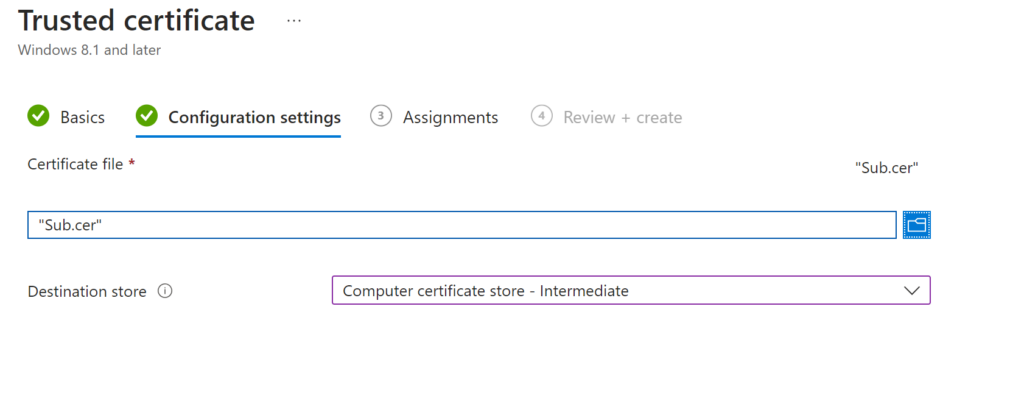
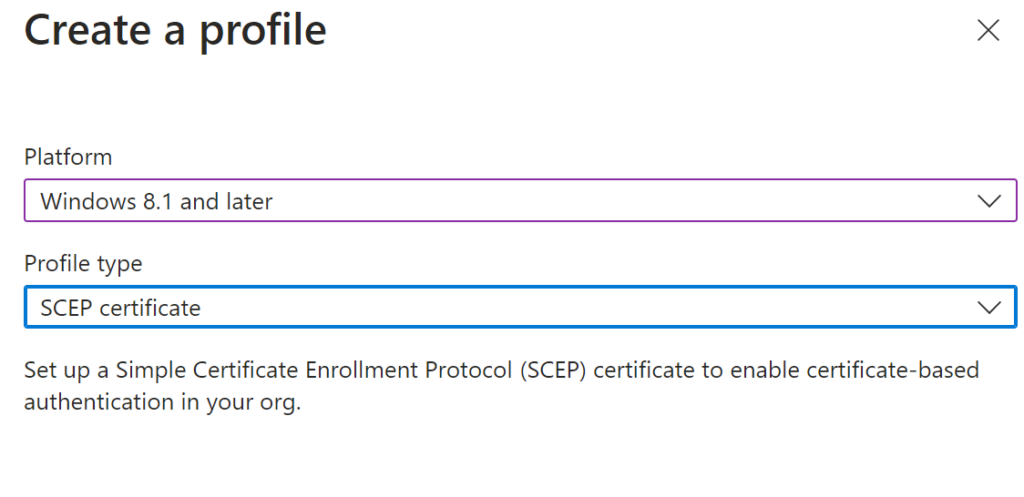
Now Create a Profile for your actual certs that will come from your PKI / NDES
New Profile > SCEP Certificate
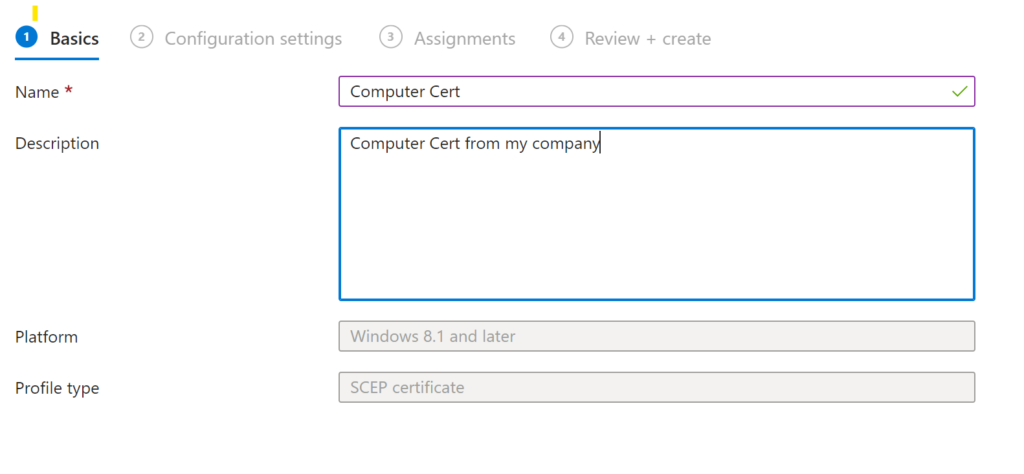
I’ve chosen these settings: Things of note
URI: IntuneDeviceID://{{DeviceId}}
Validity Period: Be very careful not to set this above what you have set in your NDES Certificate as it will fail to deploy if you do
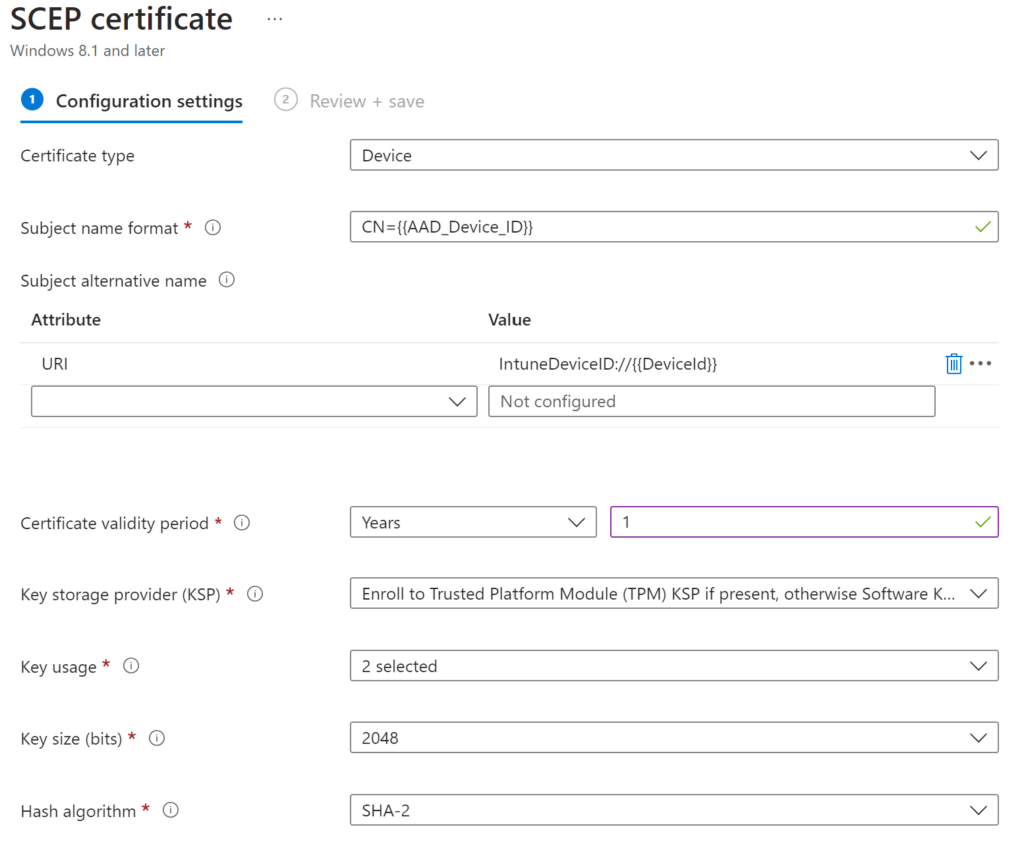
Root Certificate: Choose your Root Cert you do not need to enter Subordinate Intermediate in here
Extended Key Usage: Ive Chose this as a Client Auth Cert
SCEP Server URLS: This is where you can now Add Your SCEP APP Proxy Address
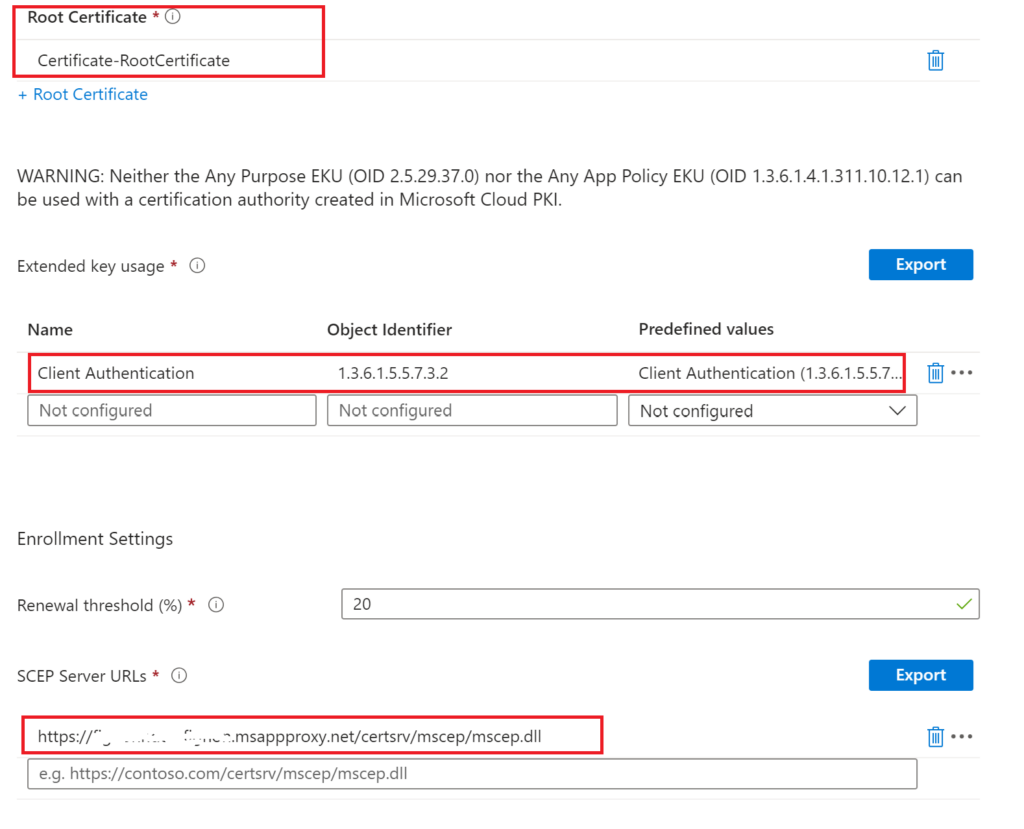
Deploy to your Users or Devices (Again I prefer Devices for this)
RESULT
We Have a cert on our workstation that’s come from our internal PKI through NDES, and Proxy
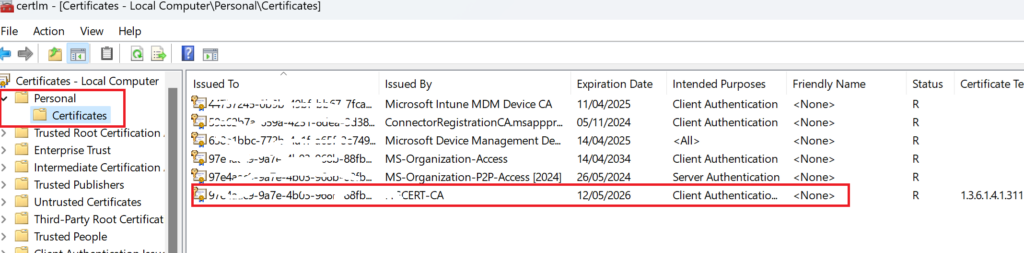
Extra Optional Settings
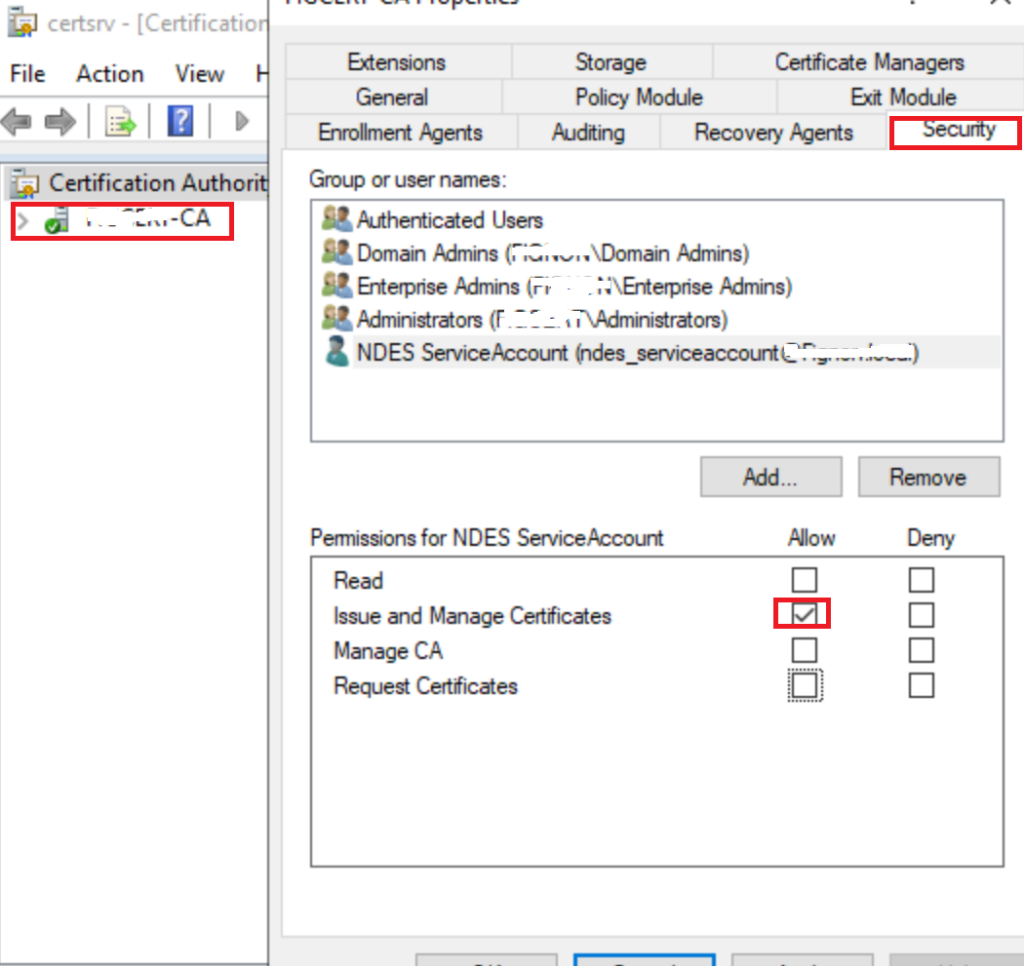
Certificate Revocation
If you want Intune to be able to revoke certificates you need to give the service account access to do this on your Internal PKI Certificate Server
Right Click your Cert Authority > Properties > Security and Add your NDES Service Account Issue and Manage Certs Right
Extra Security
On the CEP Encryption and IPSEC (Offline Request) Certs you you can remove the NDES service account Rights, Important though you will need the rights added again if you renew these at expiry and another important note do not remove these rights from the NDES Certificate
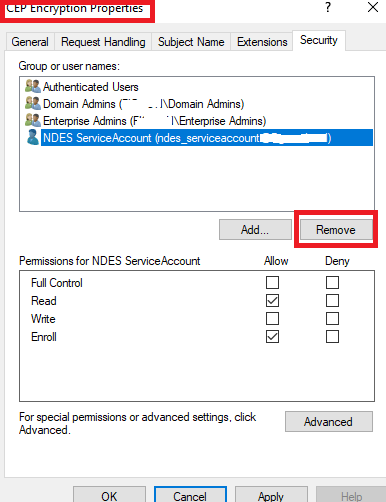
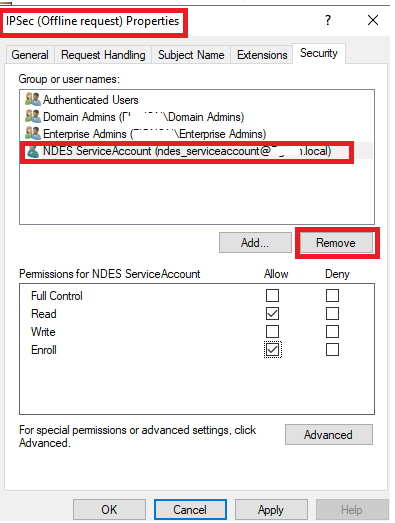
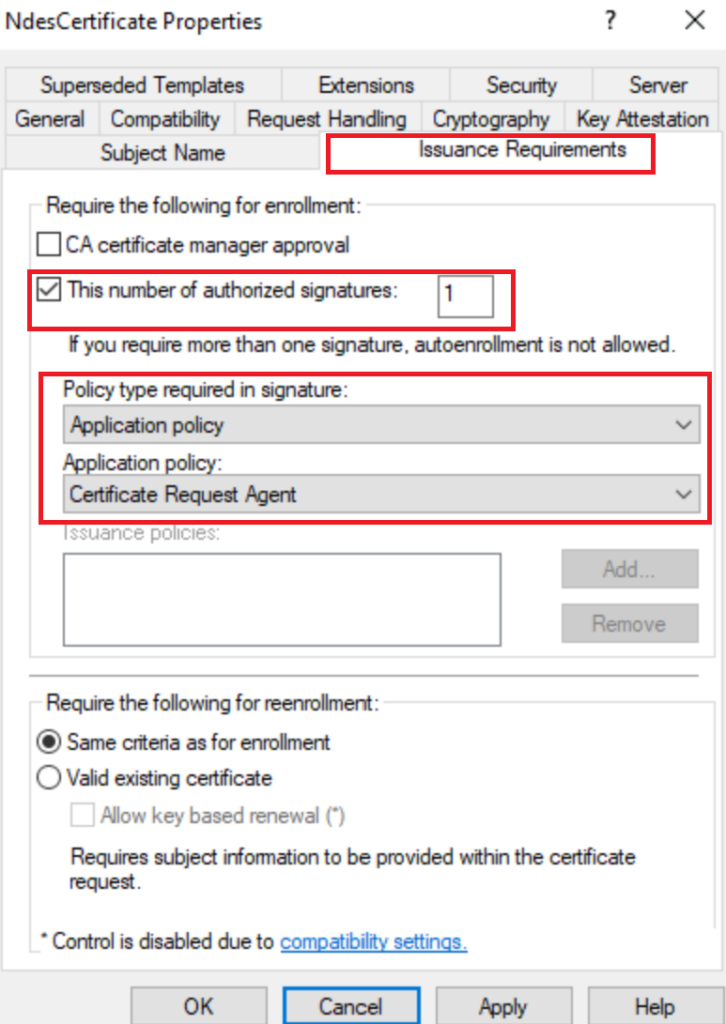
It’s best security practice to add this issuance requirement into your NDES Certificate Template
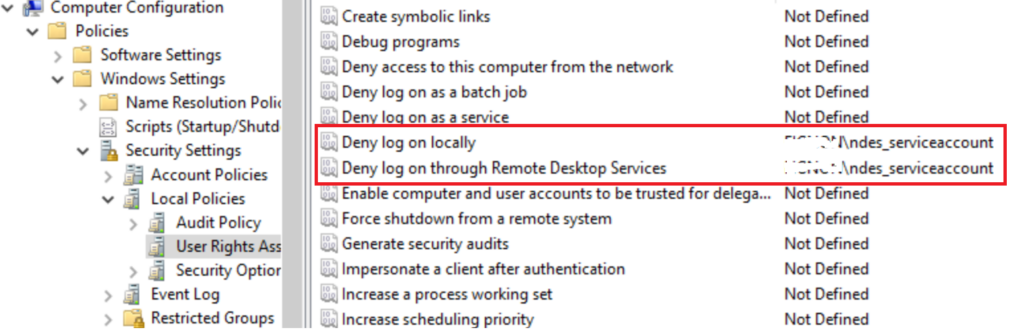
Optionally you can set these in Group policy or locally Secpol.msc
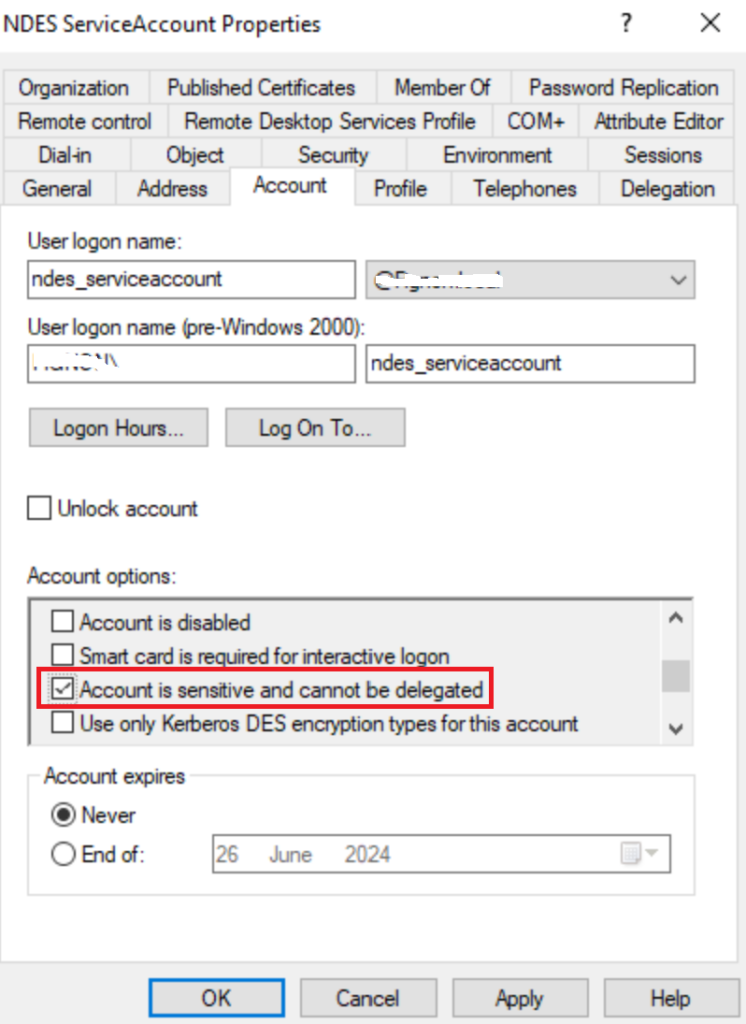
Enable Account is Sensitive and cannot be delegated
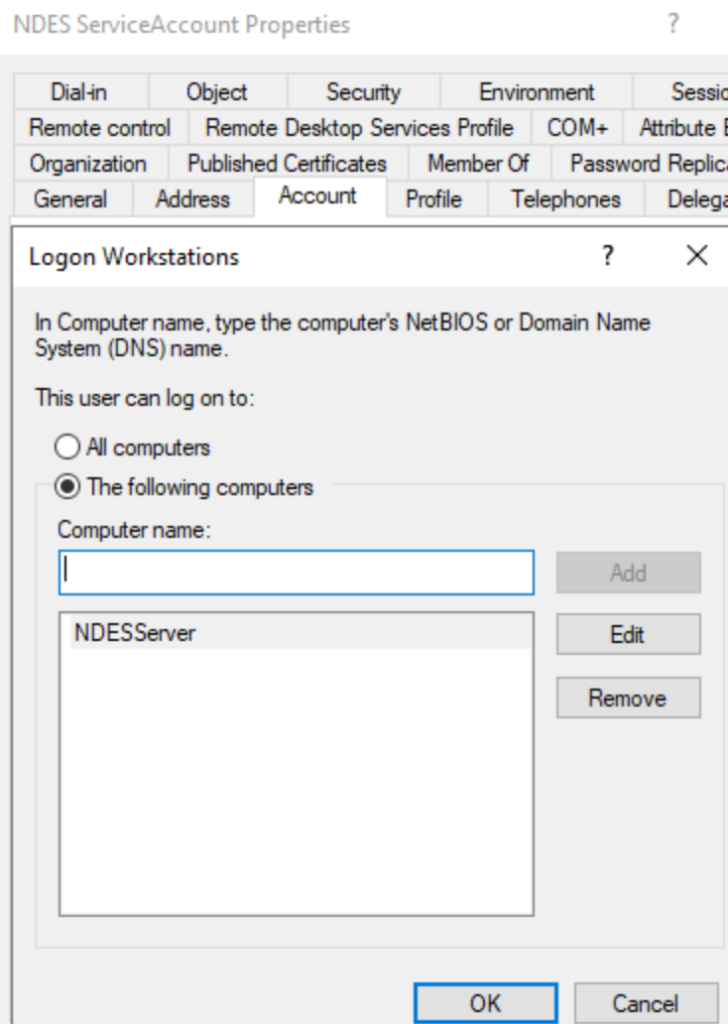
Only allow logon to your Intune Connector Servers
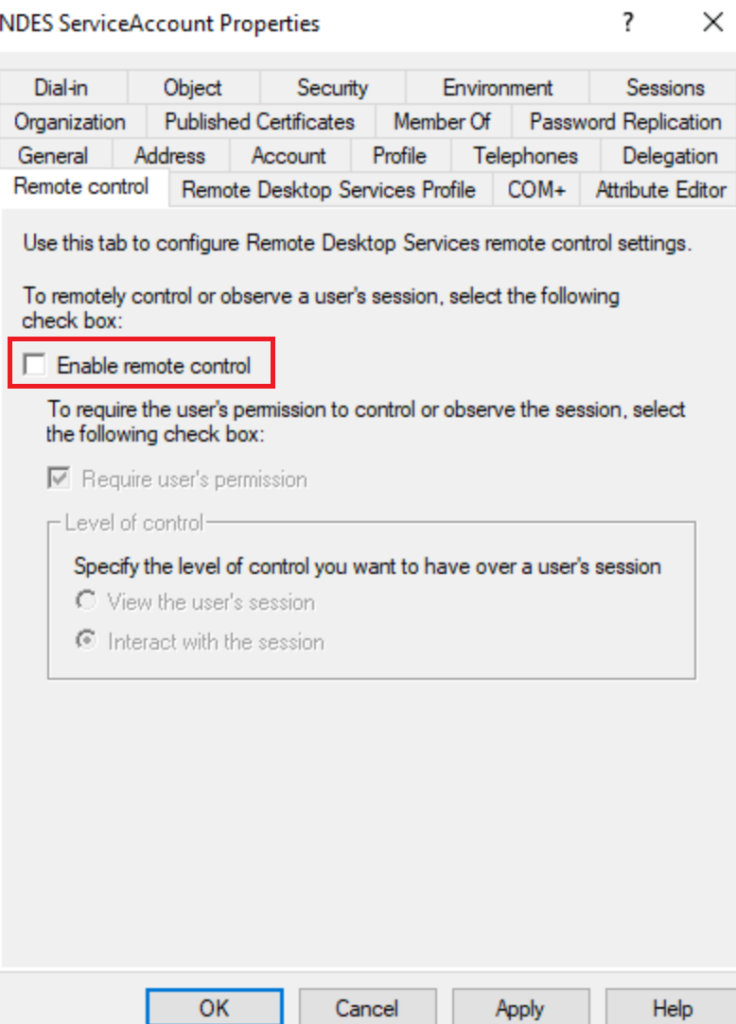
Disable Remote Control
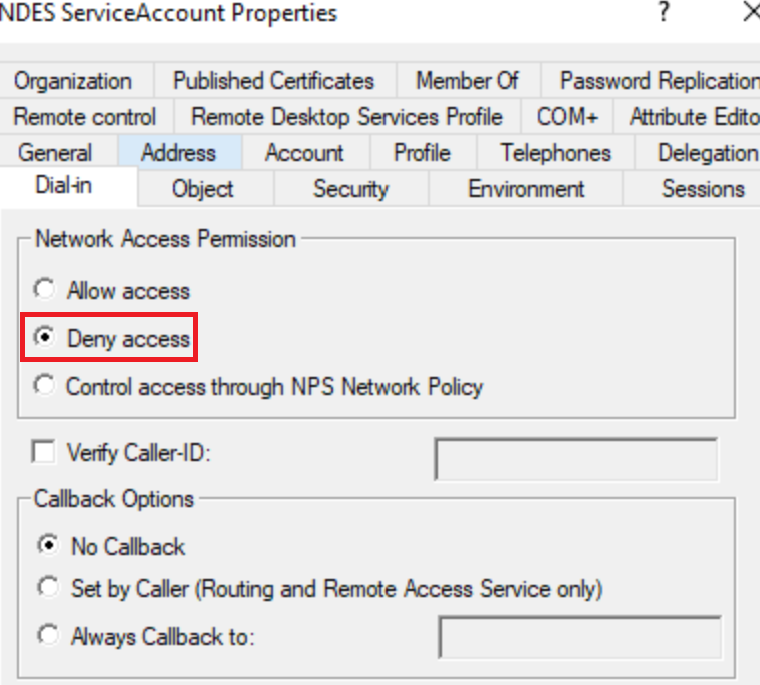
Deny Dial in Access
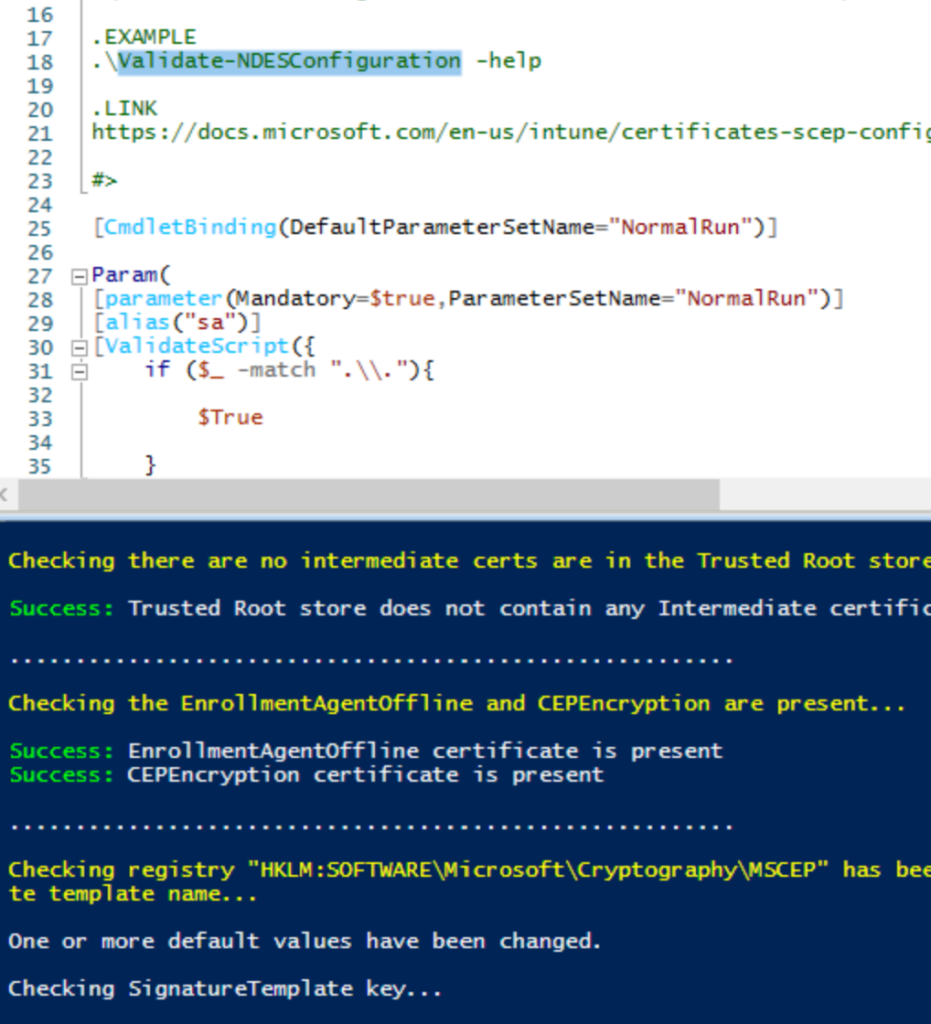
Useful Tools and references
Validate-NdesConfiguration is a very useful tool that goes through a complete check of all the components that should be present for NDES to work
You can download it here https://github.com/microsoftgraph/powershell-intune-samples/blob/master/CertificationAuthority/Validate-NDESConfiguration.ps1
Main NDES Config Page at Microsoft
Renewal when certs are expiring
This guide is invaluable when your NDES Server certs are coming up for renewal
How to renew NDES service certificates for usage with Microsoft Intune – MSEndpointMgr
One thing to note is that you do need to give the NDES server rights to Enroll to the CEP certs on renewal, you can always add enroll rights and remove again

Hi Tim,
we have this set up and our clients and users are getting the certificates BUT our machine and user wifi policy always gives the error that no certificates are present/usable when connecting.
When checking both certs are present on machine
OK, I think the most likely issue is the type of certificate that your Wifi Profile is looking for to be able to authenticate.
For example it may be requiring that a Subject Alternative Name (DNS Name) is present in the Certificate if so you can add this to the Intune Certificate Profile
Intune cert Profile
Which in the Computer cert profile would be under Attributes add {{AzureADDeviceId}}.domain.com where domain.com is your fqdn
I’m pretty sure this is the very likely cause just something around what certificate your wifi infrastructure is asking for to accept connection.
What wifi are you using? as in is it Cisco or are you using Microsoft Radius to allow connections?
Only other thing is, I presume when you double click on the certificate and got to the Certification path tab you have a root CA cert that it leads back to?
@R. Brik These posts here are quite similar, and again its down to what profile you have on your Wifi i.e is it set to allow a certain type of cert
https://www.reddit.com/r/Intune/comments/16rh680/wifi_setup_help_scepnpsaad/
https://www.reddit.com/r/Intune/comments/1aw9vko/new_blog_post_how_to_configure_certificatebased/
Thank’s for this tutorial.
I’m stuck at the step where you set up the proxy…
I’ve got a timeout error, I don’t really know why :/
I can acces the http://myndesserver.fqdn/certsrv/mscep/mscep.dll but not through the proxy… Any guess?
The error:
GatewayTimeout:
This corporate app can’t be accessed right now.
Please try again later…
Next Steps
The connector has timed out.
Great guide. Exactly like I did it multiple times. Unfortunately it seems, this doesn’t work on Windows Server 2025 right now. Any idea why and how to resolve this?